Security researchers noted two-factor authentication of Apple ID and defects of "searching for iPhone"

ByWarren R. M. Stuart
In recent years, all services are required to create new accounts and cooperate with accounts of famous services such as Google and Twitter. Some services store very important private information etc. Depending on the service, it is very important to increase the security of the account, but it will be more secure to operate the account "2 step verification"Has been introduced by many services. Apple ID used when using Apple's iPhone, iPad, Mac, etc. also has two-step authentication, which is "Two factor authenticationAlthough it is called "Kapil · Haresh of security researcher pointed out the defect that this is a problem.
I was violated, digitally. - Medium
https://medium.com/@kapilharesh/i-was-violated-digitally-d3ea2b290e3a
There are limits to 2FA and it can be near-crippling to your digital life | Ars Technica
http://arstechnica.com/security/2016/07/there-are-limits-to-2fa-and-it-can-be-near-crippling-to-your-digital-life/
Graduate students who are majoring in cryptology and are studying about security privacy, software engineering, human-computer interaction, etc. are arguing that "There is a limit to existing Apple's two-factor authentication (two-step authentication) Kapil · Haresh. Mr. Haresh notices that cyber attack that Mr. Harech himself encountered on July 24, 2016 notifies that Apple ID 2-step verification is not functioning sufficiently "search for iPhone".
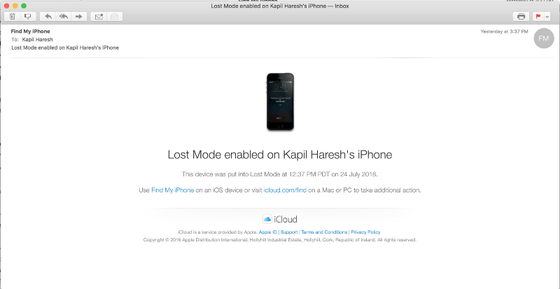
Immediately after receiving a cyber attack on July 24th, a notice of "Find My iPhone Alert (warning sound of searching for iPhone)" appears on the lock screen screen of Mr.Haresh's iPhone, and at the same time a warning beep sounded It was.
When viewing the situation of the iPhone at that time by "Search for iPhone" it seems that it was like this.
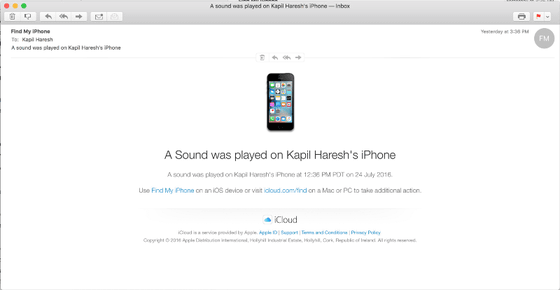
One minute after the warning beep sounded, the notice that "iPhone search warning sound" displayed on the lock screen of the iPhone switched, the screen became dark, and "Hey why did you lock my iPhone haha. Call me At (123) 456-7890. (Hey, why did you lock my iPhone, please call me at (123) 456-7890) "Notice was displayed.

The moment I saw this notification, Mr. Haresh said he understood that his iPhone had undergone a cyber attack. It is unknown where Mr. Haresh's Apple ID leaked from, but the attacker tried to hack Haresh's Apple ID, and since that failed, he used the "find iPhone" to lock the device . When iPhone is in lost mode, you can search the physical location of the terminal by using "Find iPhone". Note that this methodTragedy happened to the reporter of WIREDIn the case of a WIRED reporter, the data on the terminal is eventually deleted.
When a WIRED reporter got hacked in 2012, Mr. Haresh introduced 2-step verification in order to keep its own Apple ID more secure. 2-step verification is a perfect function to overwhelm a user trying to log in to an account illegally, and it is a system which is introduced in various services such as "Search for iPhone", "Apple Pay", "Initial setting of Apple Watch" is. However, in "searching for iPhone" 2-step verification does not work well, Ms. Haresh.
If you lose your iPhone, you can use "Lost Mode" in "Search for iPhone" to display a message to the person who locked the terminal and picked up iPhone, and iPhone data It is possible to delete all. This is a function that can be used without an 2-step authentication code even with an Apple ID that sets 2-step authentication.
Then, locate the terminal from 'Find iPhone' ...
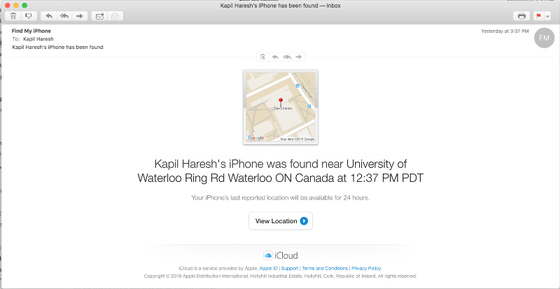
It is also possible to lock the terminal and send a notice. It seems that the attacker used this to display a notice called "phone hobby" on Hareush's iPhone.
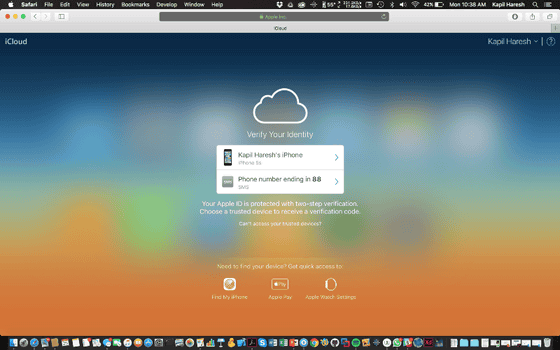
When using 2-step authentication with Apple ID, first register one or more trusted devices. A trusted device is a device that is under the control of a user and is a device that can receive 4 digit code using SMS or "Search for iPhone." However, when using "Find iPhone" it seems that you could not ask for this 2-step verification code, which is the only problem with "looking for iPhone" and a flaw in 2-step authentication of Apple ID, Mr. Harech.
Haresh says he has used Apple products for the past ten years, but he says he will be confident about the security aspects of Apple products in the future. At the same time, being able to carry out the attack like this time says "It is really terrible if Apple thinks that it gradually focuses on the cloud."
Coincidentally Mr. Haresh was a graduate student majoring in cognitive science, so I knew how to deal with such attacks, but it is not always the case that general users have such knowledge. Mr. Haresh has never taught someone a password for his Apple ID and says that the password is a secure one mixed with uppercase and lowercase letters. Also, I never entered a password for Apple ID on a dangerous site. It is unknown how an attacker knew the password of Mr. Haresh's Apple ID, but the important thing is to minimize the damage when a password leaks out. In that respect, it was very dangerous to say that all the data in the terminal might have been deleted, so Apple should make corrections on this point, Ms. Haresh.
In addition, Mr. Haresh claims that it may have been able to prevent such illegal login by "mail login notification" function. When Apple logs in to Apple ID from outside of the country, the following notification will be sent to the registered mail address.
The following e-mail notification when e-mail was sent when I logged in to Apple ID when I lived in Canada. You can read the word "Apple Canada" in the red frame.
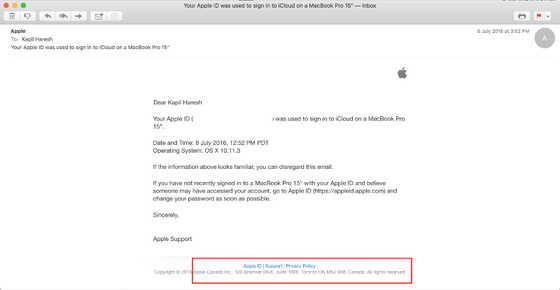
And when logging in from another area, you can see that the sender of the mail is different as follows.
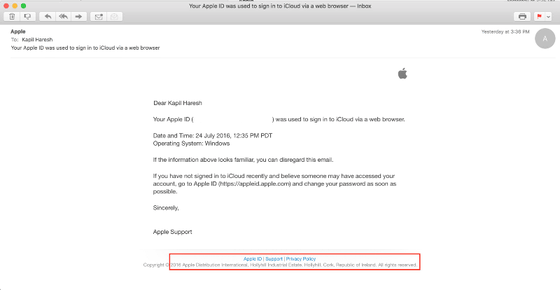
In this way Apple notifies you by e-mail when users log in to Apple ID from a different region, and is aware of which region you are accessing Apple ID from. It seems that an attacker who attacked Haresh has logged in to Apple ID from Ireland. Also, it seems that attacker logged in to Apple ID from Windows terminal instead of Mac, but Mr. Harris said he rarely logged in to Apple ID from Windows. Therefore, if you carefully monitor such login related information, it may have prevented hacking by an attacker, Ms. Haresh.
Mr. Haresh commented that it is ideal to check whether Apple is legitimate login. Also, in fact, at Microsoft, when trying to log in to an account with a new device or detecting an operation to try to log in to an account other than a terminal normally used, it is necessary to lock the computer and confirm the user is correct access, It seems to introduce the function called.
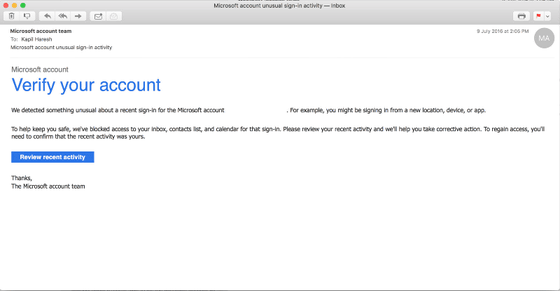
Related Posts:
in Security, Posted by logu_ii