Emergency patches will be released for remotely operated vulnerabilities in Intel 's CPU that appeared in the last decade
A bug in the remote management function included in the CPU of the 1st generation Core processor and later revealed that there is a risk that the computer may be controlled completely remotely, and on May 1, 2017 Intel repaired the vulnerability I released an urgent patch.
Intel® Product Security Center
https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00075&languageid=en-fr
Intel patches remote code - execution bug that lurked in chips for 10 years | Ars Technica
https://arstechnica.com/security/2017/05/intel-patches-remote-code-execution-bug-that-lurked-in-cpus-for-10-years/
According to Intel, this vulnerability ranges from the first generation (Nehalem) to the seventh generation (Kaby Lake) of Intel Core processors, Intel manageability (Intel Standard) in Intel Active Management Technology (AMT), Intel Standard Manageability (ISM), Small Business Technology The version of firmware is included in 11.6 machines from 6, and it is an attacker who does not have authority to allow attacks via local or network. Intel has set the severity to "Critical" and strongly recommends updating to the latest firmware with the vulnerability corrected. In addition, announced according to InteVulnerability does not exist on consumer PCAnd that.
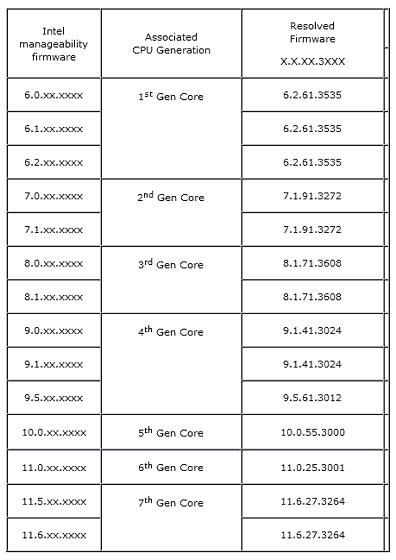
According to Ars Technica, initially when vulnerabilities were announced from Intel, security experts say "All Intel platforms from Nehalem to Kaby Lake are attacked"EvaluationHowever, researchers who analyzed Intel 's data believe that there is a danger of being exploited on the network only when Intel' s AMT service is enabled and set to be trialable in the network And that. Also, "Only when Windows-based software known as Local Manageability Service is running, attackers can attack attacks by unauthorized attackers over the network, so the hurdles imposed on attackers are quite high," thinkingresearcherIt seems to be also.
According to Mr. Moore, vice president of Research and Development at Atredis Partners, it is affected on the server on which the LMS service is running, with less than 7,000 of the open ports "16992" or "16993" opened The server is detected. Mr. Moore says that tens of thousands of PCs can be connected to these servers, Mr. Moore said that it is potentially a big threat, and companies with LMS and AMT enabled on the network prefer patch-enabled firmware first I warn you that it should be installed in a similar way.
Related Posts:






