A system that sends monitoring malware to millions of computers is secretly in operation

ByCorey Burger
In June 2013 by Mr. Edward SnowdenConfidential system "PRISM" for collecting personal information by the US governmentTheir existence has been revealed. At the National Security Agency (NSA) developing and operating PRISM"Quantum" plan to monitor 100,000 PCs online and offlineIt is revealed in January 2014 that in addition to this, in addition to this, there was also a system that spreads the monitoring network by automatically sending malware to 1 million computers I found out.
How the NSA Plans to Infect 'Millions' of Computers with Malware - The Intercept
https://firstlook.org/theintercept/article/2014/03/12/nsa-plans-infect-millions-computers-malware/
NSA's automated hacking engine offers hands-free pwning of the world | Ars Technica
http://arstechnica.com/information-technology/2014/03/nsas-automated-hacking-engine-offers-hands-free-pwning-of-the-world/
NSA can freely access and collect information on servers owned by net companies such as Google · YouTube · Microsoft · Apple · FacebookConfidential system "PRISM"According to the secret document published by Mr. Edward Snowden, NSA added malware to millions of computers to further expand the information gathering capacity, It is said that he has developed a technology to set up.
As of 2004, NSA sent malware and the number of machines targeted for monitoring was from 150 to 150. However, NSA organized hacker's elite unit called "Tailored Access Operations (TAO)" over six to eight years and increased the number of targets to be monitored to tens of thousands. As a result, since it exceeded the limit that human beings can handle, it was developed as "Turbine (turbine)It is called a system called. Turbine is a system that has "intelligent command and control ability" and "can be used on an industrial scale", and it operates in July 2010, thanks to which the number of monitored machines has increased from 85,000 to 100,000 It is said that it increased to.
One of the malware that is sent to the monitored machine is the codename "UNITEDRAKE" and it is possible to fully control the control of the infected machine by installing various plugins. The plug-in includes CAPTIVATEDAUDIENCE which collects surrounding sounds picked up by the microphone, GUMFISH which takes pictures using a web camera, FOGGY BOTTOM which records login information including browse history and password, GROK which records keystroke contents, SALVAGERABBIT to extract data of removable drives (such as USB memory and SD card) connected to the machine you have done.
According to the internal document, the NSA has commented that it collects and uses information to prevent intelligence abroad, domestic spy activities and terrorist activities, and does not use it for other purposes, but according to internal documents, It was not necessarily targeted to terrorists or extremists, it seems that ISP system administrators were also targeted. British intelligence agency equivalent to NSA · GCHQ implemented a strategy "Operation · Socialist" targeting Belgian telecommunications company Bergacom and gained the ability to access Bergacom's system from 2010 It is.
However, the NSA was not aimed only at "information gathering", but for example, using QUANTUMSKY to block communication of targets accessed from a website and QUANTUMCOPPER interfering with file download on infected machines, It was causing confusion.
As a method of sending such malware, a strategy called "WILLOWVIXEN" that uses spam has been used. In this case, malware was making backdoor within 8 seconds after activation, but in recent years it has gone wrong due to an increase in users wary of spam.
Instead of faking it as a fake Facebook server to make the user log in to Facebook, sending malware behind the login process (what the user thinks), extract the information in the HDD .
This movie illustrates this flow in this movie.
How the NSA Secretly Masqueraded as Facebook to Hack Computers for Surveillance on Vimeo
It is NSA 's network that lies on the left side with the central space and the target network (general internet) on the right side. When a user tries to access Facebook, a packet sensor called "TURMOIL" detects access and interrupts before the turbine moves and the Facebook server returns the request.
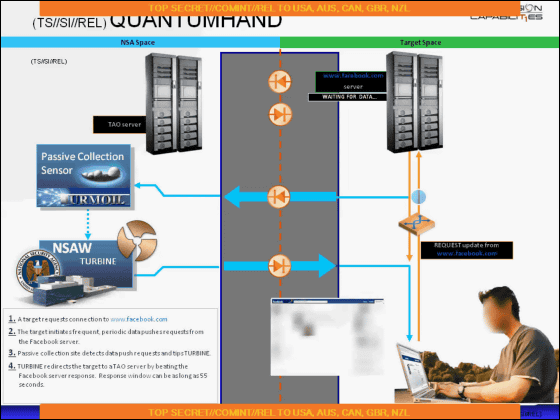
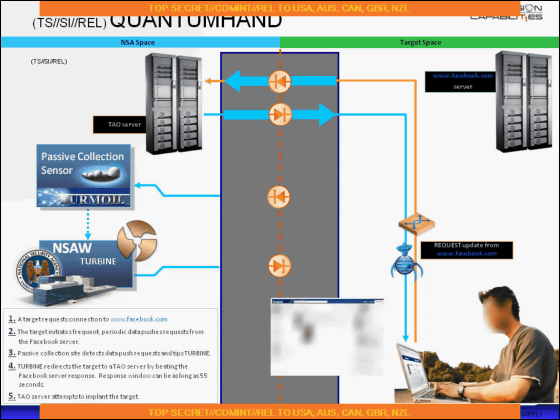
If this is the case, even if you are accessing Facebook, the communication destination switches to the NSA network that pretending to be Facebook, and while waiting while logging in, the malware (indicated by a blue worm in the figure) It is charged.
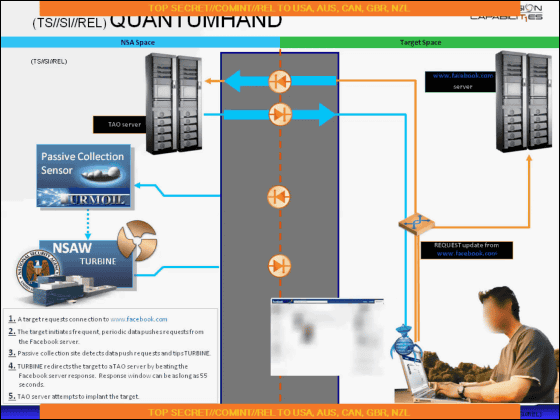
When we finish loading the malware, we switch to communication to the real Facebook server, so the login process is done normally and the user does not notice that it is infected with malware. The base of such "network eavesdropping" is not only at the Fort Meade Army Base in Maryland, where the headquarters of NSA is located, but also at the Menwith Hill base in the British Air Force and Misawa base in Japan.
Jay Nancarrow of Facebook commented that "Facebook is supporting HTTPS in 2011, and in 2013 it made HTTPS connection standard," There is no evidence that such activities were taking place. " I admit that it may be possible for NSA's system to be interfered with similar net services including Facebook.
Not only the net service is dangerous. NSA's elite hacker unit TAO also targets vulnerabilities such as web browsers such as Internet Explorer and Firefox, routers used for network connection, and Flash and JAVA operating as plug-ins, and behind the anti-virus software program He said he was doing something like that. Since NSA is investigating these technologies, it seems to be very difficult to detect.
For these facts, he is the principal researcher of F-Secure Security Research InstituteMikko Hipponen"With NSA running malware, there is a danger that new infected machines will be targeted by third parties on infected machines," he said. Embedding millions of malware pointed out that NSA is in a state where it is impossible to control the whole and that it may be in a state of massive infection / large-scale monitoring that can not specify a specific target Did.
By the way, one of the main concerns of NSA is that "Overseas countries are adopting similar secret tactics".
Related Posts: