Government agencies and companies found out the risk of hacking from 'FAX' with zero security measures

Millions of companies are at risk of cyber attacks because they are using an unsecured fax line, and two researchers are at the security conference " DEF CON " held in Las Vegas Announced. Yaniv Balmas and Eyal Itkin of Check Point Software Technologies, who announced the investigation, had not changed since the fax protocol was standardized in the 1980s, and "no security measures are embedded at all" And point out the problem.
Faxploit: Sending Fax Back to the Dark Ages - Check Point Research
https://research.checkpoint.com/sending-fax-back-to-the-dark-ages/
Malicious faxes leave firms 'open' to cyber-attack - BBC News
https://www.bbc.com/news/technology-45083774
You can check how the fax attack is done from the following movie.
Hacking the Fax - Ground Breaking New Research in Cyber - YouTube
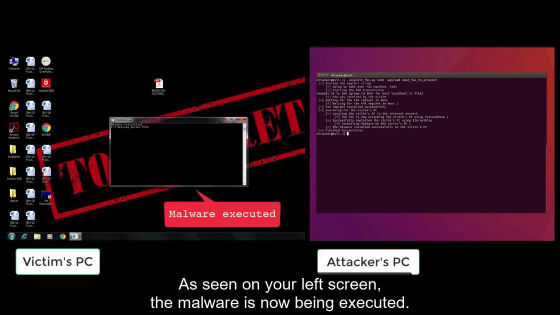
First, the script is executed on the attacker's PC on the right side of the screen. On the left side are victims' complex type printer & FAX.
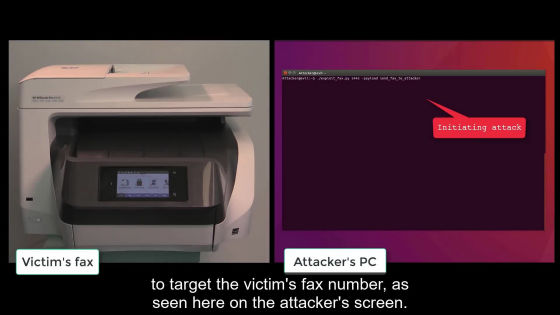
A malicious fax is sent to the victim ... ...
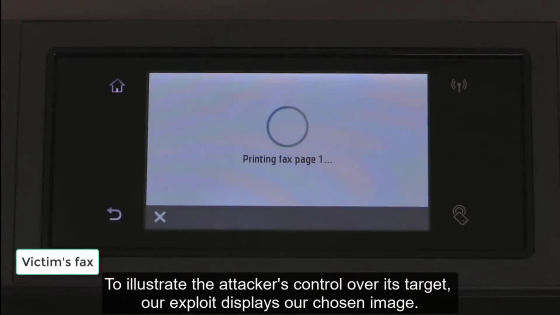
FAX is hacked.

After that, an attacker uses an intra-organization network to locate the target PC.
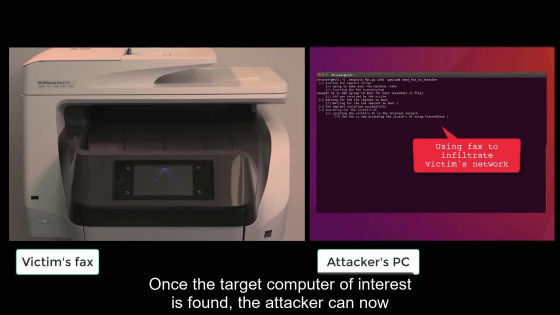
After finding the target, we started attacking using the attack tool "EternalBlue" that spreads Ransomware "Wanna Cry" that shook the world in 2017.
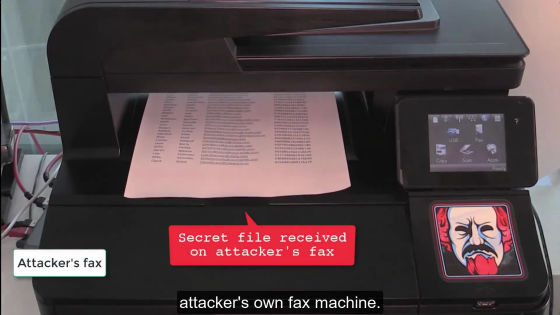
And then find the target file ......
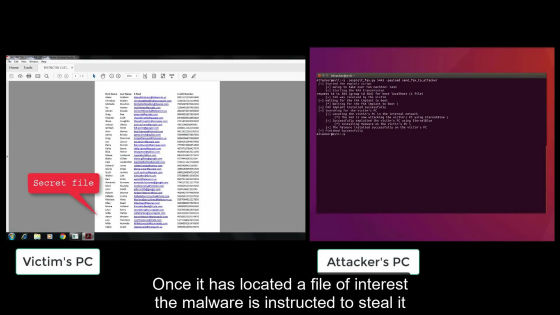
It sends a file to fax at hand and prints it.
Researchers say that millions of organizations such as government agencies and companies are using such faxes. In legal agencies fax is considered "visual evidence", but e-mails are not visual evidence. Therefore, despite the history that government authorities are using FAX, Balmas comments on the current situation that many organizations, government agencies, banks, etc. still use faxes.
The fax protocol has not been changed since it was standardized in the 1980s. There are possibilities that multiple people and organizations can attack in various ways using this protocol. Researchers point out the problem of protocols used especially for HP's multifunction machine, and HP seems to be working on a problem to deal with loopholes.
However, it is said that no evidence has been found that a malicious hacker has broken through a network protected using fax at the time of article creation.
Related Posts: