Google's streaming device 'Chromecast' is hacked and popular YouTuber's advertisement drips
There are bugs that have been abandoned for about 5 years on Google's streaming terminal Chromecast and smart speaker Google Home. A person who has abused this and hacked thousands of Chromecasts has appeared. Attackers point out security problems on hacked Chromecasts and also distribute publicity encouraging popular YouTuber · PewDiePie channel subscriptions.
Thousands of Google Chromecast Devices Hijacked to Promote PewDiePie
https://thehackernews.com/2019/01/chromecast-pewdiepie-hack.html
An unidentified attacker using two Twitter accounts, @ HackerGiraffe and @ j3ws 3 r , hijacked thousands of Chromecast's feeds and displayed a pop-up prompting a security alert and PewDiePie's channel registration on the device.
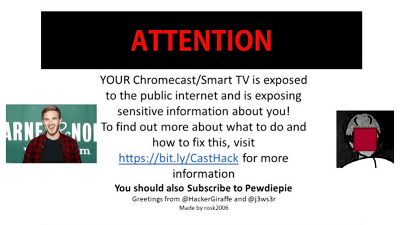
Pop-up with the following image displayed. At the top of the screen is marked as "WARNING" and "Your Chromecast or smart TV is vulnerable in a public Internet environment and it exposes sensitive information about you. To fix the URL please visit the URL below "URL is placed. In addition to this, at the bottom of the pop-up, it says, "You should register the channel of PewDiePie at the same time", you can confirm that the picture of PewDiePie is pasted on the left side of the screen.
The Hacker News of security related news site pointed out "It is the same as the event that hacked more than 50,000 Internet-connected printers around the world that came out at the end of last year and printed leaflets that encourage PewDiePie's channel registration," I guess Chromecast hacks are due to PewDiePie fans.
It is also a problem that fans of PewDiePie are acting extremely to increase the number of subscribers. If you read the following article you can see why such a problem is occurring and what kind of extreme behavior it is taking.
Charisma YouTuber "PewDiePie" fans expanded extreme activities to defend the top number of registrants - GIGAZINE

In this case, I scanned terminals compatible with Chromecast remotely, accessed them via routers that Universal Plug and Play ( UPnP ) was enabled by default, and used bugs left unattended for many years He seems to have done hacking.
Although the URL written on the popup is inaccessible at the time of article creation, it seems that it was in the form of counting the number of hacked Chromecast's terminals as shown below.
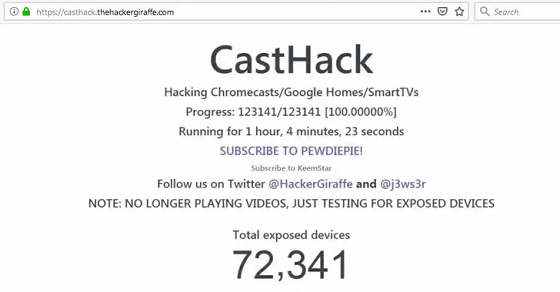
In addition, an attack named "CastHack" is a victim's attack from a device connected to the same Wi-Fi as Chromecast or Google Home, a Bluetooth device paired with Chromecast or Google Home, a Wi-Fi network We can collect all kinds of data. In addition, an attacker can select media to play on a remote hacked device, change the name of the device, reset the device to its factory condition, restart it, and send all Wi-Fi information It is also extremely dangerous to be able to delete or connect to a new network.
The Hacker News pointed out that bugs on Chromecast used by attackers were discovered in 2014 and pointed out that "Google should recognize this, but it has been neglected," and Google's bug We are doubtful about correspondence to.
The user can stop the transfer of the router's port "8008", "8443", "8009", or turn off the UPnP function to avoid the risk that Chromecast will be hacked.
Related Posts: