How can I get my domain back if suddenly my domain is seized by a government agency?

A domain is like an address on the Internet, and it will always be used when providing some kind of service on the Internet. The situation that 'the domain falls into the hands of others' is a big incident that suddenly makes the house belong to someone else, but until Mr. Susam Pal, who has the experience of suddenly losing the domain, regains it I have a record on my blog.
Sinkholed: A DNS Horror Story - Susam Pal
Mr. Pal was hosting his website on the domain 'susam.in'. The incident occurred at 14:58 on November 26, 2019, and the ownership of the domain suddenly moved to another person without any warning. Mr. Pal was performing website maintenance until a few minutes before this time, and it was three days later that he realized that he had lost domain ownership because the DNS data was cached in the system.
At 19:00 on November 29, 2019, Mr. Pal noticed that his domain was associated with a completely unknown address and checked the WHOIS record. The WHOIS records at that time are as follows. The registrar has changed from 'eNom, inc.' to 'NIXI Special Projects', the registrant has been changed from 'Susam Pal' to 'The Verden Public Prosecutor's Office (Felden Public Prosecutor's Office)', and the name server is also used by Mr. Pal It has been changed from Linode to Shadowserver's Sinkhole .
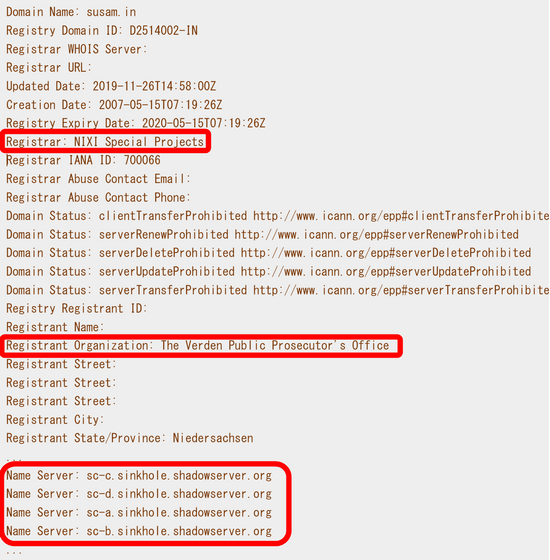
When Pal investigated the new owner, the Verden Public Prosecutor's Office, it turned out to be a German criminal justice agency that was working to take down the network of the phishing group

Mr. Pal thought that the server hosting the site may have become part of the Avalanche botnet, and also investigated whether there was any evidence of an attack. However, even after checking all the logs, there was no evidence that anyone other than Mr. Pal logged into the server or executed any code or command on the server, and no trace of malware could be found.
At 19:29 on November 29, 2019, Mr. Pal sent a support ticket to Namecheap, his contracted registrar. At 21:05, Namecheap replied that they had contacted Enom, a higher registrar, but did not give us an estimate as to when the issue would be resolved.
Mr. Pal also contacted
Mr. Pal posted about this issue on Twitter at 7:30 on November 30, 2019, and at 9:54, Namecheap's CEO replied to the tweet, ``I am contacting NIXI.'' there was.
My domain https://t.co/iWuUYx7h3o has been transferred to another registrant without authorization/notification. I owned this domain for 12 years and now it's gone without any warning. @Namecheap provides no ETA about investigating this. See https:/ /t.co/UxwsEVTbXT for details.
— Susam (@susam) November 30, 2019
At 11:43 on December 1, 2019, an email was received from the Shadow Server Foundation. According to the email, the Shadow Server Foundation began an investigation immediately after being contacted by Mr. Pal, and confirmed that the domain was seized by mistake during the Avalanche destruction operation. In the Avalanche botnet destruction operation, the `` Sinkhole '' technology that confiscates the domain used by the botnet and redirects it to a safe address was used, but even after three years have passed since the destruction operation was carried out , Acalanche is still active, and more than 3.5 million IP addresses have been confirmed to connect to domains within Sinkhole.
In Mr. Pal's case, the domain pattern of the command and control server used by Nymaim, one of Avalanche's malware, was applied to 'susam.in', and it slipped through the validity check to avoid false positives. Therefore, the domain was confiscated by Sinkhole.
When Mr. Pal checked the WHOIS record at 4:00 on December 2, 2019, he found that 'susam.in' had already been returned. At 8:37, I was formally informed by Namecheap that the domain had been restored to its original state.

Although the domain was returned safely, Mr. Pal could not return very calmly considering the possibility of suddenly losing the domain. The blog says, ``I thought there would be more checks before the domain was actually transferred,'' and ``Losing the domain I had been using for 12 years was a very unpleasant experience.''
In addition, Mr. Pal asked the Shadow Server Foundation whether the reliability differs between country code domains such as '.in' and general-purpose domains such as '.com'. . A representative of the Shadow Server Foundation said that NIXI, which manages '.in', has a very clean operation and the number of days until the problem is resolved is short, and '.com' is more problematic due to the domain generation pattern of malware. I also answered that it might be easier.
In addition, Mr. Pal changed the domain of his blog from ``susam.in'' to ``susam.net'' in 2022. says.
Related Posts:
in Note, Web Service, Posted by log1d_ts







