The people involved in the ransomware attack are more than just 'perpetrators and victims', what kind of players are forming the ecosystem?

What Is the Ransomware Economy?
https://www.backblaze.com/blog/ransomware-economy/
Ransomware attacks in recent years are no longer limited to a simple 'perpetrator and victim' composition, and a very broad ecosystem has been formed in which various players are involved on both the perpetrator side and the victim side. matter. Backblaze blog writer Molly Clancy points out that understanding the structure and size of the ecosystem is necessary to properly understand the threat of ransomware attacks on businesses and organizations.
Many people may have the impression that cybercriminals are 'a gang of violent gangsters' and 'a group of hackers specializing in expertise,' but cybercriminals in recent years have 'ransomware as a sophisticated business model.' It's an organized crime group that runs the attacks, 'Clancy said. It seems that cyber criminals are not only creating malicious malware, but also paying attention to user experience and customer service, and conducting detailed businesses such as collecting the financial status of customers (attack targets). ..
There are various 'brands' of ransomware, and some ransomware brands such as 'Ryuk ' and ' WannaCry' are very famous. The ransomware brand has been prospering and disappearing with the trend of cyber security, and sometimes the brand is revived.
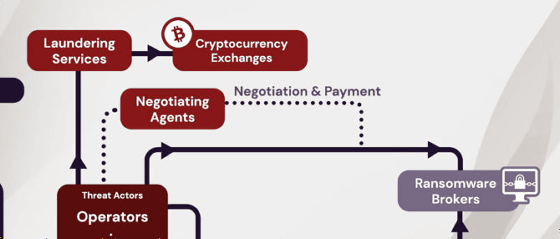
This is a diagram showing the ecosystem of such ransomware attacks. Red and brown are divided by the attacker's player, purple and gray are divided by the victim's player, and you can see that there are various players in both. Especially in recent years, it has become difficult to track attackers because the players of ransomware attacks are decentralized.
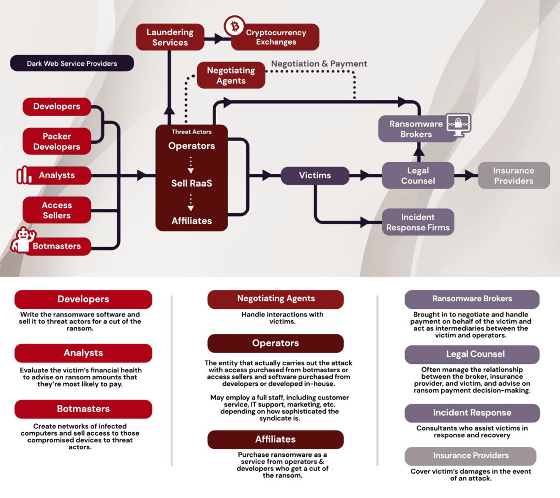
Among the players on the attacker side, the players who are active mainly on the dark web are as follows. As the name implies, 'Developers' are players who create ransomware, sell ransomware to operators who actually perform ransomware attacks, and receive a share of the ransom earned. 'Packer Developers' is a player who develops a protection layer that makes it difficult to detect ransomware attacks, 'Analysts' investigates the financial situation of potential victims and advises who is easy to pay the ransom Players, 'Access Sellers' are players who sell access to the victim's server to operators, and 'Botmasters' are access rights by building a bot network of malware-infected computers. Is a player who sells to operators. These players are just behind the ransomware attack, not the actual ransomware attack.
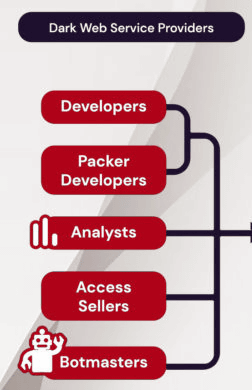
The 'Operators' who actually perform the attack use the ransomware purchased from the developer and the access rights purchased from the access seller or bot master to carry out the ransomware attack based on the advice of analysts and others. I will do it. It seems that some operators sell ransomware attacks as a service to affiliated criminal groups called 'Affiriates', and in recent years criminal groups with low technical capabilities are also conducting ransomware attacks. That thing.
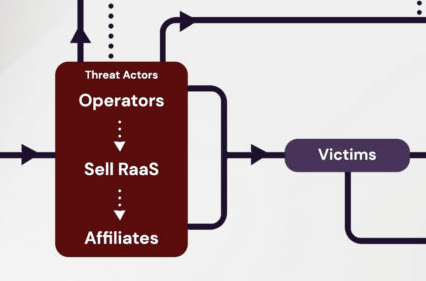
On the other hand, there are various players among the victims who have been attacked by the operator. Victims of ransomware attacks do not necessarily negotiate on their own, but consult with 'Legal Counsel' and introduce 'Ronsomware Brokers' to negotiate with operators. There are cases where you will be asked. In addition, lawyers will contact 'Insurance Providers' to negotiate compensation for the damage caused by ransomware attacks, and 'Incident Response Firms' may also advise victims. matter. Despite being a victim, ransomware brokers and crisis-responders can be considered 'profitable' because they have gained jobs through ransomware attacks.
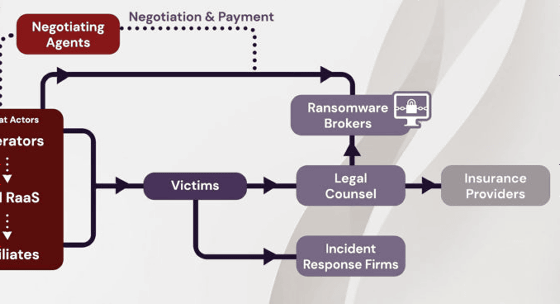
Once the negotiations are finalized between the ransomware broker and the operator, the broker will convert the cash received from the victim into cryptocurrency and transfer it to the operator's 'Negotiate Agents' cryptocurrency wallet. The operator then hands the cryptocurrency to 'Laundering Services', which is converted to fiat currency or other available assets at 'Cryptocurrency Exchanges'. The structure is to return the funds to the operator.
As you can see, the ecosystem surrounding ransomware attacks includes not only the attackers but also the victims. Of course, the cause is on the side of launching the ransomware attack, but Clancy points out that the victim's player who pays the ransom smoothly also has a side to promote the ransomware attack. If you become more confident that you can earn a ransom by attacking, the operator will naturally increase the attack, so paying the ransom will lead to an increase in ransomware attacks. In fact, it has been reported that 80% of organizations that have a precedent of paying ransomware attacks are being attacked by the same group again.
80% of organizations that paid ransom after being attacked by ransomware were attacked for the second time --GIGAZINE

Not all ransomware attacks and ransom amounts paid are publicly available, but analytics firms estimate the damage caused by ransomware attacks by monitoring cryptocurrency wallet transactions associated with operators. .. According to a report released by blockchain analytics company Chainalysis in May 2021, ransomware attacks paid at least $ 406 million in ransom in 2020.
Related Posts:







