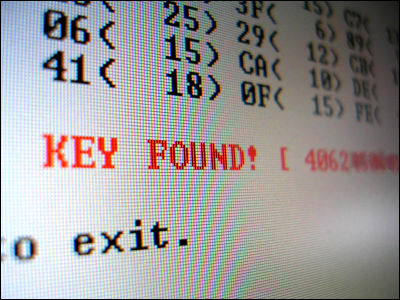
WPA encryption broken completely: Japanese Academic Researcher implemented falsification attack

While existing Tews-Beck method needs fifteen minutes or so to break WiFi Protected Access(a.k.a. WPA), this new method composed by Japanese academic researcher enables to break into WPA-protected networks in only a second.
Titled "A Practical Message Falsification Attack on WPA", this new method to attack WPA will be presented in JWIS2009(Joint Workshop on Information Security) held in Taiwan on Aug. 7 by Dr. Toshihiro Ohigashi, associate professor of Hiroshima University and Dr. Masakatsu Morii, professor of Graduate School of Kobe University on Aug. 7.
Read on for detail.
Joint Workshop on Information Security
http://jwis2009.nsysu.edu.tw/index.php/jwis/jwis2009/schedConf/program
According to Dr. Morii, the method is about how to exploit WPA-protected wireless network by utilizing vulnerability in its protocol. This will enable crackers to falsificate packets and penetrate into protected networks.
Existing Tews-Beck method also enables to break TKIP, the key mechanism consisting WPA. But the method needs 15 minutes or so, and target of attack is limited to several version of wireless protocol. Theoritically it helps the penetration, but no actual utilization is indicated.
This new method reveals the key transmitted by TKIP using its vulnerability in much shorter time(usually in a seconds). Dr. Morii also indicates how to attack the network utilizing this method. With this, such as APR and DNS poisoning or malware infection would be enabled.
Dr. Morii says "WEP is no more valid as a encryption, and so is WPA using WEP as base mechanism. It's imperative to move onto WPA2 for better security"
Here's some slides to be shown at JWIS2009
Fig.1 Title

Fig 2. Summary

Fig.2 man-in-the-middle attack utilizing the method.
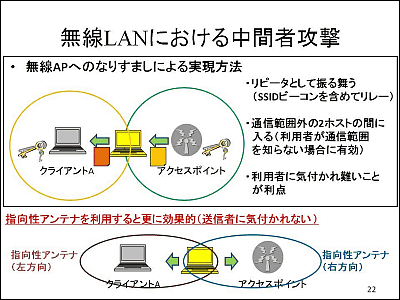
Migration from WEP to WPA can be simply done by firmware update, but to WPA2 it's rather difficult for you need proper hardwares accepting WPA2 protcol. So for enterprise clients with a lot of legacy equipments this method would cause some serious troubles.
They also present further studies at Information System Researchers's Conference of IEICE held at Hiroshima University
"A Practical Message Falsification Attack on WPA"
Yuki Ozawa(Kobe University), Toshihiro Ohigashi(Hiroshima University), Masakatsu Morii(Kobe University)
Related Post:
Which CAT7 cable is the most flexible and easy to handle? - GIGAZINE
Trailer of “Tron Legacy”, the re-produced legendary Sci-Fi 3DCG movie revealed - GIGAZINE
KDDI exhibited “Micro SD Wireless LAN Card” at Wireless Japan 2009 - GIGAZINE
Related Posts:
in Note, Posted by darkhorse