Clearly that malware 'W4SP' targeting developers is installed in PyPI's malicious package

More than 20 packages in the
Phylum Discovers Dozens More PyPI Packages Attempting to Deliver W4SP Stealer in Ongoing Supply-Chain Attack
https://blog.phylum.io/phylum-discovers-dozens-more-pypi-packages-attempting-to-deliver-w4sp-stealer-in-ongoing-supply-chain-attack
According to security firm Phylum, it has discovered dozens of newly released PyPI packages that attempt to deliver W4SP to Python developers' machines. They were hiding malicious '__import__' functions in other healthy codebases.
An early package looks like this, where you can see the function hidden on line 40.
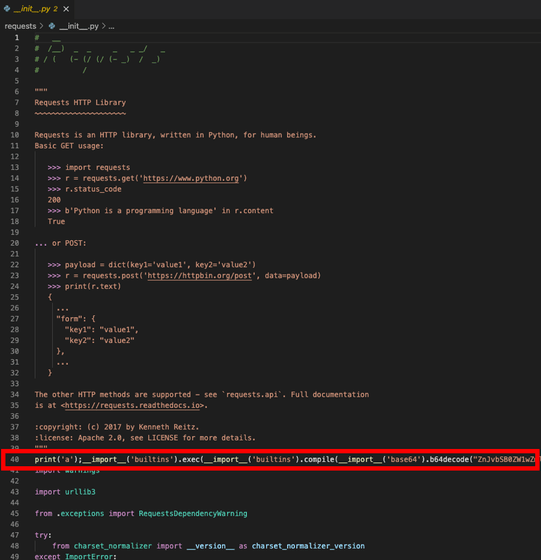
Later, when the attacker learns that the above method will be countered, he hides the malicious code in a place where it cannot be seen at first sight. The following is the screen after the countermeasure, but at first glance it seems that there is no change.
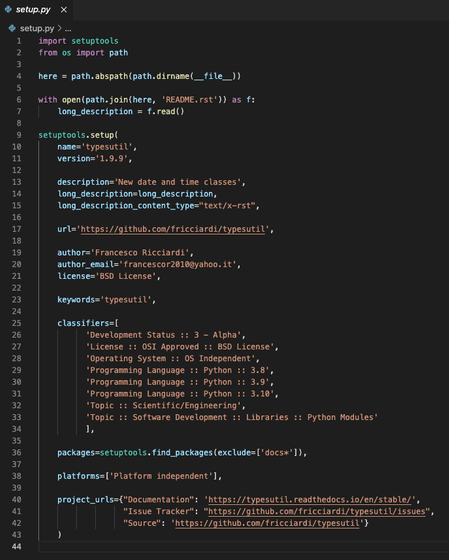
However, if you expand the window of the code editor and see the whole, you can see that the code is inserted in a position that is difficult to see by using a lot of spaces. When Phylum counted, 318 spaces were inserted.
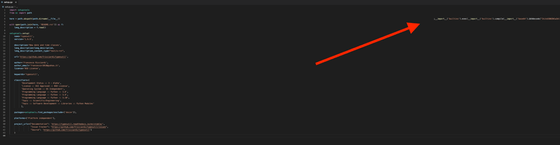
Modules loaded this way contain strings encoded in Base64. The string contains a script that executes a temporary file, allowing it to reach arbitrary URLs and retrieve W4SP. Phylum points out that the code is obfuscated and difficult to understand at first glance.
The main attacks began around October 12, 2022, gradually gained momentum, and were concentrated around October 22. According to PyPI download counter pepy.tech, the malicious packages have been downloaded more than 5,700 times. “We expect to see more malware like this in the near future, as these attacks are ongoing and attackers are constantly changing their tactics,” Phylum said. We will continue to discover and elucidate further.'
Related Posts: