The largest hacking activity in history has been carried out in the whole country for a Chinese passenger jet

It is clear that the hacking of the whole country involving many persons such as the Chinese National Safety Department staff, security researchers, enterprise insiders, etc. was done for the aircraft ``
BLOG SERIES_Huge Fan of Your Work
https://www.crowdstrike.com/resources/wp-content/brochures/reports/huge-fan-of-your-work-intelligence-report.pdf
Building China's Comac C919 airplane involved a lot of hacking, report says | ZDNet
https://www.zdnet.com/article/building-chinas-comac-c919-airplane-involved-a-lot-of-hacking-report-says/
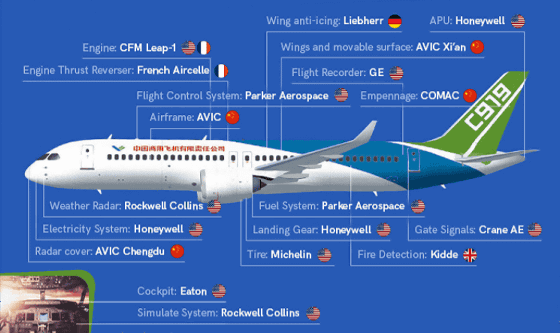
COMAC C919 is a commercial passenger aircraft under development by a private company ' China Commercial Aircraft Limited Liability Company ' established in Shanghai, China. It is said that it will be an aircraft that will compete with Airbus and Boeing when completed. According to CrowdStrike, the biggest hacking in history was done over a period of several years to a company that supplies parts to COMAC C919. As you can see from the diagram below, COMAC C919 has received parts from various companies.
CrowdStrike claims in a report that the
Jiangsu authorities have given instructions to the team manager who actually hacks and the manager who hires internal personnel working at the airline. It is believed that many years of hacking attacks were conducted under these two people.
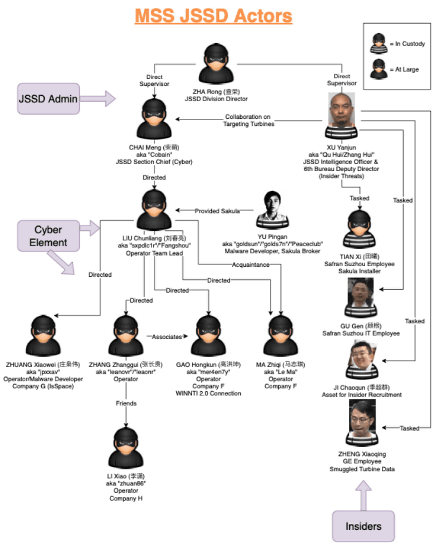
Thanks to this hacking team, information was leaked from C919 suppliers AMETEK , Honeywell , Safran , Capstone Turbine , GE and many others from 2010 to 2015. But the Chinese government did not stop there, but hired regular security researchers and Chinese hackers.
The US Justice Department indictment states that Jiangsu authorities hired a Chinese hacker working in the underground to find the target's internal network and put in malware. Hackers leaked confidential company information to remote servers using malware called 'Sakula' and 'PlugX'. “Sakula” was mainly used by a Chinese security researcher named Yu Pingan.
In rare cases, it seems that hackers could not find a way to enter the target's internal network, but at that time, it seems that a method of hiring staff working at the target company and entering the network via USB was taken .
This hacking team, which CrowdStrike calls “Turbine Panda”, has been unseen by anyone for six years since 2010. The CJ-1000AX engine announced by the China Airlines Motor Group in 2016 is scheduled to be installed in the C919, which had previously used a foreign-made engine, but similarities to the CFM International engine were pointed out It is.
But hackers make mistakes when the target hits the US Human Resources Administration and health insurance giant Anthem . Hackers made massive attacks against the server, stealing sensitive data containing tens of millions of personal information. Hackers succeeded in gaining information about future insiders in this attack, but it caught the eyes of the US government.
Chinese hackers are prosecuted as suspects of `` the worst data breach case ever ''-gigazine

The American government first arrested two hackers who worked as insiders, and then Sakula developer Pingan was arrested at a security conference in Los Angeles. And the arrest of Pingan triggered the existence of hacking activities that the Chinese government was doing. In response, the Chinese government feared that information would be passed on to the US government, and prohibited security researchers from attending security conferences outside of China.
Then, in 2018, a person named Xu Yanjun, who was an employee of Jiangsu Province authorities and hired a foreign company insider, was arrested.

It is the first time that a senior official as high as Yanjun has been arrested in the United States, and at the time of writing the article, Yanjun is engaged in judicial transactions with the US government. On the other hand, 'Many of the cyber operators that made up Turbine Panda will escape prison,' Crowdstrike said. The arrest of Yanjun seems to have stopped Turbine Panda from functioning, but the activities were handed over to another Chinese cyber group. Since C919 has not yet been completed, attacks on airlines from China are expected to continue.
Related Posts: