The FBI seizes the site of the hacker group 'BlackCat' and distributes the decryption key, claiming that BlackCat is not working, but there is a possibility of fatal damage

The US Department of Justice announced on December 19, 2023 that the site of the ransomware group ``BlackCat'' was seized by the FBI. Although BlackCat has launched a new site and claims that the impact of the seizure is minor, experts say that ``it will be difficult for a ransomware group whose incompetence has been exposed to recover.''
Office of Public Affairs | Justice Department Disrupts Prolific ALPHV/Blackcat Ransomware Variant | United States Department of Justice
FBI disrupts Blackcat ransomware operation, creates decryption tool
https://www.bleepingcomputer.com/news/security/fbi-disrupts-blackcat-ransomware-operation-creates-decryption-tool/
FBI developed decryptor for BlackCat ransomware, shut sites • The Register
https://www.theregister.com/2023/12/19/blackcat_domain_seizure/
FBI developed decryptor for BlackCat ransomware, shut sites • The Register
https://www.theregister.com/2023/12/19/blackcat_domain_seizure/
BlackCat is a ransomware group also known by names such as 'ALPHV' and 'Noberus,' and has been reported to have attacked Bandai Namco HD group companies and bulletin board social news site Reddit in the past. Masu.
Bandai Namco HD group company may have suffered a cyber attack and customer data may have been leaked - GIGAZINE

In the 18 months since BlackCat began its operations, it is estimated that hundreds of millions of dollars (tens of billions of yen) in ransom have been extorted from more than 1,000 victims, and the US Department of Justice has said, ``BlackCat is a global It is a variant of ``Ransomware as a Service (RaaS),'' which caused the second most damage in the world.
In a statement, the U.S. Department of Justice announced that the FBI was able to infiltrate BlackCat's servers, monitor its activities, and capture the decryption key. The FBI developed a decryption tool based on the decryption key stolen from BlackCat and provided it to dozens of ransomware victims both domestically and internationally. According to the US Department of Justice, this has prevented the victim from suffering a total of 68 million dollars (approximately 10 billion yen) in ransom.
At the same time, the FBI says it also destroyed BlackCat's infrastructure, and multiple media outlets have confirmed that BlackCat's site on the dark web has been taken offline.
Below is a seizure notice displayed on the Tor blog that BlackCat used to publish victim names and specify how to pay the ransom. According to the notice, the seizure of BlackCat's servers was carried out in coordination with Europol, EU countries, and Australian law enforcement authorities.

The US Department of Justice is offering a reward to anyone who provides additional information about BlackCat, and is calling on victims who have not yet come forward to receive recovery assistance.
Meanwhile, BlackCat claimed in a Russian-language statement on its newly established site that the seized sites had been 'liberated' by them. According to BlackCat, investigative authorities were able to access the decryption key for about a month and a half, and 400 victims were eligible for relief, but as a result, 3,000 victims were unable to receive the decryption key. It is said that they are no longer able to receive discounts on ransom payments.
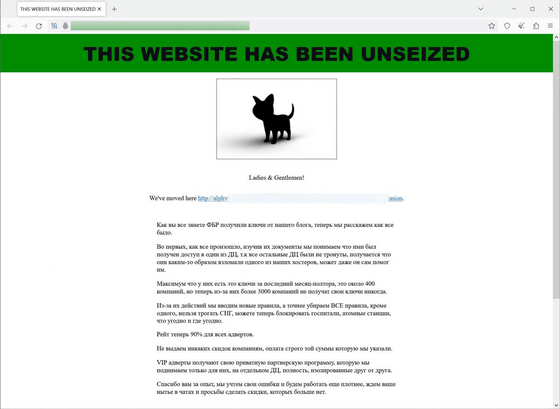
The majority of BlackCat's members are believed to be in Russia, and as Russia is beyond the reach of Western investigations, foreign media Axios points out that it is nearly impossible to arrest the perpetrators. Therefore, there is a good chance that BlackCat will relocate and resume operations, or that BlackCat members will establish a ransomware group under a new name.
However, many experts have expressed the opinion that it is difficult for cyber criminals to maintain the same level of influence once they have allowed reverse hacking by law enforcement authorities.
'No one will be surprised to learn that ALPHV is a bunch of lying scum. They haven't 'released' anything,' ransomware researcher Alan Liska said on X (formerly Twitter). He pointed out that BlackCat's statement was a bravado.
It will surprise no one to learn that ALPHV are lying pieces of shit. They didn't 'unseized' anything.
— Allan “Ransomware Sommelier????” Liska (@uuallan) December 19, 2023
The way .onion addressing works is that, as long as you have the signing key, if you register a second server with that address the newest server will be believed by default. https://t.co/88Fqc35Fnr
Alexander Leslie, an analyst at the security firm Recorded Future, said, ``As long as ALPHV has the private key, you can still access the blog, which shouldn't come as a surprise. In other words, this 'counterattack' is nothing more than ALPHV's attempt to double down and save face.''
Okay, clown time over. This reeks of desperation.
— Alexander Leslie (@aejleslie) December 19, 2023
As long as ALPHV retains their private keys, they'll still have access to the blog. They could also spin up a second server. It's not some incredible feat of intellect.
The commission restructuring is obviously intended to… https://t.co/Y2wa5Bhw7a
Brett Callow, an analyst at security firm Emsisoft, told the overseas media The Register, ``ALPHV's criminal partners will have to suspect law enforcement of honeypots in the future. 'There are very few criminals who would want to continue working with an incompetent organization that has a history of being dismissed by law enforcement agencies. The risk is too high.'
Related Posts:
in Security, Posted by log1l_ks







