The US Department of Justice announced that it has completed the removal of the malware 'PlugX' set by Chinese hackers 'Mustang Panda' and 'Twill Typhoon'

On January 14, 2025, the U.S. Department of Justice (DOJ) announced that it had completed the removal of the malware 'PlugX' that was installed on more than 4,200 computers by the Chinese government-backed hacker groups 'Mustang Panda' and 'Twill Typhoon.'
plugx_affidavit.pdf
(PDF file)
Office of Public Affairs | Justice Department and FBI Conduct International Operation to Delete Malware Used by China-Backed Hackers | United States Department of Justice
https://www.justice.gov/opa/pr/justice-department-and-fbi-conduct-international-operation-delete-malware-used-china-backed
US removes malware apparently planted on computers by Chinese-backed hackers | Reuters
The remote access Trojan 'PlugX' has a long history and has been confirmed to have been used in targeted attacks since around 2008. According to court records filed in the U.S. District Court for the Eastern District of Pennsylvania, the Chinese government provided funding to Mustang Panda and Twill Typhoon to develop a version of PlugX that added a 'worm function' to spread infection via USB drives.
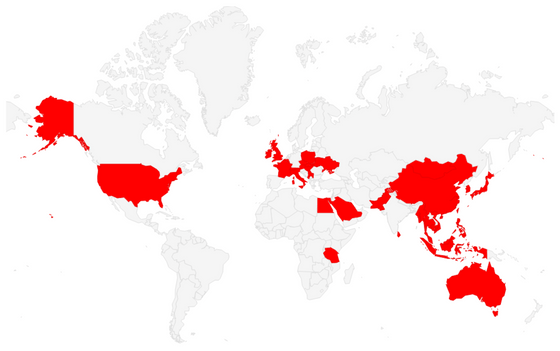
Since 2020, the number of cases of infection with the worm-function-added version of PlugX has increased . The map below shows countries and regions where infections have been confirmed as of July 2023 in red, with infections confirmed in Japan, the United States, the United Kingdom, France, and other countries.
However, in September 2023, cybersecurity company Sekoia
In the United States, the DOJ and FBI began working together to remove PlugX from victim computers in August 2024. On January 3, 2025, the DOJ announced that PlugX had been removed from a total of 4,258 computers and networks, marking the completion of the PlugX removal operation in the United States.
In addition, users whose computers have had PlugX removed will receive a notification from the FBI via their internet service provider about the operation.
'This operation underscores the FBI's commitment to using the full range of our legal authorities and technical expertise to combat nation-state cyber threats and protect the American people,' said Brian Von Doran, Deputy Director of the FBI's Cyber Division.

'DOJ is committed to aggressively disrupting cyber attacks to protect American victims from harm, while working to apprehend and prosecute perpetrators,' said Assistant Attorney General Matthew Olsen of the Department of Justice's National Security Division. 'Today's successful operation demonstrates our partnerships to counter malicious cyber activity, and I commend the French government and our private sector partners for leading this operation.'
According to the DOJ, the FBI continues to investigate Mustang Panda and Twill Typhoon computer intrusion activities. FBI Special Agent Wayne Jacobs said, 'The FBI has identified and removed thousands of PlugX-infected computers in the United States. This operation demonstrates the FBI's determination to track down the Chinese government's attackers, wherever they may be targeting Americans.'
Related Posts:
in Security, Posted by log1r_ut







