What kind of information can ISP obtain about us?

ByMatthew
Although we use the Internet as usual, such as net search, map display, viewing of movies, etc., it is not only the user himself / herself as to "how to use the Internet" but actually the Internet You can also grasp the service provider (ISP). A paper by Peter Swire, a researcher of the privacy law which investigated about what kind of information and how much ISP can obtain?UpturnI explain it in an easy-to-understand manner.
What ISPs Can See
https://www.teamupturn.com/reports/2016/what-isps-can-see
01: From the Internet as a whole, encryption has not been done yet

ByMinisterio TIC Colombia
Today, HTTP is used on many websites, but if the website is HTTP, ISP can identify what kind of content the user requested and which URL was visited.
To avoid the above situation, some sites with high traffic and popular sites do encryption on the website. At this time, looking at the encrypted contents and the unencrypted contents with the entire traffic on the Internet as the denominator, considerable contents are encrypted, and by the end of 2016, 70% It is predicted that it will be encrypted. However, 35% of downstream traffic in North America is Netflix's content. Comparing the traffic when looking at one movie and the traffic volume when searching on the Internet may be close to 20,000 times, there is a limit to see the tendency of the whole encryption only by comparing traffic volume There is.
In addition, 86% of the health field, 90% of the news, shopping 86% of the websites were found to be unencrypted. Speaking of the health field, symptoms of specific diseases are displayed in the search result, and the information is not protected despite being greatly involved in personal information, ISP is a website URL of a website searched by a specific user And what content is included in the web page.
On the other hand, for website administrators relying on third parties such as advertising, analytics, embedded movies, etc., encrypted from unencrypted HTTPHTTPSThe transition to importance is important. Third-party partners need to support HTTPS to encrypt websites, but in 2015 survey targeting 2156 online advertising services, 85% of advertising services are HTTPS It has been found that it is not adopting, and realization is considered to be very difficult.
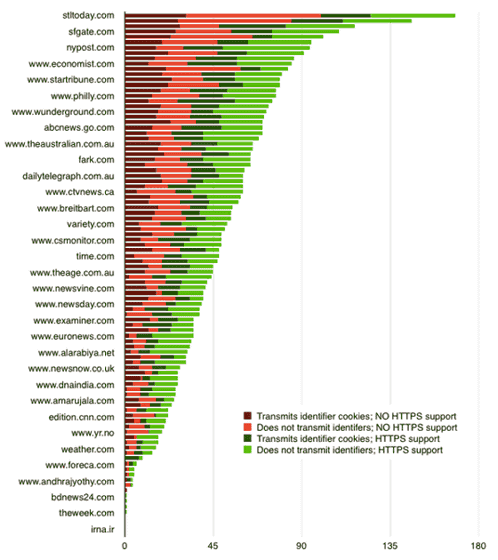
Check the access status of the web pageRank pages with a large number of visitorsThe graph below shows how much the advertisement service used by the news site entering the top 100 Web site "Alexa" is encrypted. If the news site wants to ensure safety for the reader, it means that all the red graphs are green, or it is necessary to cut off partners corresponding to the red graph.
Also, IoT (Mono's Internet) is also one of those that failed to encrypt. Researchers are using "smart fire alarm"Nest Protect"And digital photo stands"Pix-star"We found out that many devices are accessing the Internet without being encrypted.
02: ISP can check the domain of website visited by Internet users even if using HTTPS

ByAtomic Taco
By encryption, the ISP will not be able to check the details of the URL visited by the Internet users or the contents of the content, but even if you adopt HTTPS, you can check the domain visited by the user.DNSThis is because queries are hardly encrypted.
Because Internet users themselves send queries to ISPs when browsing, the act of "I collect information using DNS queries" is actually a possibility and costs less for ISPs. Using the latest tools it is also easy to record requests sent by Internet users for later analysis. Also, even if the user's computer is using a DNS server other than ISP, DNS queries may arrive from an unencrypted external server to the ISP's server and be censored.
In fact, ISP monitors DNS queries of users to prevent infection of malicious malware. It was also found in a survey in 2011 that several small ISPs are analyzing DNS query information under the name "for network management". Of course there is currently no evidence that a major ISP gathers DNS queries and is violating privacy. At the moment, "Today's technology is up to the point that ISP can monitor DNS queries and interfere with DNS queries".
Also, the list of which domain a user visited includes even very short information, even if it is short. Looking at the information below it is because the user knows that he is going to a hospital or facility due to abortion.
[2015/03/09 18: 34: 44] abortionfacts.com (information site for abortion)
[2015/03/09 18: 35: 23] plannedparenthood.org (Healthcare Community website)
[2015/03/09 18: 42: 29] dcabortionfund.org (NPO website for providing abortion funds)
[2015/03/09 19: 0 2: 12] maps.google.com (Google Maps)
If you gather information for a long period of time, you can of course identify what interests users and what kind of hobbies they have. The state that the ISP can confirm the user's DNS query includes the possibility of further compromising the user's privacy from now on.
03: Information can be obtained without unencrypting

By* Sax
Encryption makes it impossible for the user to see the URL visited directly by the ISP, but as stated above, it still reveals a lot of information. In addition, information is accessed without invalidating direct encryptionSide channel attackThere are a number of methods called heuristics that are being crafted and it is said that some governments that censor the Internet actually use side-channel attacks.
For example, in the past research, we know that it is possible to identify the user who visited the website from combination of OS, browser type and plugin setting. In addition, by analyzing the list of words coming out from Google's forecast search, it is also possible for the user to derive the words that the user put in the search box, and by using a method similar to this, the user's medical condition and income , It is also possible to infer the investment target etc.
What you can see from the above is that the encrypted data can know the contents without knowing how to decrypt it. The same is true for ISPs, so you can know which URL the user visited, even if the encrypted website does not display the details of the URL.
Information leakage due to side channel attack is difficult to prevent and personal information may be infringed. Currently, there are many side-channel attacks that are still in the experimental stage and the research stage, but from the evolution of computer science, the day in reality may be close.
04: For privacy protectionVPNIt is rarely used

ByNASA's Earth Observatory
One way for users to protect their Internet traffic is to use VPN. VPN is mainly used by companies and makes it possible for employees at remote locations to access the company's internal network. One of the advantages is "Enable security by tunneling using VPN-specific protocols" There is something called. In his paper, Swire writes that "VPN is promising for the protection of the Internet", but as to whether or not VPN will be used in the future is questioned.
According to a survey conducted in 2014, 15% of North American Internet users are using VPN, and there are few people who routinely use to avoid monitoring ISPs . Many VPN users are using it on business, and there seems to be no one aiming to protect privacy.
In countries where censorship on the Internet such as Indonesia, Thailand and China is severe, there are a lot of people who use VPN for security improvement purposes, but it takes monthly to try to use secure and reliable VPN In addition to the increase in expenses, the communication speed is also slowing down has become a major obstacle.
However, using VPN reduces the possibility of checking URLs and domains of websites browsed by ISPs, but of course it can not protect privacy perfectly. Depending on VPN settings, protection may not be done properly, but it is difficult for amateurs to set up, and someone may need to ask about settings.
Although we are using the Internet as usual, we should always be aware that it contains very sensitive privacy information,UpturnConcludes that "People understand what ISP can do with this report and wish discussions on broadband privacy will happen."
Related Posts:
in Note, Posted by darkhorse_log