'PixieFail' UEFI firmware vulnerability allows attackers in the network to infect devices with malware, a big problem for clouds and data centers

A total of nine vulnerabilities were discovered in TianoCore EDK II , Intel's UEFI reference implementation. The series of vulnerabilities, collectively named ``PixieFail,'' are said to allow an attacker who has infiltrated a network to infect devices within the network with firmware-level malware. Masu.
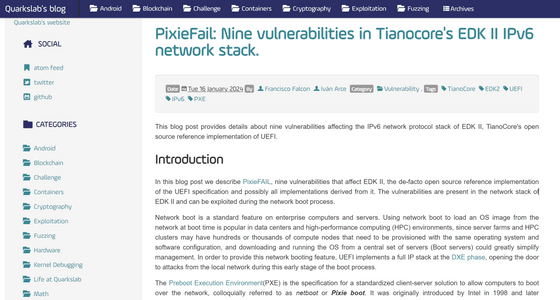
PixieFail: Nine vulnerabilities in Tianocore's EDK II IPv6 network stack.
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
UEFI is a program that runs before the OS boots. The article below contains detailed information.
What exactly is 'UEFI' that replaces the BIOS that runs when the PC starts? -GIGAZINE
In the data center and HPC fields, where large numbers of servers need to be set up, it is common to use network boot to load an OS image from the network at boot time. To provide this network boot functionality, UEFI includes IP communication functionality.
The standard specification for booting a computer over a network is Preboot eXecution Environment (PXE) , developed by Intel in 1998, and PXE is also built into UEFI. In 2010, UEFI version 2.2 was released with support for PXE using IPv6. The vulnerability was discovered this time in the PXE implementation part using IPv6.
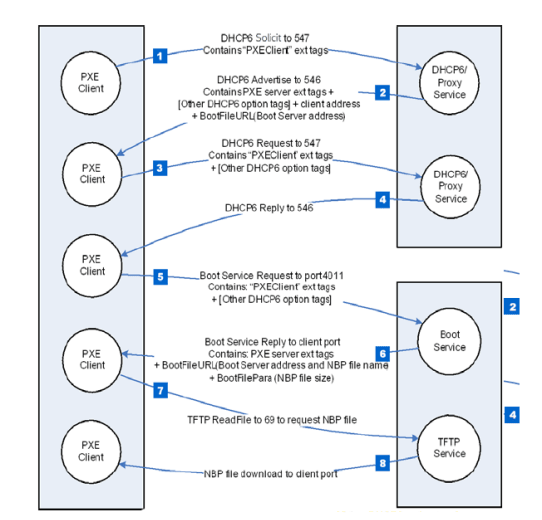
The PixieFail vulnerability allows an attacker to download a malicious firmware image to a server. Since the malicious firmware is installed before the OS and security software, the attacker can secure a permanent foothold on the machine. The research team that reported PixieFail has also released proof-of-concept code.
It is stated that there is no need to establish a malicious server or obtain high-level privileges to carry out an attack; all that is required is access to the local network and the ability to send and receive packets, with no physical access required. . However, since PixieFail targets devices that perform network boot using PXE via IPv6, many general users are not targeted.
The list of nine vulnerabilities that make up PixieFail is as follows.
◆ CVE-2023-45229
Integer underflow when processing configuration contained in DHCPv6 advertisement messages. The CVSS basic value, which indicates the degree of danger, is 6.5 out of 10.
◆ CVE-2023-45230
Buffer overflow in DHCPv6 client. It can be exploited by selecting a server ID option that is too long during what is known as a 'solicit/advertise' exchange in PXE. CVSS base value is 8.3.
◆ CVE-2023-45231
Out-of-bounds reads that can occur during the network discovery phase. CVSS base value is 6.5.
◆ CVE-2023-45232
An infinite loop occurs when parsing unknown options in the Destination Options header. CVSS base value is 7.5.
◆ CVE-2023-45233
An infinite loop occurs when parsing the PadN option in the Destination Options header. CVSS base value is 7.5.
◆ CVE-2023-45234
A buffer overflow occurs when processing DNS server options in DHCPv6 advertisement messages. CVSS base value is 8.3.
◆ CVE-2023-45235
A buffer overflow occurs when processing the server ID option from a DHCPv6 proxy advertisement message. CVSS base value is 8.3.
◆ CVE-2023-45236
Predictable TCP initial sequence number. CVSS base value is 5.7.
◆ CVE-2023-45237
Use of weak pseudo-random number generators. CVSS base value is 5.3.
Related Posts:
in Security, Posted by log1d_ts