What is the hacker group's way to steal confidentiality from mail accounts and favor stock trading?

ByMerrill College of Journalism Press Releases
Securities and Exchange Commission(SEC) is investigating hacker groups suspected of breaking into corporate mail accounts and stealing confidential information on stock trading and mergers. Since the new insider trading caused by cyber attacks has occurred, the US government has also begun to take countermeasures, and a report that the cybersecurity company "FireEye" independently investigated the hacking method of group hunting for company information It is open to the public.
Exclusive: SEC hunts hackers who stole corporate emails to trade stocks | Reuters
http://www.reuters.com/article/2015/06/24/us-hackers-insidertrading-idUSKBN0P31M720150624

HACKING THE STREET? FIN 4 LIKELY PLAYING THE MARKET
(PDF file)https://www.fireeye.com/content/dam/fireeye-www/global/en/current-threats/pdfs/rpt-fin4.pdf
The Securities and Exchange Commission (SEC) is seeking at least eight companies to provide details of information leaks, one of whom said "The abnormal movements of the authorities reflect concerns of the US government's cyber attack It is said that it feels like. This is the first time that the Securities and Exchange Commission has approached the company through investigation of insider trading, and because failure of cyber security creates insider trading by a new method, the authorities are increasingly wary of new kinds of crimes.
It is believed that confidential information was stolen by e-mail account hacking and insider trading was done, and the method of monitoring business transactions and stealing corporate confidential information is a report released by Cyber Security company FireEye in December 2014 It is written in detail. The report reveals a group of "FIN 4" which seems to have stolen company confidentiality of more than 100 companies.
FIN 4 is a group of hackers who steal confidentiality by targeting organizations and companies, 68% of companies targeting medical and pharmaceutical related companies are targeted, 20% of public companies with advisory, securities, legal and M & A related companies, other public company Is 12%. Individuals are being targeted at executives at the level involved in corporate management, people connected to the upper level, attorneys, persons in charge of regulatory, risk, compliance, researchers, scientists and advisory officials.

In addition, 50% of biotechnology companies, 13% of medical equipment companies, 12% of medical equipment / equipment related companies, 10% by pharmaceutical companies, 5% for medical insurance plans, 5% for medical examination / research companies, 3% for medical services and 2% for medical supplies sales. FIN 4 focuses on identifying those who are making M & A deals and identifies them.

After identifying the target, FIN 4 sends a phishing mail along the target's interest. The following is an example of a phishing e-mail actually sent to executives of a company, the title is "About the employee of your company posting negative comments", and as the sender's email address The corporate domain of the unauthorized recipient is used. The content is adopted a clever phishing e-mail, such as "A Forum is posting negative comments by employees of your company", such as URLs written as "applicable forums" .

When you access the URL,VBA(Visual Basic for Applications) An Office document embedded with macros opens, and fake Windows authentication input field is displayed. If you enter the information there, the login information of the mail account is stolen. As a countermeasure to companies that have disabled VBA in Office, instead of linking fakeOWA(Outlook Web App) may be installed in some cases.
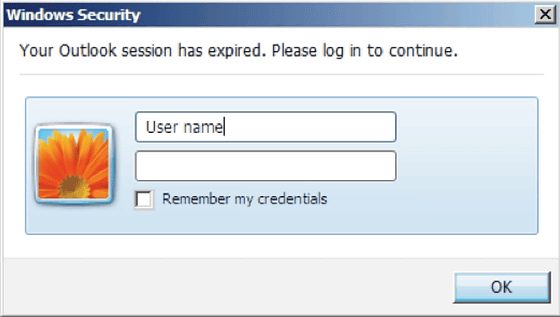
Then, the target whose account information is pulled out is monitored in real time in FIN 4 mail exchanges, and if you proceed with transactions such as M & A, corporate secrets will be leaked outside.
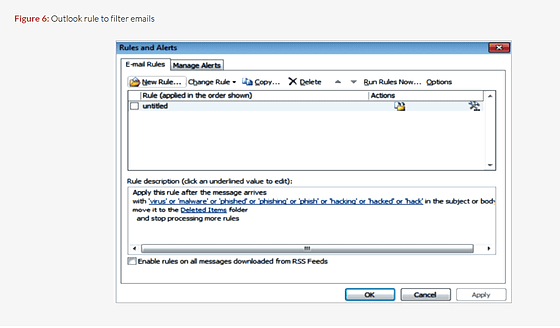
Not only is FIN 4's signature infected with malware, it is difficult to detect that it is hacked with virus software, etc. In addition to FIN 4 hijacking mail accounts, create a mailbox filter I also know that there is. All emails including words such as "phishing", "malware", "hacking" are automatically deleted, and it seems that they are taking time to hack up.
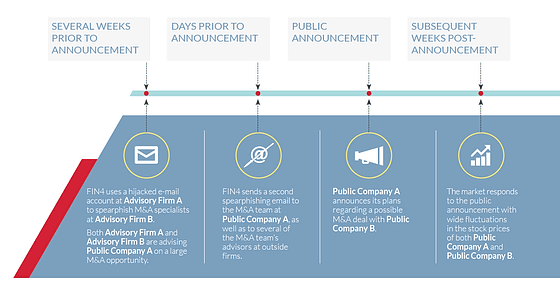
The following is a diagram showing a series of flows of spy acts of FIN 4. As a first step, I hacked the e-mail account of "advisory company A company" and invade the "advisory company B company" from there. Therefore, Public Company A refrained from large-scale merger in a few weeks and information leaked from A company / B company leaked. Furthermore, FIN 4 steals information that it will officially announce the merger of company A and company B in a few days by invading the merger team of public company A company. FIN 4 that got these information is a mechanism that gains profits by conducting insider trading according to market fluctuations.
In addition, FireEye clarified that FBI asked for explanation on this report, and it seems that not only the Securities and Exchange Commission, but also other institutions in the United States are strengthening countermeasures against new cyber attacks.
Related Posts:
in Software, Posted by darkhorse_log