Fearful multifunctional malware "everything shop" that has the possibility of physically destroying the infected smartphone appeared

"Trojan.AndroidOS.Loapi" of a malware targeting a newly discovered Android keeps showing a series of advertisements without end,Distributed Denial of Service attack(DDoS attack), as an end terminal for sending a text message to an arbitrary number, secretly subscribing to a paid service, and perform many malicious attacks. Such "Trojan.AndroidOS.Loapi" is a terrible thing that there is the possibility of destroying a physically infected smartphone.
Jack of all trades - Securelist
https://securelist.com/jack-of-all-trades/83470/

Currency-mining Android malware is so aggressive it can physically harm phones | Ars Technica
https://arstechnica.com/information-technology/2017/12/currency-mining-android-malware-is-so-aggressive-it-can-physically-harm-phones/
"Trojan.AndroidOS.Loapi" is a malware hidden in applications distributed through third-party app store, browser advertisement, SMS-based spam, etc. Applications containing malware are likely to be popular anti-virus solutions and applications of famous pornographic sites.
Image of application icon including "Trojan.AndroidOS.Loapi"

When the installation is completed, the application will try to access the administrator authority of the device. The request screen is repeatedly displayed repeatedly until the user agrees. "Trojan.AndroidOS.Loapi" seems to confirm whether or not the device got root privilege, but this right is not used and it seems that it will not be used, "In the module added in the future (authority) There is no doubt that will be done. "
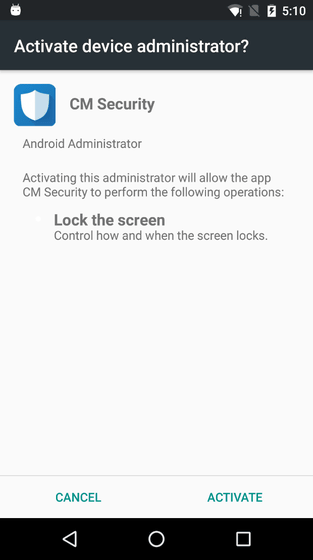
Furthermore, if you acquire the administrator's privilege, it seems that the installed application does not display an icon or disguises its behavior in an anti-virus application.
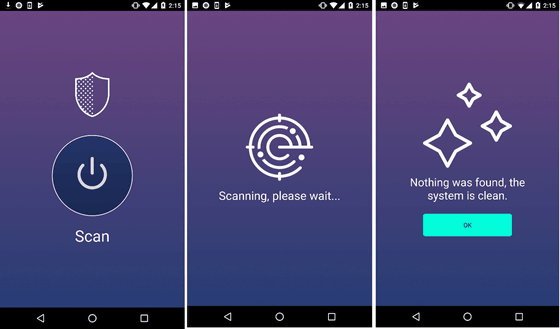
Kaspersky researchers who develop security wear, from the point that "Trojan.AndroidOS.Loapi" can set off various attacks too much, "Jack of all trades (Anywhere store)"We name it. This malware has less mining resources than bit coin (Bitcoin) "virtual currency"MoneroIt also includes a function to mining, and the person who created the malware can obtain the virtual currency mined by the infected smartphone.
Even though Monero's mining resources are small, it does not mean there is no burden on smartphones infected with malware. When Kaspersky researchers actually experimented with a smartphone infected with "Trojan.AndroidOS.Loapi", it seems that the battery of the smartphone swelled and the casing was deformed after two days.

Popular site uses the number of accesses and virtual currency mining with viewer's CPU powerWe are hoping for mining virtual currency as a new source of income instead of advertising. But,A method to continue mining the virtual currency even if the browser is closed by borrowing the PC resource of the website visitor secretlyThere are cases in which mining of the virtual currency is carried out secretly without informing the user, such as appearance. Note that Sophos, a software developer, uses the CPU resources without user consent The virtual currency mining tool is "It is malware"We formally classify it.
"Trojan.AndroidOS.Loapi" is extremely troublesome malware even without the virtual currency mining function, it can also be registered with an expensive paid service, and by sending an SMS message or using an infected smartphone It is also possible to launch a DDoS attack. In addition, it is also possible to receive a list of security-related applications that may harm malware via the C & C server, and if the user installs or launches the application contained in this list, it will be displayed on the smartphone screen as "Malware We detected that "Trojan.AndroidOS.Loapi" has been invalidated by displaying a false notification saying "Trojan.AndroidOS.Loapi" has been detected. Note that this notification will be displayed repeatedly until the user agrees and deletes the application.
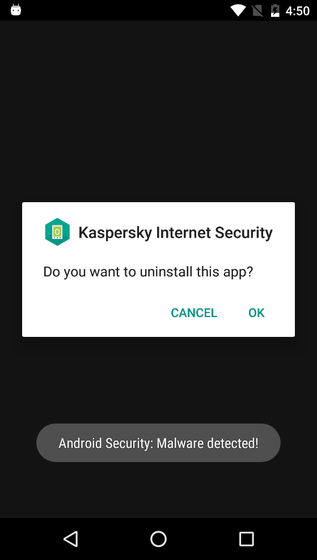
Kaspersky says, "I have never seen malware that can launch all such attacks so far."
Related Posts: