Protest voice against Australian anti-cryptography law that obliges 'all accessible services' to intercept encrypted communications

by Kobu Agency
In Australia, there is a bill that seeks to be able to intercept encrypted communications for "all accessible services". In response to this bill, the Labor Party of the Australian opposition party is calling for amendment.
Australia now has encryption-busting laws as Labor capitulates | ZDNet
https://www.zdnet.com/article/australia-now-has-encryption-busting-laws-as-labor-capitulates/
Australia's anti-encryption law will merely relocate the backdoors: Expert | ZDNet
https://www.zdnet.com/article/australias-anti-encryption-law-will-merely-relocate-the-backdoors-expert/
In Australia, bills are being considered to allow the encryption of communications to be lifted (intercepted) at the request of government agencies, which is called " anti-encryption method " from intellectuals and media.
The anti-encryption method was already known as its existence as of July 2017.
Australia announces a bill to mandate IT companies to provide access to encrypted communications
https://www.reuters.com/article/australia-security-messages-idJPKBN19Z0HL
Once the anti-cryptography law is enforced, government agencies in Australia will be able to issue the following three types of notifications.
Technical Assistance Notices (TAN: Technical Assistance Notice): Forced notification to use the cryptic interception function of the communication aid agency
Technical Capability Notices (TCN): Forced notice to make communication provider build new cipher interception function
Technical Assistance Requests (TAR: Request for Technical Assistance): any request that secret provision is applied, but not criminal punishment or civil penalty
Chris Carnan, a lecturer at the University of Melbourne's Department of Computing Information Systems said, "Anti-cryptography laws contain two mandatory notifications and voluntary requests, and forced notice is attracting attention, but spontaneous The request is the most dangerous thing ". According to Mr. Carnan, there is the danger that "TAR has no restrictions similar to the two compulsory notices the government agency seeks and there is no need for an annual report", so what kind of interception of communication It points out the point that it is unclear whether it will be done.
Government stated that anti-cryptography does not create encryption backdoor, but it is intended to create a framework to provide access to endpoint devices, Mr. Carnan This law also points out the possibility of creating backdoor for various communications.
Also, although the anti-encryption method is applied to the Australian telecommunications provider, its definition is "to provide electronic service with one or more end users in Australia", so access from Australia It is possible that all possible websites are eligible. About this, Mr. Carnan writes that "This is an incredibly broad category, its legitimacy is unknown."

by Taras Shypka
This anti-encryption method was approved by the Australian Congress on Thursday, December 6, 2018. As the voice of criticism from the Australian Labor Party "criticized as inappropriate" gathered, the bill was temporarily withdrawn, but the bill finally passed by the Labor Party through the Congress . According to Christian Porter, Australian Attorney General, he said, "I agree to consider the bill (with the Labor Party), but I did not agree with the revision."
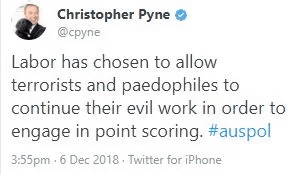
In response to criticism from the Labor Party, Defense Minister's Minister Christopher Pine said on his Twitter, "The Labor Party will continue to do wrong in order to capture votes from terrorists and pedophiles (not accepting anti-cryptography laws I was allowed to do "). The tweet has already been deleted at the time of writing the article.
Labor Party Tim Watts said, "We are not solving the problem with this bill, there is a possibility that it will be difficult to conclude a mutual legal aid agreement, and furthermore," CLOUD law on providing data from overseas providers " The problem we already face may be even more challenging, "he points out that it is a problem that law revisions are carried out with the problems associated with the anti-encryption method intact I will.
Related Posts:
in Security, Posted by logu_ii