Ransomware group 'Qilin' releases about 400GB of information including confidential information of hospital patients, victimized NHS refuses to pay ransom of 8 billion yen

On June 3, 2024, the Russian cybercrime group 'Qilin' carried out a ransomware attack targeting medical institutions in the UK, causing difficulties for several medical institutions in providing care to patients. It has now been revealed that Qilin has published approximately 400GB of personal information stolen from medical institutions on the dark web.
Synnovis cyber incident - NHS England Digital
Synnovis cyber incident - NHS England Digital
https://digital.nhs.uk/news/synnovis-cyber-incident
Qilin Ransomware Leaks 400GB of NHS and Patient Data on Telegram
https://hackread.com/qilin-ransomware-attack-nhs-patient-data-leak-telegram/
Qilin is a Russian-based cybercrime group that has previously carried out ransomware attacks on all kinds of organizations, including companies and schools. On June 3, 2024, Qilin carried out a ransomware attack on Synnovis , a pathology laboratory that performs blood tests on behalf of the National Health Service (NHS) in London. This resulted in several hospitals in London being unable to perform blood transfusions or surgeries. It is reported that more than 3,000 medical institutions were affected .
Qilin also released a statement saying that it had demanded a ransom of $50 million from Synnovis, but the payment was refused, revealing that Synnovis did not comply with the attackers' demands.
Hackers demand $50 million in ransomware attack on London's health service - GIGAZINE

Then, on Thursday, June 20, 2024, Qilin published approximately 400GB of data, including patient information stolen from Synnovis, on the dark web.

It has also become clear that data is exchanged in chunks on Telegram.

The NHS has acknowledged that the data has been made public, and has already begun analyzing the data in cooperation with the National Crime Agency (NCA) and the National Cyber Security Centre (NCSC). However, the analysis of the data will take several weeks, or in some cases longer, so the details of the data stolen by Qilin have not been made public.
Qilin claims that its cyberattacks against Synnovis were 'in retaliation for the UK government's involvement in an unspecified war', but cybercrime expert Graham Cluley has questioned this claim, saying 'Qilin has never claimed political motives in any of its previous cases'.
Cluley also cited the reasons why Synnovis was chosen to deal with ransomware attacks: 'Public healthcare organizations have complex IT systems and limited budgets, which make them vulnerable to security vulnerabilities. When healthcare organizations fall victim to ransomware attacks, it has a direct impact on human lives. For this reason, cybercriminals believe that it is easier to negotiate ransoms with healthcare organizations.'
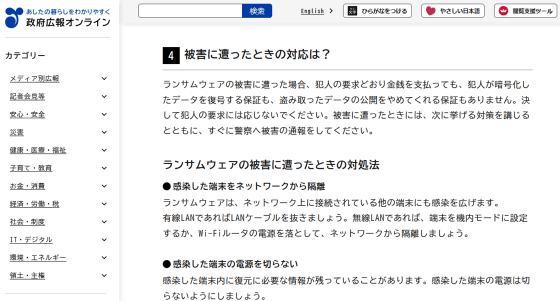
If you are attacked by ransomware and are asked to pay a ransom, the correct response is to 'not pay the ransom.' For example, a government public relations bulletin about ransomware clearly states, 'If you are a victim of ransomware, even if you pay the money as demanded by the criminals, there is no guarantee that they will decrypt the encrypted data or stop publishing the stolen data. Never comply with the criminals' demands.'
Ransomware, is your company also a target? What to do to prevent damage | Government Public Relations Online
https://www.gov-online.go.jp/useful/article/202210/2.html#fourthSection
In addition, the JPCERT Coordination Center (JPCERT/CC), a non-profit organization working to improve cybersecurity in Japan, also explains that you should not pay the ransom even if you are the victim of a ransomware attack for the following reasons:
There is no guarantee that encrypted files can be restored.
・The cause of the damage and other damage caused by the infringement remain unresolved
・There is a risk of being victimized by another attack or being asked to make a payment after making a payment.
・Paying ransom to the attacker may encourage further attacks.
In addition, JPCERT/CC also states, 'Even if you receive a threatening or proposing message from an attacker, you should not only not respond, but also not consider negotiating.' The following page summarizes how to respond if you are the victim of a ransomware attack, so please check it out.
FAQs to read if you are hit by an intrusive ransomware attack
https://www.jpcert.or.jp/magazine/security/ransom-faq.html
Related Posts:
in Security, Posted by log1o_hf






