Just by rewriting the program code of 'macOS High Sierra', we found out the existence of zero day vulnerability that can be hacked using 'invisible click'
It was announced that a new vulnerability exists on the Mac where macOS High Sierra is installed. When this vulnerability is exploited, malicious applications will be able to click on objects on the screen without user involvement.
macOS Zero-Day Flaw Lets Hackers Bypass Security Using Invisible Mouse-Clicks
https://thehackernews.com/2018/08/macos-mouse-click-hack.html
This vulnerability was announced at a security related conference DEF CON 26 by former NSA (US National Security Agency) hacker, Patrick Wardle, lead senior researcher at Digita Security. The content of the vulnerability is that a malicious application can execute an operation which the actual user does not intend by misusing the accessibility function prepared for the disabled person , Mr. Wardle points out that it is a very dangerous zero day vulnerability .
Mr. Wardle talks about an actual problem as an example as follows.
"Do you want to run untrusted applications with just one click with several security mechanisms completely bypass? Do you want to approve access to the keychain? Click. Third party kernel Do you want to load the extension? Click Do you approve the external network connection? Click. "
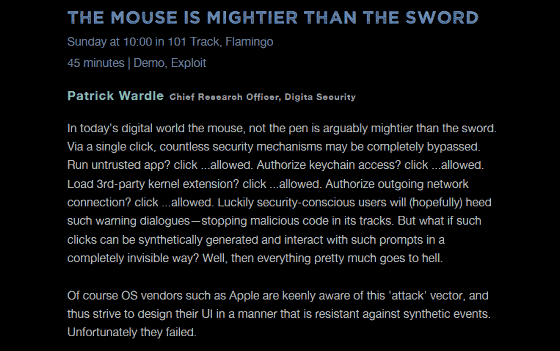
Mr. Wardle made a presentation in DEF CON 26, whose title was "The Mouse is Mightier than the Sword" (the mouse is stronger than the sword).
DEF CON® 26 Hacking Conference Speakers
https://www.defcon.org/html/defcon-26/dc-26-speakers.html#Wardle2
Mr. Mr. Wardle clarified what she said as "synthetic interaction" using the user interface, and by doing a "synthetic click" that the computer program can not see in the eyes, the operation which is not intended by the user It will be possible to be executed automatically without knowing it. As mentioned earlier, behind it there is an "accessibility" feature that Apple has prepared, but of course Apple has provided a variety of barriers to prevent this feature from being exploited.
But Mr. Wardle found that High Sierra incorrectly interprets two consecutive "synthetic click" events as "actual click". If this problem is exploited, it means that an attacker can use the program to respond to security warnings or to approve access to highly confidential data.

By Tim Franklin Photography
Mr. Wardle came across this problem by chance while copying and pasting the code. Mr. Wardle does not make clear the details of the actual problem, but he seems to be able to use the vulnerability by slightly adding two lines of High Sierra's code. Unlike when he discovered the problem earlier, Mr. Wardle did not report this to Apple, he said he opted to announce at DEF CON 26.
In addition, the next version of macOS "Mojave" contains measures to eliminate threats by blocking synthetic events.
Related Posts:







