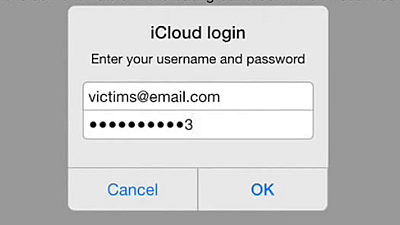
Starbucks saves passwords etc. registered in the application without encrypting them

ByJason Hargrove
Coffee chain store Starbucks can pay for iPhoneSpecial applicationWithout encrypting data such as user name, password, and mail address registered inClear text (clear text)It turned out that it was saving with.
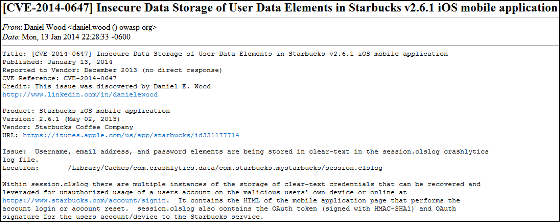
Full Disclosure: [CVE - 2014 - 0647] Insecure Data Storage of User Data Elements in Starbucks v 2.6.1 iOS mobile application
http://seclists.org/fulldisclosure/2014/Jan/64
Evan Schuman: Starbucks caught storage mobile passwords in clear text - Computerworld
http://www.computerworld.com/s/article/9245438/Evan_Schuman_Starbucks_caught_storing_mobile_passwords_in_clear_text
Security of Starbucks Mobile App for iOS | Starbucks Newsroom
http://news.starbucks.com/views/security-of-starbucks-mobile-app-for-ios
Starbucks' iOS app is proud of its popularity in the United States because of its ease of use. The user can pay the price from the application by simply entering the set password and charging the application with cash.
Data such as passwords and user names registered in the Starbucks iOS application were saved in the smartphone itself so that you do not have to enter it every time you use it, but since it was not encrypted, connect your smartphone to your PC It was in a state that anyone can read it if it did. Also, it is known that not only account data such as passwords, but also location information such as geolocation was stored in plaintext.
Daniel Wood of a security researcher who found a vulnerability of a special application. After noticing the vulnerability, Wood attempted to contact Starbucks, but no matter how many times we contacted you could only get a response "Please contact customer service", so on January 13, 2014SecLists.OrgWe posted the content of the investigation to the fact that vulnerability was discovered.
Computerworld conducted a phone interview with Starbucks' Chief Digital Officer Adam Brotman on the vulnerability of the special application. Brotman said in an interview, "We are aware of the vulnerability of specialized apps and measures have already been taken, so users will not have to worry," while concretely speaking about vulnerabilities I did not answer about measures.
Three days after the vulnerability of the special application was discovered January 16, 2014, Starbucks announced the official comment on the vulnerability on the official website. After announcing the vulnerability at the announcement, "There are no users who leaked account data due to the vulnerability we discovered this time, and we are currently in the process of updating the application at a rapid pace" We are planning to distribute it soon.
Related Posts: