Six cryptanalysis tests to determine if there is a brain that can be cyber security
In the past, British military had introduced thought tests using crosswords and puzzles in order to find people with decryption ability to decipher the codes and ciphers used by German military during World War II That's right. In contemporary society, cryptanalysis problem is adopted as a brain test to find the owner of the capability appropriate for "cyber security" to prevent cybercrime or deal with actual attack.
Do you have the brains for cybersecurity? - BBC News
http://www.bbc.com/news/technology-34312697
Fostering cyber security that can cope with cyber attacks has become a major challenge for each country in the world. In the UK nationwide brain test to distinguish whether there is an element of cyber securityCyber Security ChallengeHas been utilized. Whether we have a brain that is suitable for cyber security can be understood by solving the following six tests.
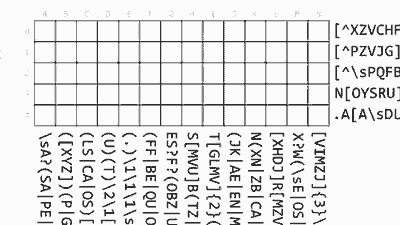
◆ Challenge 1
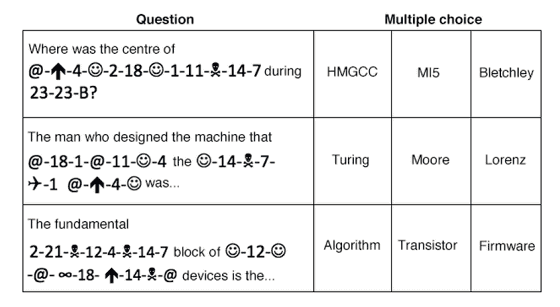
The first problem is a cryptanalysis sentence that solves the problem using the code table below.

The question (Question) is 3 styles, the style to answer from all three choices (Multiple choice). For example, replacing the first question using the code table will result in "Where was the center of" CODE BREAKING "during" WW 2 "? (Where was the corruption center in World War II?)" The correct answer is "Bletchley", if you can solve it as feeling OK.
◆ Challenge 2
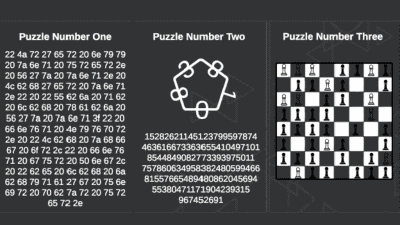
The next problem is to read the code name of famous mathematics from the character string "5 8 1 14 14 0 2 2 8 18 4 16 20 4 13 2 4". An image of a bee that caught sunflowers under the number is given as a hint.

◆ Challenge 3
Julius CaesarHowever, as ciphertext is used to send a secret message to the military, decryption was being actively done in the days of the Roman Empire. In the ciphertext "X S K L V V O H H Y L H V" below, the place where Caesar hid the army is hidden.

◆ Challenge 4
The challenge 4 cipher text looks something like this. It is written with symbols that are not letters or numbers, and the work of decrypting the encryption becomes more tricky. If deciphering succeeds, a famous person name appears as a decryption technique.

◆ Challenge 5
Challenge 5 is a problem of deciphering sentences consisting of numerous figures as follows. A questionnaire appears if it can be deciphered, so if you can reply to it, the problem will be cleared.

This image is a hint. It looks like a chemical period table.

◆ Challenge 6
The final question is to solve three puzzles and find quotes of famous works. It seems that each puzzle is an independent problem.

Because cyber security work requires the ability to find the optimal solution in the imperfect knowledge to solve the problem that is occurring, people with high ability to decrypt cryptosync He said that he is suitable for his job. The answers to these six problems are:BBC NewsIt is scheduled to be announced at the end of March 2016.
Related Posts:
in Note, Posted by darkhorse_log