Vulnerability to be hijacked during flight to the drone such as "AR Drone 2" turned out

For aerial photographs in which real images can be takenThe brand name of drone (multicopter) gradually rises, such as things that can be bought at thousands of yen from a toy shop, but Parrot's one of the pioneers of such dronesAR Drone 2"There was vulnerability to be hijacked such as the manipulation was announced at the hacker event" DEFCON ".
Parrot drones easily taken down or hijacked, researchers demonstrate | Ars Technica
http://arstechnica.com/security/2015/08/parrot-drones-easily-taken-down-or-hijacked-researchers-demonstrate/
Among the "drones" that have risen in popularity as good or bad, "AR Drone 2" is the model that had high awareness in the early stages. Everyone can easily skip using smartphones and I was able to easily shoot the following images.
Everyone can easily shoot HD movies and iPhone / iPad become controllers Try shooting the sun tower with "AR Drone 2" - GIGAZINE

And the vulnerability clarified this time is that AR Drone 2 and its new model also at the companyBebop DroneIt is said that they are two models. In the following movie, there is a state of an experiment that crashes by invalidating the control of hovering AR Drone 2.
Planetzuda.com parrot drone hack from defcon 23 - YouTube
Pilot with AR Drone 2 on the ground with a connected smartphone.

The aircraft floated and floated and entered hovering. So far no normal problem condition.

I take control of the aircraft from here. First of all, put the smartphone you used for maneuvering in a place that you can not reach ... ....

Take control of radio waves with a PC. Although it can not distinguish the written character because the image is unclear, it seems that "Kill One" is displayed according to the man.
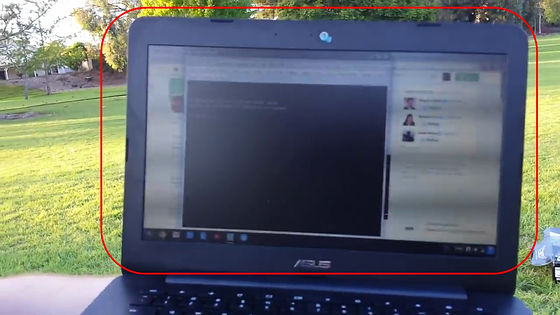
In this state, hit enter key ......

The propeller stopped and AR Drone 2 crashed to the ground with Stone. Although it crashed from a place not so high, it seems that it is not a calm thing if it thinks that this is a crash from a sky of several meters to several tens of meters.

This vulnerability is a security consultant'sPlanet ZudaIt is what made it clear. It is said that Wi-Fi is used for AR Drone 2 control, and the signal is not encrypted and SSID is not hidden. Although the detailed method is unknown, it seems that it is also possible to cancel the connection between the smartphone and AR Drone 2 and crash it, or take over the maneuver itself and skip it as it is.
In addition, the model such as "Phantom 3" sold by DJI does not use Wi-Fi for maneuvering, and similar problems are not confirmed because radio waves for radio control are used. Planet Zuda has already notified this issue to the selling Parrot, and what kind of measures Parrot will take is not announced at the time of writing the article.
Related Posts: