The filter 'EasyList' used by 99.99% of ad blockers is undeliverable due to DDoS attack

AdGuard, a major ad blocker, has reported that the filter '
EasyList is in trouble and so are many ad blockers
https://adguard.com/en/blog/easylist-filter-problem-help.html
According to AdGuard, EasyList is a very major filter list for ad blockers, and 99.99% of ad blockers, including the company's products, use EasyList or its derivatives. However, if you access the EasyList list at the time of article creation, it will take several minutes to load, or in the worst case it will time out.
AdGuard is also facing a problem of a 10 to 20-fold increase in traffic from around November 2021, and after conducting an investigation, it was found that the cause was two types of browsers equipped with an ad blocking function. .
Here's how it looked like in the CF panel. With how things were and considering the growth, we would hit 2.5-3PB for November. But how in the world we could use THAT MUCH bandwidth?
— Andrey Meshkov (@ay_meshkov) November 24, 2021
(3/11) pic.twitter.com/nTaEquSIJu
The browser in question is derived from a very popular browser in India and suffers from a flaw that 'attempts to download filter updates every time it launches'. As a result, EasyList was accessed every time the user of the browser started the browser, resulting in a situation similar to a DDoS attack.
AdGuard, which identified the cause, took measures to block unwanted app traffic, but said that it had to return 100 TB of 'Access Denied' errors every month. thing.
EasyList is hosted on Github and proxied by CloudFlare, but CloudFlare does not allow non-enterprise users to use large amounts of traffic, so requests to EasyList's files are limited, and this is EasyList's It is the cause of the situation where it is difficult to access the text file.
The EasyList team contacted CloudFlare and asked for cooperation, but there was no island to attach. And since EasyList is a community project powered by volunteers, I can't afford to subscribe to CloudFlare's enterprise plan.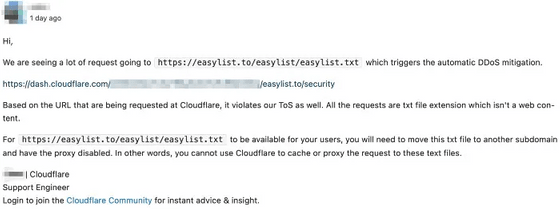
AdGuard has been redeploying filter lists on their own servers for some time, so AdGuard users are not directly affected by this issue. Also, other ad blockers are already getting their filters from mirror domains, or will be switching over in the near future. However, if the problematic app detects new access destinations and is flooded with access, it ends up being a cat-and-mouse game.
In this regard, AdGuard said, ``If you are a security researcher, it would be very helpful if you could find an Android browser that has DDoS attacks on EasyList and AdGuard filters. I contacted the developer, but the problem has not been solved and is getting worse, so there are probably more browsers, ”he asked experts for cooperation.
In addition, it is said that the URLs where access is concentrated are the following three cases.
・https://easylist.to/easylist/easylist.txt
・https://filters.adtidy.org/extension/ublock/filters/2_without_easylist.txt
・https://filters.adtidy.org/extension/ublock/filters/11.txt
Related Posts:
in Software, Posted by log1l_ks