Check Twitter login history of yourself and see if it was compromised by unauthorized access "Twitter data" How to use Summary
ByScott Beale
"Twitter's dashboard function allows you to check your account history, history of accessed devices, login history, etc."Twitter data"Has been added. In order to confirm, you need to log in to Twitter on web version from the browser, but especially login history allows you to check the login status of the linked application, so you can quickly find hijacking and unauthorized access .
A new dashboard to help you monitor and manage your Twitter account | Twitter Blogs
https://blog.twitter.com/2015/a-new-dashboard-to-help-you-monitor-and-manage-your-twitter-account
To check using "Twitter data" function, first log in to your Twitter account. Open the web version of Twitter without using the application, click your icon on the top right of the page, and click "Settings".
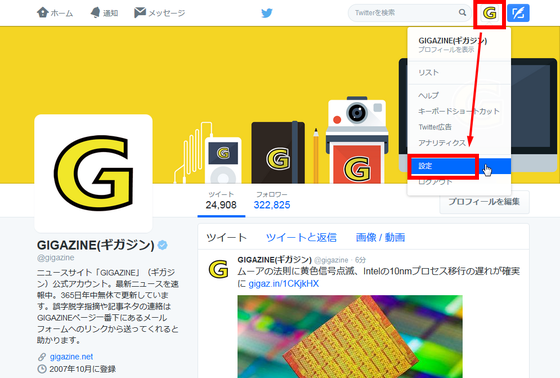
Click "Twitter data" displayed in the menu on the left side of the page.
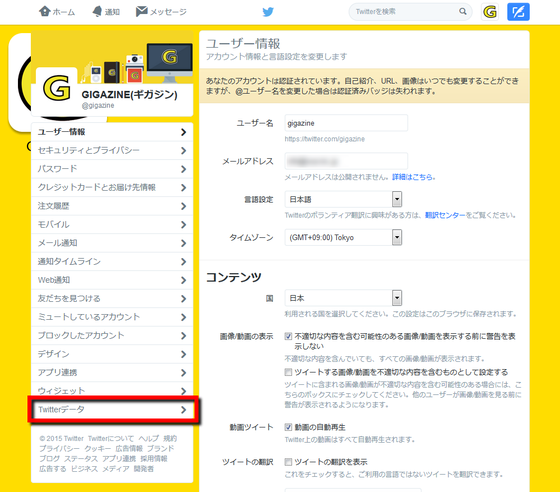
Then, you will be prompted for a password to access the page containing personal information. Enter your password and click "Confirm".
The page of Twitter data was displayed. It seems that it depends on user's usage, but it has become long and slickly long page.
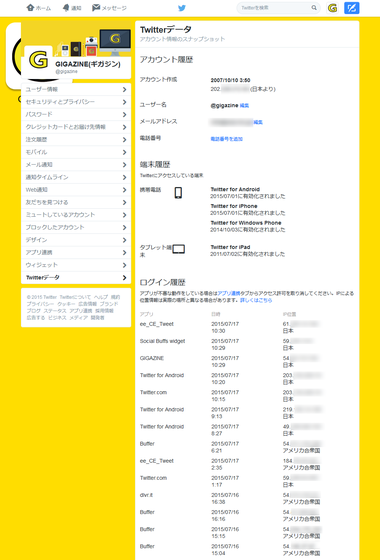
At the top of the page, basic information such as account creation date and time, location, user name and e-mail address are displayed, below which the type of terminal and application name that accessed the account are displayed.
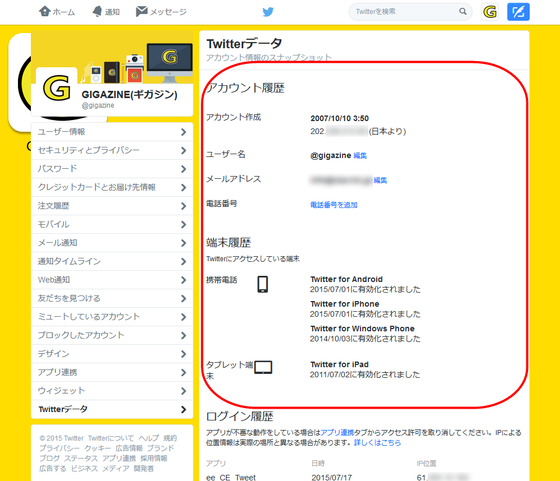
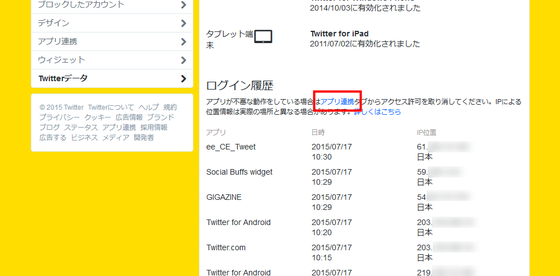
And below that, "login history" which is information effective for security is displayed. Here, since the name of the application that accessed the account, its date and time, IP address and location are displayed, it is possible to check whether there is an unauthorized login that I did not recognize.

If there is suspicious access from an unfamiliar application in the history, it is possible to shut out access by canceling cooperation between the application and Twitter. To set up, click "Application cooperation" near the item name "login history".
A list of applications linked with the account is displayed.
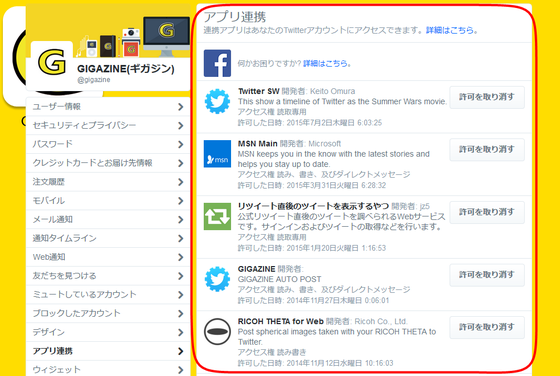
Once you can identify suspicious apps, you can shut down access by clicking "Cancel Permission" next to the name.
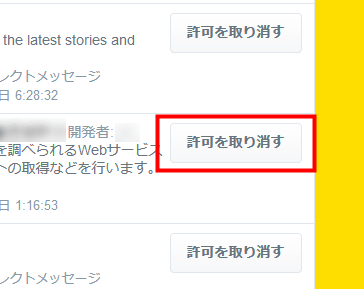
In this way, you can easily check the login history from web version Twitter. Think about what happened when an account was compromised, and in the sense that you remember the procedure, once it is confirmed it seems to be OK.
Related Posts:
in Web Service, Review, Posted by darkhorse_log