Google "How to recover an attack site certified (hacked) site" public
In early FebruaryExamples of cases where the Japan Weather Association, Picsive Encyclopedia, etc. are blocked by Google as "attack site"Occurred. Also in early MarchEvery day jp and My Navi news are blockedAlthough there was a case, even a famous site · even a major site it is difficult to prove that an unknown site was "blocked as well" if it is similarly blocked. For such a case, Google has released "How to restore (revive) hacked sites". There is also a movie to explain from "where is it originally hacked"? It is rather polite.
Webmasters help for hacked sites - Google
http://www.google.com/webmasters/hacked/
Friends help friends recover their hacked sites - Google Developers Blog
http://googledevelopers.blogspot.ca/2013/03/friends-help-friends-recover-their.html
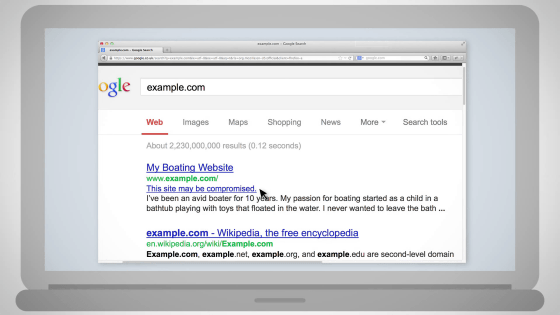
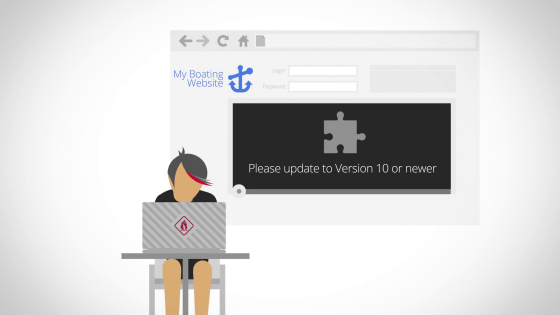
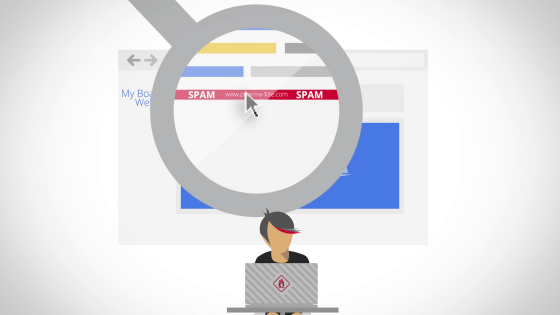
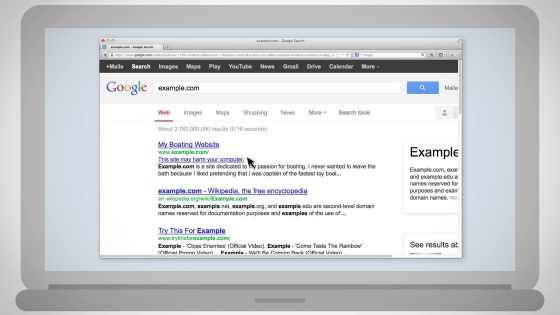
In Google's search results, under the link, "This site may harm your computer" may be displayed, or if you access it, a warning may be displayed and you may not see the original site.
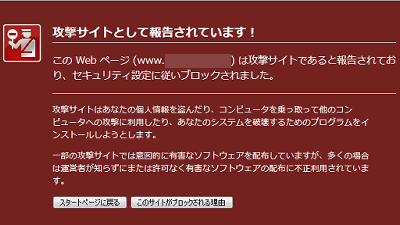
The fact that this is displayed means "I'm sorry, but the site was hacked," Google said. This means that means for recovering from this state is explained at movies and sites this time. The first thing to watch is this movie, the length is 7 minutes 21 seconds.
Help for hacked sites: Overview - YouTube
"Help for hacked sites"

Maile Ohye of Google Webmaster support team will show you.

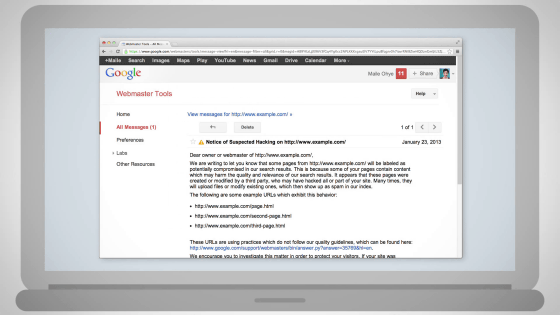
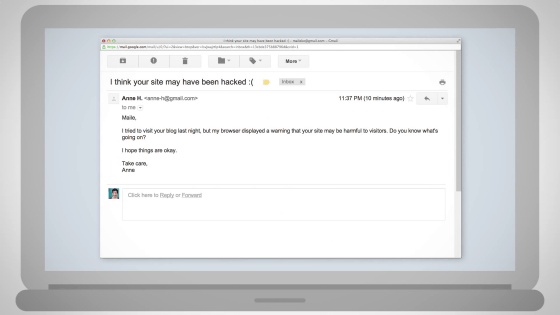
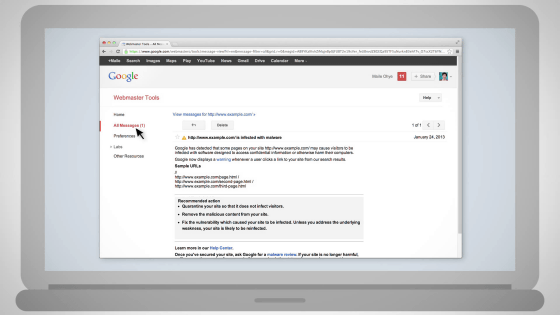
We may find out that your site is certified as an "attack site" with Google search, notification from browser, Google Webmaster Tools, email from friends, etc.

It is this movie that explains what to do in order to make it a site where everyone can be seen, why it is blocked in the first place.
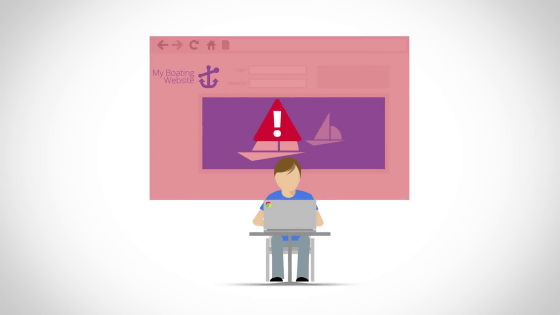
Consumer groupsStopBadwareAccording to the tool we are offering, it seems that 130 thousand sites have successfully escaped from the blacklist for three years. This is the same thing that Google provides.

I have two approaches, I do it myself if I am in technical. Another one asks trustworthy experts.

Find the danger and remove it ...
If it is confirmed OK ... ...
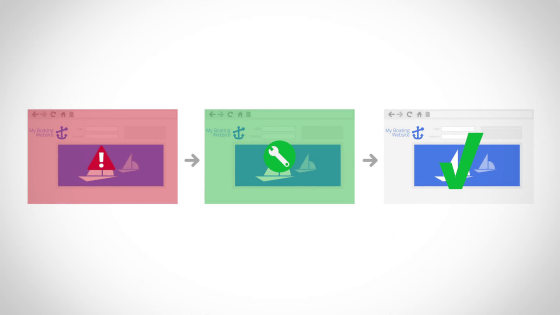
It is restored.
From here it flows until hacked. Suppose you have operated a wonderful site.

However, if there is a vulnerability somewhere ... ...
"Malicious attacker" will immediately set up a cyber attack.
It is like a small wound affecting the whole body.


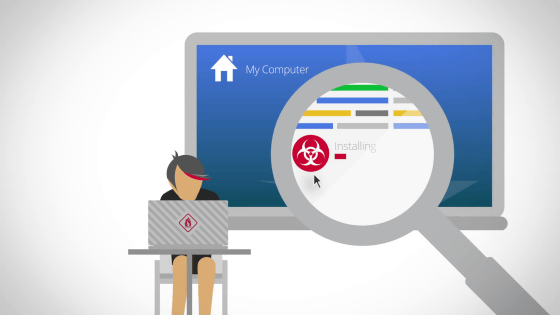
An attacker could install spam links on the site, or create a mechanism to install malware.
It is aimed at plugins and software that are not upgraded and not safe ......
It is a vulnerability of a site (service) that can steal login information.
Alternatively, install malware ......
I might be stealing private information secretly.
The motive of hacking is mostly economical.
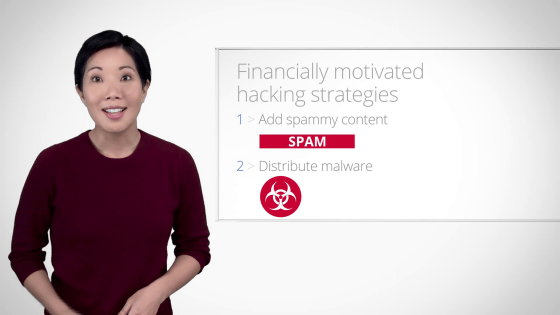
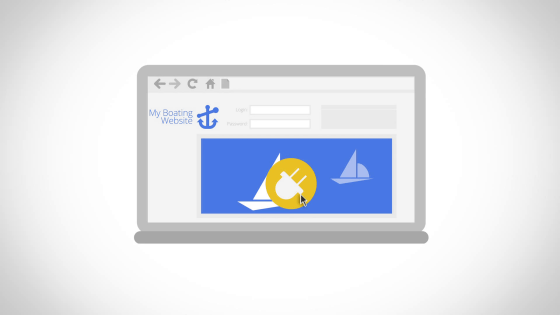
For example, suppose you use something plugin for users at your site.
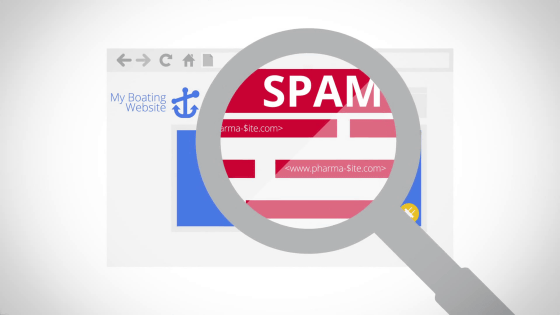
On the other hand, an attacker wants to attract people to the site selling prescription drugs.
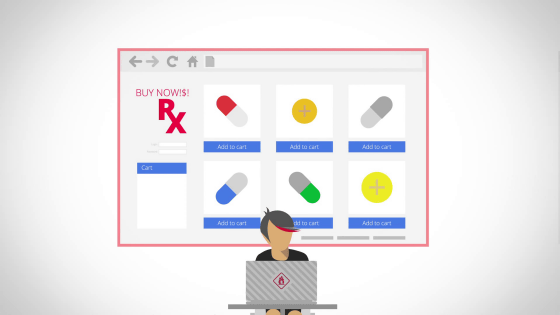
As a means to do that, I can think of sneaking a link to the above site on the site.
If this attacker is already aware of plug-in vulnerability at other sites ......

It means that the target is a site using the same plugin, which means that your site will also be targeted.

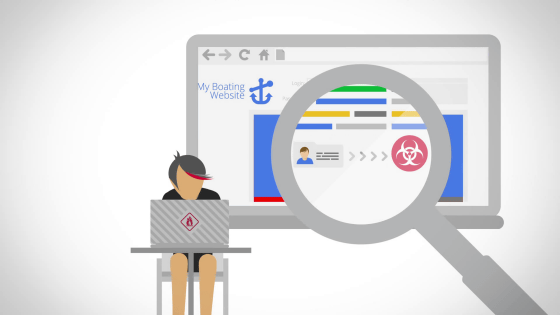
Even if you look at the spam link, it steals so as not to know it, so there are cases that you do not notice that you are injured.
However, when a search engine like Google crawls ......

In a website linked by various links ... ....
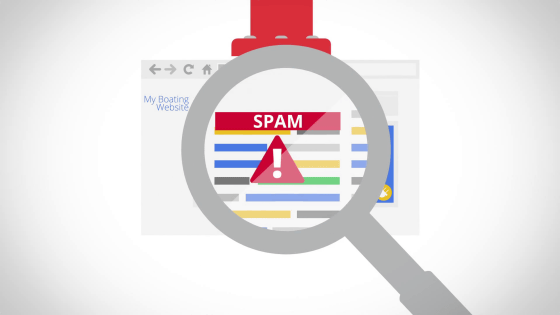
As a site containing links (spam links) to sites recognized as dangerous sites, your site will be listed. This is sometimes blocked.
More serious in case of malware.
"I went to the site and I got infected with malware."
This can happen to anyone who visits the site without taking a specific link.
Infected users ......
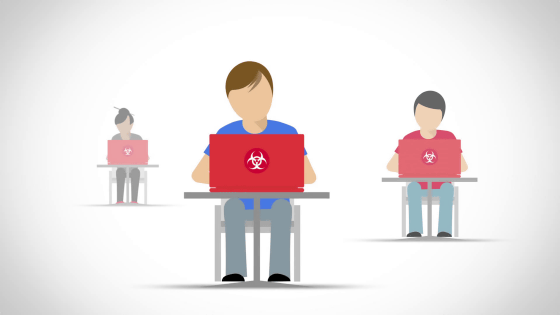
It is possible that an attacker could steal personal information and account information.


To such sites, Google notifies you that "This site is dangerous" in search results.
At the same time, we send notifications to webmaster tools to site administrator ......
I am sending mail directly.
So on the concrete method we will continue to the next movie.
The steps are divided into eight in total,
1:Looking at the overview (the movie above)
2:Contact the hoster (service administrator etc.) to make a support team
3:Quarantine the site
Four:Confirm site ownership with Webmaster Tools
Five:Assess damage
6:Identify vulnerabilities
7:Make the site "clean"
8:Request investigation
It has become. Among them, 1 and 2 are classified as "Beginners", 3, 4 and 8 as "Intermediate", and 5, 6 and 7 as "Advanced".
Aside from whether it can actually be done or not, since Japanese version is not prepared at this stage, we would like to ask you to provide Japanese version for users as well.
Related Posts:
in Web Service, Video, Posted by logc_nt