Concluding remarks of "iesys.exe" to make a notice of crime by remotely operating via thread on bulletin board

ByIKorp
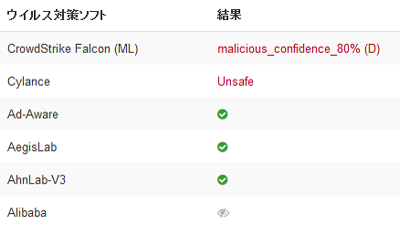
An e-mail asking for the release of Aum Supreme Truth Shogun's Aum Supreme Truth Shogun's death row prisoner arrives at the customer correspondence window of Japan Airlines and an incident occurs when the flight to the United States returns, as Osaka-shi I was arrested mistakenly for a misunderstanding because I wrote in the column "Osaka / Nihonbashi's Otarudo pushed into the pedestrian zone with a truck and I will indiscriminately draw" in the opinion column for municipal administrationKitamura MasakiMr. Mr. 's computer discovered remote control virus (backdoor, in essence a malicious program that makes a back door)Iesys.exeAlthough it turned out that it was a file name of "It is a file name", Trend Micro, famous for Will Buster, explains what it is like.
Caution: Remind alert about pre-impersonation crime notice by remote control using malicious program
http://www.trendmicro.co.jp/support/news.asp?id=1851

First of all, there are malicious programs of the type called "backdoor" "bot" as a conventional means of recent attacks, and these malicious programs are aimed at remote control from the outside, and IDs for online banking of banks from the personal computer It was mostly used to hide your identity by creating a stepping stone for secretly pulling out passwords, credit card numbers, etc., or "stepping stones" for other attacks, but this time it is finally spoofed by yourself It is expected that notice of crime by the cause etc. will start to happen.
For example, criminal punishment for illegal download was enforced from 1st October, but if you were made "stepping stool" by the backdoor or bot earlier, actually you did not download any files As in this case the police and the prosecution said "There is confirmation of IP addressIt asserts that he is coming to arrest. From the point of view of the police and others, I think that the IP address that appears in the investigation result is like a "fingerprint", so this time it happened to be good because it detected "iesys.exe", but similar backdoor Some of them have deleted themselves after fulfilling their duties, so that someone who is made a stepping stone will not only become virtually disapproved of the means to prove that he was a stepping stone, but also become a stepping stone Not being aware that even though it was, police and the prosecution said "I will lose my sin if I admit itThere is a possibility that even though it is innocent like this time it is likely to be arrested actually, so if you do not pay attention to security more than ever before, when you are the victim It is not understood whether it will become.
, "Iesys.exe" this time mainly has the following features.
Backdoor type malicious program "BKDR_SYSIE.A" that gives a notice of crime by remote control | Trend Micro Security Blog (Trend Micro Security Blog by virus analyst)
http://blog.trendmicro.co.jp/archives/6098
BKDR_SYSIE.A | Risk factor: Low | Trend Micro: Security database
http://about-threats.trendmicro.com/malware.aspx?language=jp&name=BKDR_SYSIE.A
When this iesys.exe is infected, a setting file called cfg.dat is created and an illegal entry is added to the following part of the registry so that it starts automatically at the time of Windows startup.
HKEY_CURRENT_USER \ Software \ Microsoft \
Windows \ CurrentVersion \ Run
{Malware filename} .exe = "{malware path} \ {malware filename} .exe"
What kind of remote operation is done is as follows.
· Key input operation information of the user and operation record of the mouse (so-called key logger, entered password etc. all go through)
· Operate and open a specific URL with a hidden browser (probably written in this case)
- File download (It is possible to collect information such as who owns infected PC by this function)
· Uploading files (You can send anything even with child pornography, so you can do anything if you want to make it as a further criminal)
· Acquire screenshot (It is also possible to obtain various information of owner of that computer even by this)
· Enumerate files and folders (find important files and download them)
· Execution of files (You can also copy and delete files freely)
· Acquire default Internet browser
· It is a function that makes it possible to prevent itself from being detected by keeping updating itself before the update of the antivirus software, a function that is more common in more advanced bots and backdoors)
- Update of environment setting file (necessary for remote operation to be described later)
· Updated thread of used bulletin board (necessary for remote operation to be described later)
· Sleep computer for a certain period of time
· Delete itself from the computer (You can lose any evidence by deleting yourself)
In addition, how to do "remote operation" is to access a thread of a specific URL on the bulletin board site on the net, and by writing that indicates a specific command written in the thread, the above command It is going to execute. According to Trend Micro, the URL of the bulletin board to be accessed is as follows.
http://<省略>s.<省略>or.jp/bbs/<省略>.cgi/<掲示板のカテゴリ>/<BBSのID>/<スレッドのID>/
http://<省略>s.<省略>or.jp/bbs/<省略>.cgi/<掲示板のカテゴリ>/<BBSのID>/
This format applies to "Livedoor if you bulletin board: Free Rental Bulletin Board"is. For example, if you create a bulletin board in the category of "computer" the address will be as follows. The part of the number written as "99999" becomes the above "
http://jbbs.livedoor.jp/computer/99999/
Further threading it will result in the following address. The part of "0000000000" is "
http://jbbs.livedoor.jp/bbs/read.cgi/computer/99999/0000000000/
In this way, a specific thread in a specific bulletin board is described in the configuration file "cfg.dat".
Why is this "doing a command via a bulletin board website on the net"? That means that when you open this bulletin board, there are several disposable email addresses and multiple proxy servers overseas Because it is possible to hide your identity easily by going through 'stepping stones'. Whether or not the command written to the thread was executed properly can be confirmed easily and safely by "iesys.exe" which is the backdoor · bot itself writes the issue result of the command to the thread. In addition, the function itself of which thread on which bulletin board is used for sending and receiving commands itself is also provided with functions such as "updating environment setting file" and "updating thread of used bulletin board" which can be controlled by writing of command issue It is understood that it is built in considerably high function so as not to be able to find out where remote control is done from where.
There are already types that send and receive commands via "IRC" or "Newsgroup" overseas, but there is a part of substituting it with "Japan's unique" thread type bulletin board " It is a fairly special part of this time and it is a purpose itself to make a police or prosecution arrest mistakenly by fake "crime preliminary announcement", and it is an exaggeration to say that it is an unprecedented type of crime It is not.
In the future, if police and the prosecution do not investigate on the premise that there are backdoors and bots of this type of "tailor to the criminal", there are cases where they are arrested despite being innocent At the moment, police and prosecutors deal with "IP address" like "fingerprint" at the moment, unless you are careful about security and self-defense, it is expected to occur in such a crime It is not amusing to be involved. Although it is fundamental for self-defense to frequently update the security relationships of various software, in some cases "Zero Day Attack"It is virtually impossible to completely defend because vulnerabilities are discovered and infected and remotely controlled by exploiting the vulnerability before security updates are found.
· 2012/10/11 20:00 additional note
According to Symantec, famous for the Norton Antivirus series, it is said that authors of malicious programs who do this backdoor from their own analysis results are highly likely to be Japanese or highly fluent in Japanese, and analyzed as evidence The Japanese character string included in the resultPublic on official blogdoing.
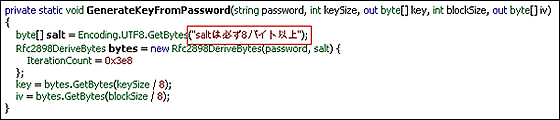
It is also confirmed that there are two versions, and it seems that one is "2.23" and the other is "2.35". Since there is not continuous between versions, there is an unknown version in the meantime, or it has already been upgraded to a different version considerably with a high probability and it is steadily upgraded and detection is escaped, or additional functions are implemented, etc. The possibility of uploading is great.

なお、シマンテックが公開している情報ではコマンドを受信するために使われている掲示板サイトを「http://jbbs.livedoor.jp/」であると明記、「したらば掲示板」を経由してコマンドを受信するので「したらば」をもじって「Backdoor.Rabasheeta(バックドア・らばしーた)」と命名しています。ほかにも、コマンド自体は「BASE64 でエンコードされ、Rijndael で暗号化されたコマンド」であると書かれており、ファイルをアップロードするアップローダのアドレスも「http://sysdeck.boxhost.me/upld.php」であると明記しています。
· Continued
Which is the author of "iesys.exe" and the entire e-mail from the real culprit of the remote operation incident is open, what is the biggest problem? - GIGAZINE

Related Posts:
in Note, Posted by darkhorse