Playing video advertisement 300 million times a day to earn about 600 million yen Russian-origin hacker's new attack "Methbot"

ByBlogtrepreneur
By hacking the mechanism of Internet advertisement and automatically playing back advertisement videos, it is unlikely that in the past fraud system which is illegally earning income of 600 million yen a dayMethbot"Is clear from the follow-up survey by security affiliate" White Ops ".
Methbot | White Ops
http://www.whiteops.com/methbot
'Biggest Ad Fraud Ever': Hackers Make $ 5 M A Day By Faking 300 M Video Views
http://www.forbes.com/sites/thomasbrewster/2016/12/20/methbot-biggest-ad-fraud-busted/#6b1439514ca8
To put it briefly into the structure of Methbot, "By using bot, we can reproduce 300 billion times more video advertisements that can earn high profit, and advertising revenue from advertisers is 600 million yen a day It is said that it is a mechanism that raises near too. However, simply "letting bot play advertisement video" should not get advertisement revenue, but hacker's group has succeeded in breaking through the barrier of defense by using skillful methods Thing.
A detailed investigation of White Ops has revealed that Methbot is a system that is precisely designed by a group named "Ad Fraud Komanda" or "AFK 13" based in Russia. First, AFK 13 creates more than 6000 Internet domains and 252,67 URLs, and disguises them as if they are related to prominent companies. Although the camouflaged companies are big names such as the American broadcasting station "ESPN" and the famous brand "Vogue", it is said that only the video advertisement is displayed on the page where the URL was actually opened about.
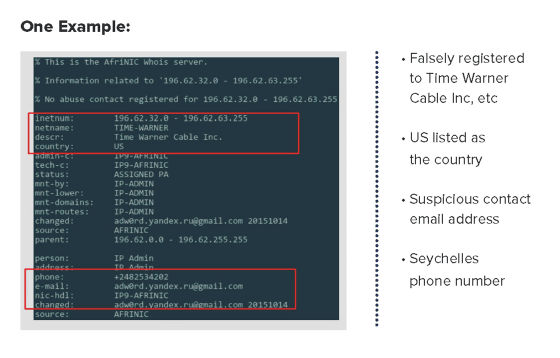
In the image below, it is possible to check information on the domain that Methbot is impersonating. It is registered illegally under the name of "Time Warner Cable Inc." and its location is the United States, but it is obviously funny that the mail address is free e-mail or the telephone number is the country code of Seychelles You can see that it is understood information.
In addition, AFK 13 has adopted a mechanism to disturb the advertisement insertion algorithm by performing fake domain information, and to attract more profitable advertisement contents to its site. Although this algorithm is normally a mechanism that determines the publication fee by bidding, AFK 13 raises the unit price by pretending that the advertisement space of the site prepared for fraud is purchased by a large company It is seen as being there.
In addition, AFK 13 "invests" the server that runs the bot and runs over 570,000 bots to generate traffic to the site. And with that bot, AFK 13 displays and plays video advertisements 300 million times a day, generating average revenue of 13.04 dollars (about 1500 yen) per view.
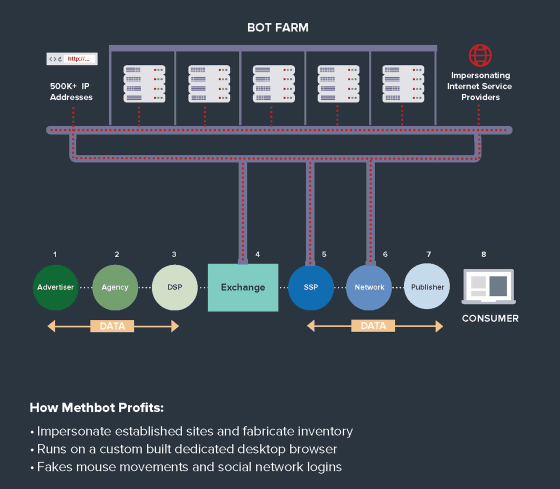
In doing so, AFK 13 uses a proprietary browser developed exclusively, bot acts like mouse operation and click, further disguising the history of SNS, it is as if the actual human being browsed It is making a situation as if it is in the way that it is taking measures to prevent the advertisement system from being realized as bot.
In White Ops, we have been tracking this fraud system since September 2015. Initially, it seems that Methbot has been noticed because of suspicious traffic going to its customer's network, but it seems that until that time of October 2016 that much extensive activity had not been done. Eddie Schwartz, COO of White Ops, said that while the company's method hides himself to avoid being aware of it, he said, "The group involved in fraud is based in Russia and is a single organization There is no doubt about something, we are working with law enforcement agencies in the US for several weeks, "he said, stating that it is a policy to take legal measures.
In addition, White Ops shows a policy to deal with situations where Internet advertisements are exploited on a large scale at an unspecified level in the past. At the same time as doing work with law enforcement agencies as described above, "From the historical point of view, it is very difficult to get Russian cooperation in pursuing cybercrime," Mr. Schwartz said in a survey Detailed information such as domain for fraud and IP addresswebsiteWe are strengthening the work to stop the damage by making it public by.
Related Posts:
in Security, Posted by darkhorse_log