Samsung gets hacked 190GB of sensitive data

Hacker group Lapsus $ has announced that it has stolen 190GB of sensitive data from Samsung and leaked it over the Internet. Lapsus $ just
Hackers leak 190GB of alleged Samsung data, source code
https://www.bleepingcomputer.com/news/security/hackers-leak-190gb-of-alleged-samsung-data-source-code/
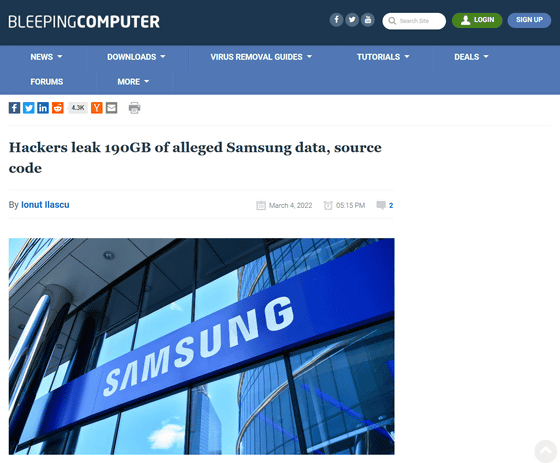
Lapsus $ has released screenshots of C language and C ++ directives among the confidential data stolen from Samsung, and appeals that the stolen data also includes 'Samsung's confidential source code'.
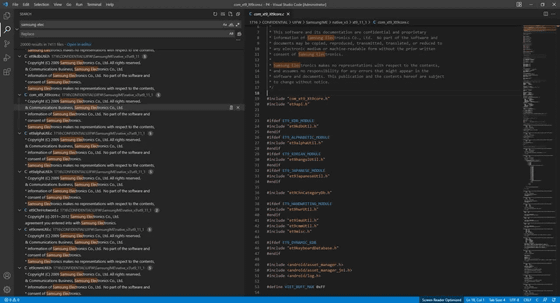
Lapsus $ explains the stolen Samsung sensitive data as follows. 'If the following details are accurate, Samsung is suffering from a serious data breach that could cause tremendous damage to the company,' said Bleeping Computer, a technology media company.
· Source code for all Trusted Applets (TAs) installed in Samsung's TrustZone environment used for sensitive operations (hardware encryption, binary encryption, access control, etc.)
-Algorithm for unlocking all biometric locks
-Boot loader source code used in all recent Samsung devices
・ Qualcomm's confidential source code
・ Samsung activation server source code
· Complete source code for technologies used to approve and authenticate Samsung accounts, including APIs and services
Lapsus $ divides the stolen data into three compressed files, puts them together in a folder of about 190GB, and shares them on torrents. Lapsus $ describes the data in three parts: 'Part 1 contains source code and related data dumps for security / defense / knocks / bootloaders / trusted applications and various other items.' 2 contains source code and related data dumps for device security and encryption. ”“ Part 3 contains various GitHub repositories by Samsung. Mobile Defense Engineering and Samsung Account Backend, Includes pass backend / frontend, SES (Bixby, Smartthings, store), etc. '
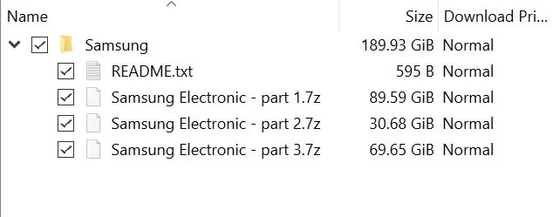
Bleeping Computer has asked Samsung to comment on the data breach, but it hasn't received a response at the time of writing the article.
Related Posts:







