In the 1980's the Soviet Union was spying on American information by hacking typewriters

ByRalf St.
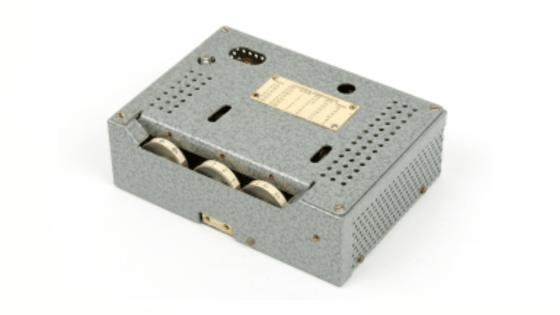
Confidential material of CIA Wikileaks announced on March 7, 2017 "Vault 7"Although a spy method such as hacking smart TV in the other room's room and tapping all contents of the conversation was written, the methodology of dive secretly jumping into the other's pocket and pulling out information once was It is one of the classical methods used since the Cold War era. At that time the USSR was confronted with the US Soviet employing a method of intercepting the document to be created in real time by sneaking in a special device to the typewriter used at the American Embassy.
Forget Smart TVs: Russian spies hacked typewriters in the 1980s - Quartz
https://qz.com/932448/forget-smart-tvs-in-the-1980s-spies-were-hacking-typewriters/
The method of CIA's "hacking smart TV made by Samsung, secretly turning on microphone and gathering surrounding sound" is a way to symbolize the era of "IoT (Internet of goods)" However, it is clear that similar ideas were incorporated in national-level intelligence activities in the 1980s. American NSA (National Security AgencyAccording to the data published in 2012, the Soviet Union (Soviet Union) in the midst of the 1980's East-West Cold War concealed a special device to the typewriter used at the American Embassy and detected the entered key The contents of the document created in secret was acquired.

Originally it was unknown how the information was pulled out but it was information from the embassy of the detailed nondisclosure "country close to the United States" that first noticed that existence Thing. The NSA who got the information analyzes the equipment and reaches the recognition that it is "the technological development of the Soviet Union" as a high level of its technical capabilities. I heard that the initial device was not used for typewriters, but it seems that NSA has reached the conclusion that the device will be used near some kind of electronic equipment.
After that, the US succeeded in collecting the actual equipment for the first time. Until then it was America that was stepping on a small microphone hidden in the lights and walls, but you will notice the existence of a device that you do not expect. In the NSA's report, "The development of such a device requires a lot of personnel, time and budget, and it requires a grand, modern facility operated by many people in production. Then, there are possibilities that more devices are being used ", it was predicted that devices were widely used.
In response to the situation, the US government instantly negotiated the response, recognizing that the Soviet Union possesses such technology and recognizing that the US Embassy in Moscow is the largest target, the NSA We have launched "Project · Gunman" to investigate the whole picture. The first thing I did was to thoroughly investigate the electronics used in the embassy. However, in order to proceed with the investigation without noticing this project on the partner side, we can not disassemble the equipment at all. Therefore, the US side adopted a method of investigating the inside of the machine using X-ray equipment. Not only typewriters but also other types such as teletype machines, printing machines, computers, cryptographic machines, copy machines, etc., were the subjects that were investigated on the scale of "everything powered by the wall outlet" It is said that it was advanced.

The ultimate goal was to collect and replace the unit without being noticed by the Soviet Union and to bring it to the US. However, for the convenience that it can not be felt by the Soviet Union, it seems that it was impossible to introduce experts in the investigation, so to speak, an amateur operates various equipments and analyzes the equipment. For that reason, it seems that it seems quite time that the investigation could not proceed.
In the survey using X-ray equipment, the technique of shooting and comparing the equipment actually used and the same type of equipment was adopted. For days, I shoot the equipment and compare it, and the days that I can not find anything in the end continue. However, IBM's electric typewriter "Selectric", It turned out that a small coil was attached near the power switch. The staff who was in charge of the investigation told that time, "When I compare X-rays, I told you" holy fuck. "It's really a bug in our equipment I was very excited, but there was no one around us who could talk about it, my wife was also an NSA official, but to tell my wife that the confidential level is different I could not even do it. "

With this discovery, the pace of the survey dramatically improved. According to an investigator who discovered a bug, "We had investigated all typewriters of the embassy because there was a possibility that bugs were hidden in other typewriters, We also reported this content to the US Embassy officials and asked us to investigate whether similar bugs were installed.We reversely engineer this device so that information can be extracted through what kind of mechanism We started investigation as to whether there is something wrong. "
Eventually NSA finds that there are five types of power budgets and different component configurations in this bug. Also, the mechanism by which these devices operate is the change of the magnetic force generated when the key of the typewriter is pushedMagnetometer, And by sending the information to a receiver that is put in the vicinity by placing the information on radio waves, it is possible to grasp in real time which key is pressed and what kind of document is being created I found out that I found out.
Now that the world is connected by the Internet, in many cases it is possible to intelligently activate the smart TV secretly by turning on the microphone, for example, by operating it remotely. On the other hand, in the Cold War era in which most of the equipment was running in analog, it is quite interesting to see how this device was sneaked into the equipment of the partner country. But what is surprising is that there is no fundamental difference in the method of obtaining information even now and still, it is noticed that "I jump in secretly into the other's pocket and pull out the information". And while doing this now, there should be similar intelligence activities around the world.
Related Posts: