"KeySweeper" disguised as a USB adapter and wiretapped the wireless keyboard

A wireless keyboard that can be used anywhere without connecting a cable is convenient, but you can intercept and analyze the operation content transmitted wirelessly and send it via SMS to a third party USB adapter type eavesdropping deviceKeySweeper"Was developed by a hacker's hand.
KeySweeper
http://samy.pl/keysweeper/
"KeySweeper" was created by security expert Samy Kamkar. In 2011Apple, Google, and Microsoft regularly uploaded position information data of mobile devices to the serverIt is also a person who has ascertained things.

You can confirm the actual state of KeySweeper with the following YouTube movie by Mr. Kamkar.
KeySweeper - covert Microsoft wireless keyboard sniffer using Arduino and nRF 24L01 + - YouTube
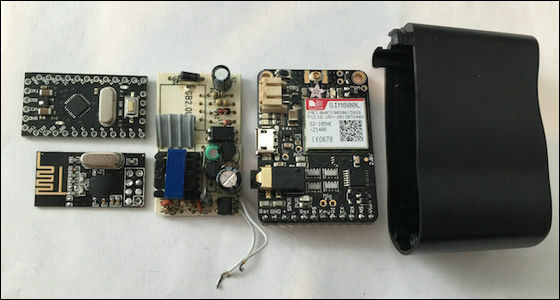
This is the real machine of KeySweeper. At a place like a slightly larger USB power adapter, it is impossible to confirm the kind of antenna that transmits and receives radio waves at all.

Inside, the self-made microcomputerArduino, Radio wave transmission / reception board, 2G communication board and so on.
KeySweeper intercepts data indicating key operation information sent from a Microsoft wireless keyboard. The company's products are protected by using proprietary communication protocols, so it seems that they have hardly been deciphered so far.

In the specifications of the wireless keyboard published by Microsoft, radio waves of the 2.4 GHz band are used for communication, and its platform has its ownProprietaryIt is stated that the protocol is used.

In order to elucidate its communication method, Kamkar first started research based on the FCC ID described on the keyboard.

With FCC ID databaseHit contentsIt turns out that this product uses the radio wave band of the frequency 2403 MHz to 2480 MHz.

Kamkar predicts that the chipset for data communication used for the keyboard is one of Nordic's "nRF 24L01 +", TI made "CC2500", and Cypress "CYRF 6936" based on experience and so on. And actually check the contents of the product and make "Nordic"NRF 24LE 1It was found out that it is. This chip is a low-power chipset that integrates a wireless chip and a CPU, and it is sold at eBay and other e-commerce websites in the order of only 1 dollar (about 120 yen).

Kamkar succeeded in constructing a system that analyzes by intercepting keyboard communication and combines with Arduino etc. based on the specifications found out. The created source code isGitHubIt is said to be published in.

Next, Mr. Kamkar prepared a USB adapter to hold boards. An affordable product was found.

However, since all the boards can not fit as it is, disassemble the USB charger for iPhone and take out only the power supply part.

Divide the taken out power unit ......

Succeeded in making multiple boards compact. Inside of this is a board that intercepts radio waves, an Arduino board to analyze it, and a 2G communication board for SMS transmission of data on a mobile phone line.

The diagram is as follows. Mr. Kamkar's site is an electronic circuit design toolFormat corresponding to FritzingYou can download the data of.

By using KeySweeper produced in this way, what actually intercepted operation content was sent by SMS. After entering "initely try to make it!" Press the enter key, the cmd key and the tab key are pressed twice simultaneously. After you press the cmd key + L key at the same time, you entered "facebook.com" ... it is a duct.

KeySweeper disguised as a USB power adapter can actually be used as a USB power supply. Lithium-ion battery is built in the interior and it is designed to continue to operate until the battery runs out even if it is pulled out from the outlet.

The catch phrase listed on Mr. Kamkar's website is "Think Bad, Do Good" (thinking bad things and acting well). It is unknown what kind of application this device will actually be used, but it seems to be said that it is an example showing that everything is possible if hacking technology is used.
Related Posts:







