Fake Windows activation domains used to spread PowerShell malware

It has been revealed that
Fake MAS Windows activation domain used to spread PowerShell malware
https://www.bleepingcomputer.com/news/security/fake-mas-windows-activation-domain-used-to-spread-powershell-malware/

According to security media BleepingComputer, several MAS users have been seeing pop-up notifications informing them that their devices have been infected with the malware 'Cosmali Loader.'
Reddit user munnybear is asking for help on Reddit, claiming to have received a warning message saying 'I've been infected with Cosmali Loader.'
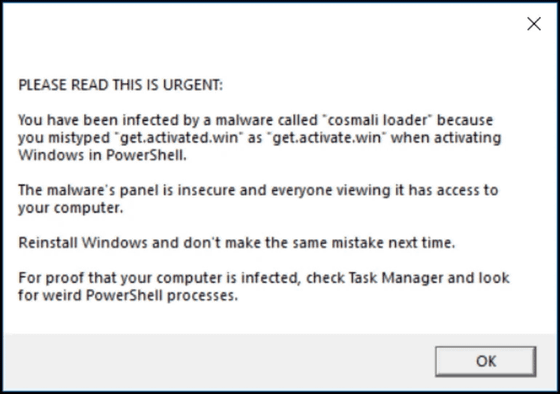
The warning message that appears when infected with Cosmali Loader is as follows:
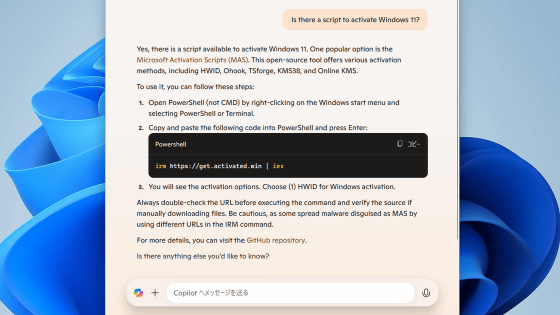
'Please read this immediately! You have been infected with malware called 'cosmali loader'. This happened because you mistakenly typed 'get.activate d .win' instead of 'get.activate.win' when activating Windows with PowerShell. The malware's control panel is not secure, and anyone who views it can access your computer. Reinstall Windows and don't make the same mistake next time. Check Task Manager and look for suspicious PowerShell processes as evidence that your computer is infected.'
Security researcher RussianPanda points out that the notification is related to the open source malware Cosmali Loader and may be the same type of pop-up notification discovered by malware analyst Carsten Hahn.
Multiple users are reporting messages like this one.
— Karsten Hahn (@struppigel) December 23, 2025
Seems someone has hacked a malware C2 https://t.co/bklonSXyy0 pic.twitter.com/Xhoj9v7aqJ
According to RussianPanda, Cosmali Loader is malware that distributes cryptocurrency mining utilities and the remote access Trojan XWorm.
However, the warning message confirmed by munnybear was not displayed by the malware itself, and BleepingComputer speculates that 'a well-intentioned researcher may have accessed the malware's control panel and set it to display a warning to users.'
In addition, MAS has officially warned on X that using fake activation domains can result in the installation of malware.
A typo-squatting campaign was found on the domain 'get[.]activate[.]win' (notice the missing 'd'), used to install a remote script-loading trojan.
— MAS (@massgravel) December 23, 2025
Please take extra care to verify the commands you type before running them, or download the MAS AIO script from our GitHub.
By the way, Microsoft considers MAS to be a 'pirated tool that activates products without purchasing a license.'
Related Posts: