Obviously it is possible to hack PC via subtitle file

BySimon Doggett
Subtitles who say "watching foreign movies with subtitles"60%There are also many people who watch movies with subtitles as there are more questionnaire results. However, if you are watching subtitle movies on a PC or the like, security researchers have pointed out the possibility that PCs will be hacked via files that read subtitles.
Hacked in Translation - from Subtitles to Complete Takeover | Check Point Blog
http://blog.checkpoint.com/2017/05/23/hacked-in-translation/
Beware! Subtitle Files Can Hack Your Computer While You're Enjoying Movies
http://thehackernews.com/2017/05/movie-subtitles-malware.html

Software development companyCheck PointA security researcher working at the company found a common vulnerability in four popular media player software. This vulnerability could endanger your device if malicious code is inserted in the subtitle file, whether PC, smart TV or mobile terminal.
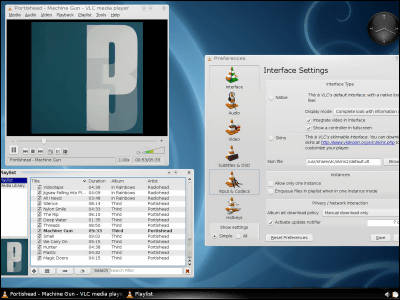
"Four popular media player applications"VLC·Kodi(XBMC)Popcorn Time·StremioFour of them. These four applications have been downloaded over 220 million times in total.
ByPanagiotis Giannakopoulos
The detected vulnerability is based on the processing method of the subtitle file of the media player, and it seems that there is a possibility that hundreds of hundreds of users in the world may be hacked if this is exploited. When a media player analyzes a malicious subtitle file and displays subtitles on the screen, it is possible to completely hijack the operation of that computer or smart TV.
A movie that shows how to actually hack PC using subtitle files has also been released.
Hacked in Translation Demo - YouTube
First of all, from hacking PC via subtitle file of Popcorn Time.
The screen shown on the screen is the screen of the victim who is trying to watch the movie using Popcorn Time.
Activate Popcorn Time and play your favorite movie.

When the movie starts, select subtitles.

Then "Malicious Subtitles Loaded" is displayed on the screen ... ...

The screen on the left is the screen on the browser of the victim's PC and the screen on the right is the screen on the attacker's side. When you select subtitles, connection between the attacker and the victim's PC is done ... ....

The hijacking of the PC has been completed before Cinderella Castle and the logo disappears that are played before the main part of the Disney movie.

Then hack the PC with "Kodi".

In the same way the victim will play the movie with Kodi.

It is the movie "Snowden"is.

The movie started ......

First, select subtitles.

In the case of Kodi, multiple choices are displayed, but the top three are prepared as "malicious subtitle file".

If one of these is chosen, the connection between the attacker and the victim's PC has started as in the case of Popcorn Time ......

It takes away control of the PC in no time.

Subtitle files of movies and TV programs are created by writers, etc., and the world's largest free subtitle database "OpenSubtitles"And free subtitle database"SubDBSince it is uploaded to, etc., there is a good possibility that the file containing malicious code is misunderstood in the normal subtitle file. Also, by manipulating the ranking algorithm of these subtitle file sharing sites, it is also possible to direct malicious subtitle files to be displayed in places where users can easily see.

Check Point estimates that media players with similar vulnerabilities exist in addition to the four applications listed here. Also, Check Point reports information on vulnerabilities to developers of each application, and developers have not revealed technical details at the moment in order to secure time to deal with vulnerabilities Thing.
Stremio is a modified versionStremio 4.0 beta, And VLC has announced the release of VLC 2.2.5 which will be the latest version within two weeks. Also, Kodi is planning to release the modified version of version 17.2 this weekend,Available from hereAnd that. In addition, Popcorn Time alsopatchIt is probably good to update users who are using one of these applications as soon as possible.
Related Posts: