Google announces that Iran-backed hacking group APT42 has targeted US presidential election officials and Israeli military, government and diplomatic institutions

On August 14, 2024, Google's Threat Analysis Group (TAG) published a report stating that
Iranian backed group steps up phishing campaigns against Israel, US
https://blog.google/threat-analysis-group/iranian-backed-group-steps-up-phishing-campaigns-against-israel-us/
Google says it saw Iran trying to hack the Trump, Biden-Harris campaigns
Iran increases phishing attempts on US, Israeli targets | CyberScoop
https://cyberscoop.com/iran-israel-hacking-phishing/
According to TAG, APT42 conducted phishing attacks against approximately 12 current and former senior U.S. government officials and U.S. presidential campaign officials from May to June 2024. APT42's attacks were carried out by both Democratic and Republican campaigns, and TAG reported that it 'blocked numerous attempts to log in to the targets' personal email addresses.'
TAG also confirmed that APT42 had accessed the personal Gmail account of a prominent political consultant and revealed that it had reported this to the FBI in July 2024.
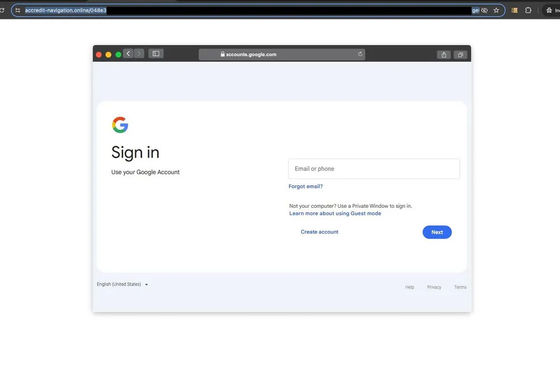
According to the TAG report, APT42 sent phishing emails to targets, posing as real organizations and individuals, in order to steal personal information, and also used pop-up pages disguised as Google Drive and Google login screens to infiltrate targets' computers. It was pointed out that the group weaponized targets' computers in order to send phishing emails to higher-ranking personnel.
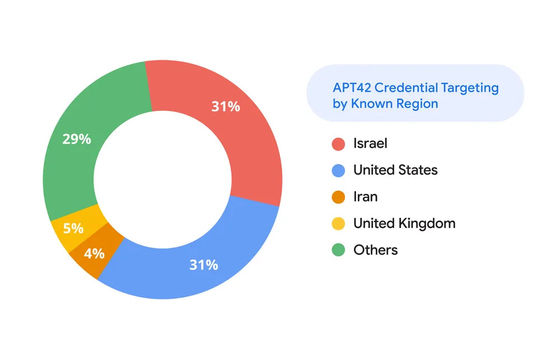
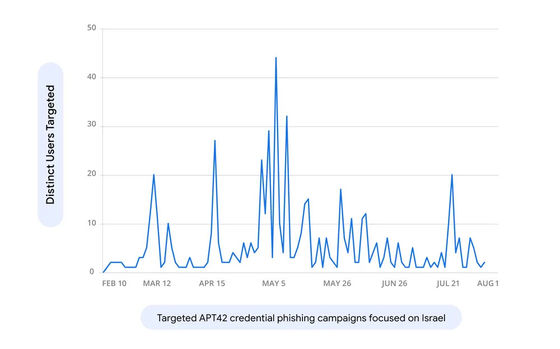
In addition to those involved in the US presidential election, APT42 has also reportedly conducted phishing attacks on Israeli military, government and diplomatic institutions. In fact, between February and late July 2024, Israeli and American users accounted for approximately 60% of AP42's targets.
It has also been revealed that APT42 attacks targeting Israel increased sharply between February and late July 2024, with approximately 45 phishing campaigns being launched per day at their peak.
According to TAG, APT42 has also attempted to socially engineer former Israeli military and aerospace officials by posing as journalists seeking comment on attacks on cities, and has also impersonated organizations such as Israeli military research institutes, using similar websites and email domains.
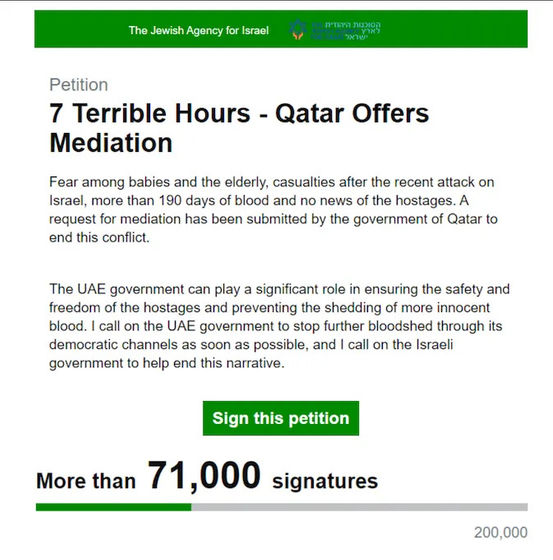
'We have taken down several APT42-created websites calling on the Israeli government to enter into mediation to end the conflict. Some of the sites contain embedded image files rather than HTML, which redirect users to phishing pages when accessed,' TAG reported.
'We continue to monitor US election activity closely and encourage all high-risk individuals, including elected officials, candidates, campaign workers, journalists, election officials, and government officials, to sign up for Google's Advanced Protection Program ,' TAG said. 'Advanced Protection is a free, opt-in program designed to protect users from phishing attacks and other scams, and helps prevent unauthorized users from signing into their accounts, even if their passwords are compromised.'
Related Posts:
in Security, Posted by log1r_ut