A story about a remote job interview task containing malware that almost led to a hack

In recent years, with the increase in remote work, 'online interviews' have become a more common method of job hunting, eliminating the need to visit a company in person. At the same time, cyber attacks disguised as online interviews have also increased, and David Dodda, who almost fell into the trap, has issued a warning based on his own experience.
How I Almost Got Hacked By A 'Job Interview'
Dodda had been working as a freelance web developer for eight years and had experience participating in a variety of projects. One day, he received a LinkedIn message from Mykola Janczy, who claimed to be the Chief Blockchain Officer of a company called 'Symfa.' The message introduced the job, saying, 'We are developing a platform called 'BestCity' that aims to transform real estate workflows. We are also hiring part-time positions with flexible hours.'
Dodda, with his long experience as a freelancer and a developer himself, considered himself to be highly security-conscious and cautious. Although he didn't blindly believe Yang Qi's request, Dodda decided to respond to it because Symfa was a real company, Yang Qi's LinkedIn profile was authentic, and he had over 1,000 'connections,' which is equivalent to 'following/followers' in X.
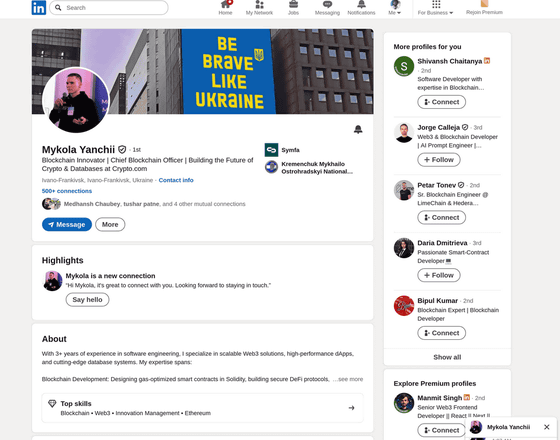
It was later decided that an online interview would be held, and Dodda was asked to complete the standard pre-assignments, such as codebase testing and preparing materials. The pre-assignments included receiving a BestCity repository, running the code, reviewing it, and making corrections. However, Dodda was short on time before the interview, so he started editing the source code directly without running it.
Before completing the task, Dodda instructed the AI agent to 'check for suspicious code in this codebase before running this application.' The agent discovered malware embedded in the code of legitimate administrative functions, which ran with server privileges the moment it accessed the administrative root, stealing cryptocurrency wallets, passwords, files, and more. Dodda described the scam as 'obfuscated, malicious, and sophisticated. The profile looked authentic, and there were no unusual interactions during face-to-face interactions.'
Dodda then messaged Yangqi seeking comment but did not hear back from him.
Dodda points out that the key point of this scam targeting developers is the time pressure to complete the test before the interview time. While reviewing the code locally is a standard test, time constraints can lead to people neglecting security checks and running the code in a secure environment, which are usually required. By skipping steps and running the code locally, there is a risk that the PC will be infected with malware.

To avoid falling victim to this scam, always sandbox any unknown code in an isolated environment and never run it on your main machine. Dodda also says that code can be checked by simple AI prompts, so it's important to always check before running it. Dodda also warns that you shouldn't let your guard down just because a social media profile looks authentic or you can confirm that the company is a real one.
When Dodda's blog became a hot topic on Hacker News, several comments were made pointing out that 'his LinkedIn profile looks completely inauthentic, so it should have been obvious.' However, one issue that has been raised is the presence of a Persona verification badge on the LinkedIn profile. The presence of a Persona badge indicates that identity verification using a form of ID has been performed. The fact that the profile is being used for fraud suggests that there is a security issue with the Persona verification system, and that fraud is being perpetrated using the Persona verification badge. Dodda's blog contains many characteristics typical of AI-generated text, leading many on Hacker News to question whether this was actually a real-life incident. However, Dodda himself responded directly on Hacker News, pointing out the Google Doc he had prepared before writing the blog on Claude, which led to the case being praised as a real and interesting example.
Related Posts:
in Security, Posted by log1e_dh