Backdoor malware 'SysJoker' targeting Windows, macOS, and Linux is reported

Security company Intezer reports that a multi-platform backdoor malware 'SysJoker ' targeting Windows, macOS, and Linux has been discovered. In December 2021, an attack by SysJoker was confirmed on a Linux-based web server.
New SysJoker Backdoor Targets Windows, Linux, and macOS --Intezer
New SysJoker backdoor targets Windows, macOS, and Linux
https://www.bleepingcomputer.com/news/security/new-sysjoker-backdoor-targets-windows-macos-and-linux/
SysJoker is coded in C ++, and the variants are made according to the target OS. VirusTotal , an online malware scanning site that uses 57 antivirus detection engines, did not detect all of SysJoker, including variants.
On Windows, a DLL-style
SysJoker then uses a technique called Living off the Land to collect information such as MAC addresses, IP addresses, user names, and physical media serial numbers. It uses a text file to record the results, then stores it in a json object, deletes the text file, encodes it, and writes it to a file called 'microsoft_Windows.dll'.
The following shows a json object written to memory by SysJoker.
After collecting the data, SysJoker adds a new registry key called 'HKEY_CURRENT_USER \ Software \ MicrosoftWindows \ CurrentVersion \ Run' to make the
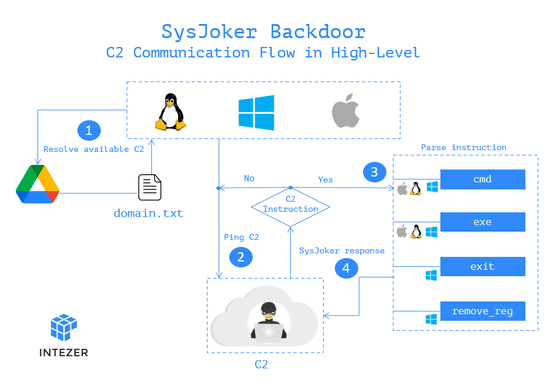
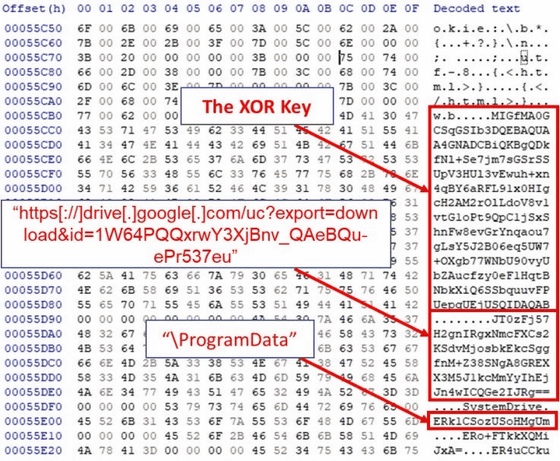
SysJoker then accesses the hard-coded Google Drive link in the SysJoker source code to access the C2 server. A 'domain.txt' that summarizes the list of C2 servers has been uploaded to this Google Drive and is updated regularly by attackers.
The information initially collected by SysJoker is
Bleeping Computer, a technical news site, summarizes trace information for detecting SysJoker for each OS as follows.
◆ Windows
The SysJoker files are stored in 'C: ProgramData %% igfxCUIService.exe' and 'C: ProgramData %% microsoft_Windows.dll' in the 'C: ProgramData \ RecoverySystem' folder. SysJoker creates an autorun setting called 'igfxCUIService' for persistence and launches a malware executable file called igfxCUIService.exe.
◆ macOS
The SysJoker file is created in '/ Library /' and persisted under '/Library/LaunchAgents/com.apple.update.plist' via LaunchAgent.
◆ Linux
SysJoker files and directories are created under '/.Library/' and are made persistent by creating the following cron job.
[code] @reboot (/.Library/SystemServices/updateSystem) [/ code]
Bleeping Computer also advises you to take the following steps if you find yourself infected with SysJoker.
1: Kill all malware related processes and manually delete SysJoker persistence directories and files.
2: Run the memory scanner and make sure all malicious files have been uprooted from your system.
3: Investigate the entry point, check the firewall configuration and update all software to the latest available version.
Related Posts:
in Security, Posted by log1i_yk