Vulnerability to intercept communications that should be protected by HTTPS "Forbidden Attack" can be used in multiple sites such as VISA related sites

BySean MacEntee
Financial services giantVISAOwned byHTTPSIt has been revealed that websites that are protected by them are vulnerable to specific code.
"Forbidden attack" makes dozens of HTTPS Visa sites vulnerable to tampering | Ars Technica
http://arstechnica.com/security/2016/05/faulty-https-settings-leave-dozens-of-visa-sites-vulnerable-to-forgery-attacks/
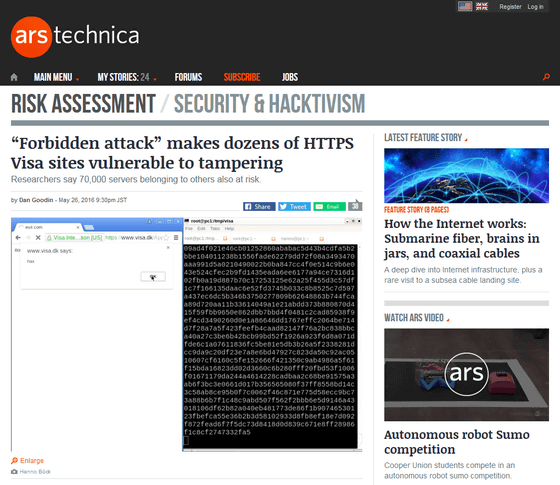
It is a German stock exchangeDeutsche BorseAnd the bank association of PolandZBPIncluding 184 servers, including 10 years of vulnerabilityNational Institute of Standards and TechnologyIt was clarified by investigation. This vulnerability is called "Forbidden Attack" by cryptographic experts. Although it seems there is a danger of being attacked similar to 'forbidden attack' even with more than 70,000 web servers, it is also clear that it is extremely difficult to carry out this.
The existence of 'forbidden attack' was revealed in January 2016, after which Deutsche Borse has taken measures against 'forbidden attack' on the website. However, VISA related sites and ZBP are still vulnerable, and there is a risk of being attacked.

ByBlondinrikard Fröberg
Websites that are countless on the Internet are constructed with markup language HTML, but the communication protocol for sending and receiving this HTML data between the web server and the web browser is "HTTP"is. In order to make the communication by HTTP more secure, communication dataSSLIt is "HTTPS" to encrypt using TLS (TLS).
"Forbidden Attack" is a vulnerability that occurs when HTTPS "TLS Protocol" is executed, "It reuses encryption to incorrectly encrypt data". TLS encryptionGCMAlthough it adopts the cryptographic use mode of, it is only one time that arbitrary encryption is used. However, if you send a request of 2 to the 30 th power to a vulnerable HTTPS server, the encryption will be reused with a probability of 3%, so that the encryption is released to a malicious hacker or the like and HTTPS There is a danger that communication contents that should have been encrypted are intercepted. However, it seems necessary to send several terabytes of requests to the server to do this attack.
ByChristiaan Colen
Moreover, there is a possibility that communication may be intercepted,Man-in-the-middle attackIt is also suggested that hackers who have set up for malicious content may get mixed. People who can bypass encryption using "Forbidden Attack" can also steal confidential information such as passwords and personal information entered by users of website by misleading malicious JavaScript code, And that.
The following movie contains a state of using "forbidden attack" to bypass the HTTPS of the VISA related site.
Proof of concept of GCM nonce reuse attack against visa.dk - YouTube
For details on "Forbidden Attack", please visit the Security Conference to be held in Las Vegas, USA from 30th July to 2nd August 2016Black HatIt will be announced in.
Related Posts:
in Security, Posted by logu_ii