Summary of DNS settings to prevent emails from being sent from domains you do not use

When sending an email, you can write anything you want in the 'From' field, so it's easy to spoof someone else. When someone sends an email spoofing a domain you own, engineer Vivek Gait explains how to set up DNS to tell the recipient that the email is a 'spoofed email.'
DNS settings to avoid email spoofing and phishing for unused domains - NixCraft
Gaito's explanation is about how to set up 'domains that do not use email' to tell them that 'the domain will not send emails' and that 'if emails are received from that domain, it is a spoofed email sent by a malicious person.' Therefore, it is important to note that if you set it up for a domain that actually sends and receives emails, you will not be able to use email normally.
1: Setting up a null MX record
The DNS MX record is a record for delivering emails to the correct server. You can check it with commands such as 'host' and 'dig' as shown below.
[code]host -t MX [target domain]
dig MX [domain]
dig +short MX [domain of interest][/code]
When the above command was entered into the domain 'cyberciti.biz' operated by Gaito, the results were as shown below.
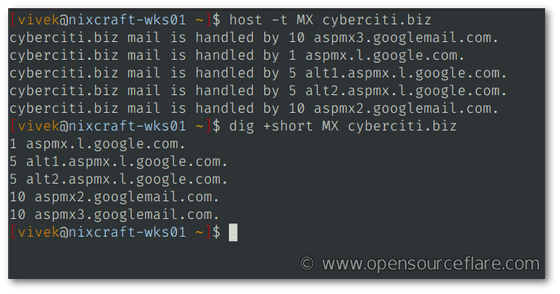
If there is no MX record, the A record will be used instead of the MX record, so it will not be possible to tell that 'the mail server does not exist.' On the other hand, if you set 'Null MX,' it will correctly tell you that 'the mail server does not exist.'
To set a null MX, simply set the MX record with a priority of '0' and a '.'. For example, to set it for the domain 'opensourceflare.com' owned by Gaito, it will look like this:

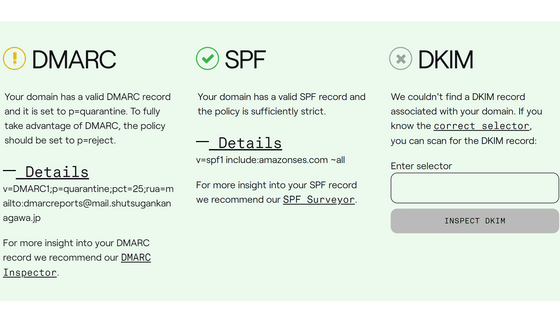
◆2: Setting up SPF
SPF is an abbreviation for Sender Policy Framework, and is one of the mechanisms for preventing domain spoofing. Using SPF, you can inform the recipient of the correct sending server of the email. For example, by setting it up as shown below, it means that only emails sent from IP addresses included in 'amazonses.com' and '_spf.google.com' among those sent using the 'cyberciti.biz' domain are correct.
[code]cyberciti.biz descriptive text 'v=spf1 include:amazonses.com include:_spf.google.com ~all'[/code]
If you don't send emails from a domain, just set the TXT record as shown below. All emails sent from this domain will fail the SPF check, letting the recipient know that the email is suspicious.
[code]'v=spf1 -all'[/code]
However, what SPF checks is the legitimacy of the 'envelope From' that shows the actual sender of the email, not the 'sender (from)' field that users generally see. However, by preventing spoofing of the envelope From, it is possible to prevent
3. Setting up DKIM
DKIM is a mechanism that uses public key cryptography to prove that 'the email was sent from the domain listed in the DKIM header' and 'that the email has not been tampered with on the way.' By registering a private key on the mail server and digitally signing all emails, and registering the public key in a DNS TXT record, the recipient can verify the digital signature using the public key of the domain that sent the email. An example of an actual DKIM record is shown below.
[code]google._domainkey.cyberciti.biz descriptive text 'v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAlXtL1tL+0WrwdEldIO0ZED1hmaQJ9AcAA/eN3wMDUd723+MSR+vIqOrp2Bu5rKIPvm3IdADx+Av5UGmQ1UwU/TuJR+T+p5nW9bymUgJGqM8pp+Pg+YPsD4EEu+ClBwt8gExE6BYM/CK17djlrBnv9vbzUkK9IvhGr1UggUaz9N3BDCPRq/0PAhDYiwm18QN+s' 'S8j8I3Iuv25oSUz20NYQ2R4PEZFN6dQcPuuwYCC0Ntjip2r/vonwv4LBFgqjEBJfyeuPlGiE+KagxtAI5s1lvIGNGw937vT5FkpmMXe0czJKrKEm0j/RiKb1fgYbjGJndX9x2uNELcqCwP2NQ06PwIDAQAB'[/code]
For example, if a domain that does not send email, such as opensourceflare.com owned by Gaito, sets up a DKIM record as shown below, all emails sent using that domain will fail the DKIM check.
[code]*._domainkey.opensourceflare.com.1 IN TXT 'v=DKIM1; p='[/code]
Successful DKIM authentication ensures that the email was sent from the domain listed in the DKIM header, but does not check the domain listed in the 'From' field like SPF does. Therefore, SPF and DKIM alone cannot prevent spoofing, but these two factors can be used to set up DMARC as follows:
◆4: DMARC settings
DMARC is a mechanism to check whether the domain used in SPF and DKIM matches the 'sender' domain. You can also decide how to handle emails when SPF and DKIM checks fail, and request that the mail server send a report when the check fails. For example, in the case of opensourceflare.com, it is as follows.
[code]_dmarc.opensourceflare.com.1 IN TXT 'v=DMARC1; p=reject; sp=reject; adkim=s; aspf=s;'[/code]
'p=reject' tells the server to 'reject' any email that fails the DMARC test, and 'sp=reject' tells the server to reject any email that fails the DMARC test for any subdomain. 'adkim=s' and 'aspf=s' set the DKIM and SPF validation modes to ' strict ', respectively.
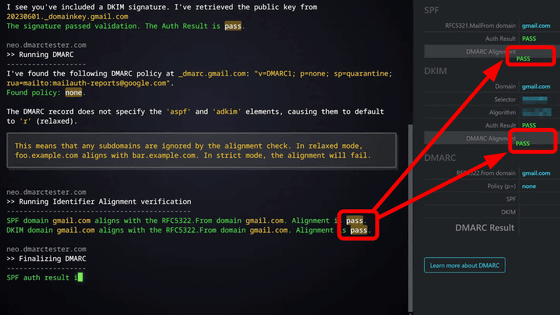
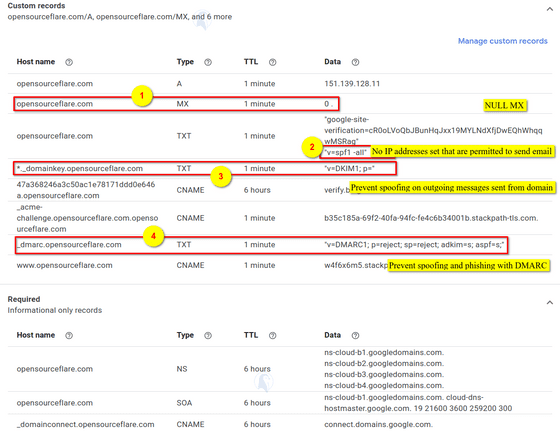
The above four settings are displayed on the Google domain screen as shown below. By configuring these four settings, you can recommend that the receiving server reject all emails sent from your domain, preventing your domain from being spoofed as a spam sender without your knowledge.
Related Posts:
in Web Service, Posted by log1d_ts