How did anti-fraud experts respond when they received a fraudulent call?

People who are familiar with security and social engineering should think that 'I can not be fooled by fraud', but in reality it is not such a thing and it is said that it is familiar with social engineering. Natasha L reveals it based on her own experience.
As much as we like to pretend otherwise,
infosec professionals are as vulnerable to scammers and social engineering as anyone else. Here's a story about the most sophisticated Wells Fargo / Apple Pay scam I've encountered, which successfully tricked me. t.co/K5HmHxPoJf — Meadow (Natasha L.) (@lupinia) March 31, 2022
Lupinia Studios-I'm a Scam Prevention Expert, and I Got Scammed
https://www.lupinia.net/writing/tech/scammed.htm
One day in the afternoon, I received a phone call to Mr. Natasha. Mr. Natasha hides his real phone number as much as possible by using transfer numbers etc., and although people who know that number rarely call during the day, caller information When I confirmed, it was from
The person on the phone was 'Wells Fargo's Fraud Prevention Officer,' who heard Natasha's name and the last four digits of his debit card number and told him that the card had evidence of fraud. Natasha, who had no idea how to use it in a city 2100 km away, decided that it was an illegal use. A Wells Fargo representative continued, 'Send a new debit card to the registered address.' Natasha thought that this was the end of the response to common fraudulent use, but this was just the beginning.

After the exchange, a Wells Fargo representative told Natasha, 'This fraudulent bill was made with Apple Pay. If you don't use it, you have to turn it off.' Natasha plans to use Apple Pay. After confirming that it wasn't there, I started 'Separating the account from Apple Pay'.
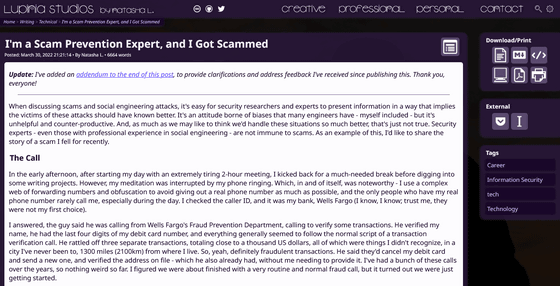
During the work, Mr. Natasha will give the confirmation code sent to the person in charge. The emails I received at that time were as follows. Natasha realized that this was a two-factor verification code that the recipient should enter directly into the verification page, but a Wells Fargo representative said, 'This is part of Apple's system and we The range of access is limited. '
Knowing the technical complexity of the system, Natasha said, 'Apple and Google will put this kind of pain on banks in removing fraudulently added payment methods from their accounts,' and 'Wells Fargo in the first place.' Because the system is sloppy, I think he's a good person even with such a terrible method. ' I heard you told me.
After proceeding to this point, Natasha remembered two catches. First, a text message about unauthorized use had arrived in advance at the mobile phone number that I usually use, which is different from the mobile phone registered with Wells Fargo.
Second, I received an email from Apple Pay saying that I registered my card number while I was communicating. Regarding the email, a Wells Fargo representative replied, 'I think the old email was left on the server,' but Natasha received the 'delayed email' shortly after giving the verification code. I felt that it was too good by chance.
When Natasha finally realized that the other person wasn't calling her name, Wells Fargo's person in charge revealed that her employee number was '1687979' by calling herself 'Daniel Coffman', so if you're worried. I told Natasha that I would replace my boss. Natasha went further with suspicion, partly because Daniel was very familiar with Natasha's information and wanted to end the conversation early.
After completing the 'separation of account and Apple Pay,' Daniel asked Natasha, 'Did you log in to online banking from a city that was abused?' Natasha was prepared to deal with this kind of thing immediately, so she immediately logged in to online banking to make sure that no one had changed her password, and then changed her password. At this time, Natasha was overwhelmed by changing passwords and checking transaction history, and did not think deeply about the address, card information, account balance, year of birth, last four digits of the Social Security number, etc. that Daniel asked. It seems that he answered.

While Daniel was supporting online banking, Natasha was checking the transaction history of her account, and in front of her, a new transaction of $ 150 (about 18,000 yen) by Apple Cash appeared. Daniel replied, 'It's another fraudulent transaction and will be removed like any other,' but Natasha recalls the advice she gave to those who encountered suspicious situations. I went down and checked the situation with a critical eye.
As a result, Daniel thought that 'the fraudulent use of debit cards and the unauthorized login to online banking where no one should know the password can occur at the same time', but Daniel is a scammer. I wasn't convinced that 'this phone is a fraud' because I was so familiar with Natasha's information that I thought it wouldn't be strange for a person at a financial institution.
So Natasha asked Daniel, 'Can I call customer service and continue with this deal with Daniel's ID?' Wells dislikes Natasha's answer, 'Because it's before the process is complete, the entire checking account will be frozen for confirmation in 7-10 business days unless you go to the branch.' It was consistent with Fargo's 'ridiculous policy', but it wasn't a hint as it was also a basic tactic for fraudsters to panic and impatient their opponents.
But here Daniel asked Natasha to confirm her 'full date of birth and full social security number.' Since this information is highly confidential personal information, we use key touch tones when making a call. The key touch tone seems safe because it is not direct information, but in reality it is possible to identify which button was pressed by decoding the sound.

Deeply suspicious, Natasha asked Daniel if he was planning to transfer it to some department when he entered the number, or if he intended to transfer it to an automated system, but Daniel said, 'There is no need to transfer. You can start typing at any time. ' According to Natasha, the frequency used by the key touch tone is close to the frequency of human voice, so audio processing is required when inputting, and I heard about the mechanism of the call center that allows seamless input while talking to the person in charge of the telephone. He said he had never done it.
After a few more questions, Natasha deliberately entered a different date of birth and social security number. During Daniel's 'Please wait for the system to process the request' instruction, another phone call to Wells Fargo and there is no history of the first abuse. , I have confirmed that there is no person named Daniel Coffman with employee number 1687979. During this work, Daniel occasionally reported progress to Natasha, saying, 'The processing work is in progress,' but at the same time, another fraudulent transaction was taking place, and a real Wells Fargo representative. It seems that 800 dollars (about 100,000 yen) was protected by.
After that, Mr. Natasha, who changed his policy to 'I can not cheat money from fraudsters, but at least waste time', asked Daniel about the contents of the confirmation work so far, and when there was no more material, Daniel was asked. I asked him to take the place of my boss. Then Daniel switched to hold with 'willingness' and said that the phone was hung up without being connected.
Based on his own experience, Natasha said, 'If you feel that an ongoing call / dialogue is suspicious, it is important to get external confirmation as soon as possible. If you cannot use multiple phones, put the other party on hold. You can also borrow a phone or use text chat. Ask questions if you have any doubts. Even if the other person answers all the questions, keep asking questions until you are satisfied. The most skilled and prepared Even if you're a scammer, you'll eventually run out of answers. If you suspect that the other person isn't honest, remember that you're not obliged to be honest. Take a look, especially if the information is genuine and should be immediately available. '
He also sends a message to 'Daniel Coffman' who called himself, 'No matter who you are, you did very well.'
Related Posts:
in Security, Posted by logc_nt