It turns out that 'example.com' was automatically configured to point to Sumitomo Electric Industries' server domain in Japan using Microsoft's autodiscovery service.

It has been discovered that the domain 'example.com,' used for testing and explanation purposes, is treated as a real mail server in Microsoft Outlook's auto-configuration feature, resulting in users' authentication information being sent to unintended recipients. While no external DNS settings were found to be misleading, Microsoft's autodiscover service reportedly returned IMAP and SMTP hostnames that appeared to be under the sei.co.jp domain of Sumitomo Electric Industries, Japan.
Microsoft mishandling example.com
Why has Microsoft been routing example.com traffic to a company in Japan? - Ars Technica
https://arstechnica.com/information-technology/2026/01/odd-anomaly-caused-microsofts-network-to-mishandle-example-com-traffic/
The issue originates from the automatic configuration when adding an account in Outlook. Technology blog tinyapps.org confirmed that when a dummy email address using example.com, such as '[email protected],' is entered, an IMAP hostname under sei.co.jp is suggested as the receiving server, and an SMTP hostname under sei.co.jp is suggested as the sending server, even though the environment normally prevents automatic configuration from working. The suggested hostnames are considered to be subdomains belonging to Sumitomo Electric Industries. As a result, if the user proceeds with the configuration, the entered username and password may be sent to that host.
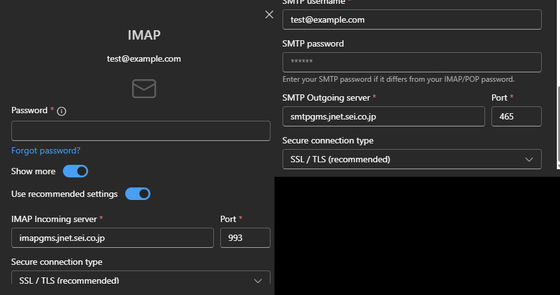
However, a verification of tinyapps.org revealed that example.com was configured to not accept emails, and that the typical DNS records used for autoconfiguration were missing. Furthermore, a null MX record indicating that no emails are accepted was set for the email delivery destination, and no records that could be used as a clue to authenticity, such as a CNAME for autodiscover.example.com or an SRV for _autodiscover._tcp, which indicates the location of the service for autoconfiguration, were found.
This means that it is highly likely that the public settings on the Internet are not directing users to Sumitomo Electric Industries' hostname, but rather that Microsoft's autodiscover service itself is returning the information in question. Technology media outlet Ars Technica pointed out, based on Outlook's behavior and command line confirmation, that the autoconfiguration information returned by Microsoft's autodiscover API points to a subdomain under Sumitomo Electric Industries' domain. The paper stated, 'Because there are a certain number of people who try to set up Outlook using example.com, there is a possibility that authentication information entered as a test may be mistakenly sent to the target server under sei.co.jp.'
tinyapps.org showed the JSON returned by Microsoft's Autodiscover API, explaining that it explicitly included the server information pointed to by the Autodiscover response. Furthermore, decoded debug information suggests that the setting was created and updated on February 3, 2020, and may have been manually registered.
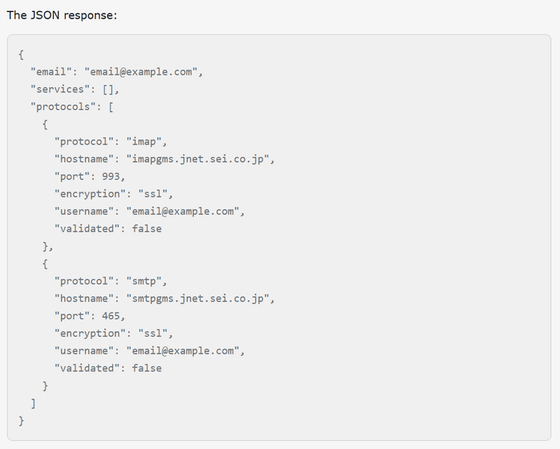
It is unclear at the time of writing why Sumitomo Electric Industries' domains were affected. Ars Technica contacted Microsoft, who said, 'We have confirmed that we have updated the service to no longer provide recommended server information for example.com,' and revealed that an investigation is ongoing. However, Ars Technica noted that it appears that the autodiscovery contacts simply stopped responding, and the root cause remains unclear.
Related Posts: