A backdoor is found in China Baidu's SDK, popular applications with a fatal vulnerability are summarized

China's search boss "Baidu" software developer kit (SDK) "Moplus"And a backdoor is installed in the application using Moplus, without sending data inside the terminal to the outside without permission, installing the application, adding contacts, sending SMS It turns out that there is a fatal vulnerability that you can do whatever you want by remote control.
A vulnerable software development kit "Moplus", in fact, the implementation of the back door function turned out | Trend Micro Security Blog
http://blog.trendmicro.co.jp/archives/12540
Baidu's SDK "Moplus" hasPointed out the existence of a vulnerability called "Wormhole"It was done. However, when security company Trend Micro analyzed Moplus, it turned out that backdoor was installed in the SDK itself apart from Wormhole.
According to Trend Micro, Moplus's vulnerability automatically sets the local HTTP server as the terminal when the user starts the application, continues to wait at the TCP port, analyzes the message sent from the outside and analyzes its own task It is called a typical command & control (C & amp; C) attack model. Unlike traditional C & amp; C attacks, it seems that there is a feature that the server is on the user side and the attacker can exist anywhere.
By exploiting the backdoor of this C & amp; C attack model, an attacker can remotely collect personal information such as user's location information, search box information, package information, add contacts to the terminal, download You can manipulate the user's terminal at will by searching files that have been made, uploading specific files, calling from a remote place, sending fake SMS, installing arbitrary applications, etc. It is possible.
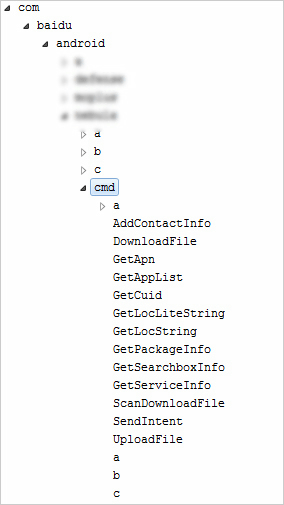
Trend Micro dared to reproduce with Nexus 6 equipped with Android 6.0. When Baidu Map was launched, I confirmed that an unauthorized service "bdservice_v1" always works in the background and that contacts are added to the terminal.
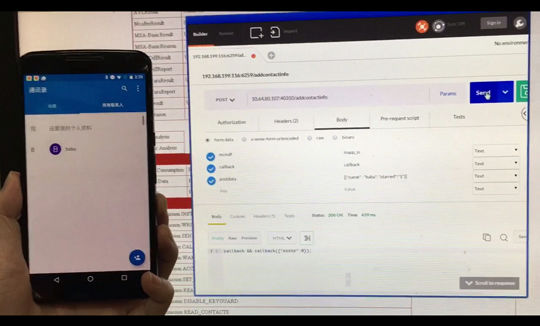
Since the HTTP server set by Moplus does not perform identification and authentication, any application developers can attack them remotely if they know the TCP port number. An attacker can simply do cheating from any place simply by sending an HTTP request. For this reason, Trend Micro said, "Moplus's backdoor has given terror to Android users around the worldVulnerability "Stagefright"It may be more malignant than ", I am evaluating.
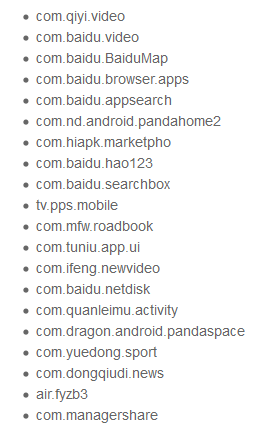
According to Trend Micro, there are only 14,112 applications that incorporate Moplus, 4014 of which are official applications of Baidu. The top 20 popularity of Moplus applications is as follows, with Chinese made applications such as "QiYi", "Baidu video", "Baidu Map", "Baidu browser", "Baidu app search", "PandaHome 2.0", "hao 123" It is caught.
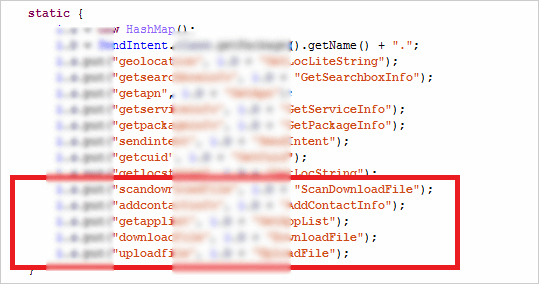
Trend Micro has reported the existence of Moplus's backdoor to Google and Baidu, Baidu said "Since 30 October 2015 we have addressed this vulnerability, have submitted updated apps to Google Play, pending Some of them have already been approved except for those of 'I'm getting approval'. And in the "8.7.5" version of Baidu Map, it seems to have confirmed that the code has been changed so that it will not be executed. However, deleted from Moplus is only the function surrounded by the red frame, and it is confirmed that there is still an illegal command.
Incidentally,Baidu Japan CorporationOn the top page and official Twitter "Baidu Headquarters (China) developed some SDK" Moplus "news reports, but this SDK is used for" Simeji "provided by our company (Baidu Japan corporation) We are not announcing.
SDK developed by Baidu head office "# MoplusThere were some reports on ""Baidu (Japanese corporation) provided by"#SimejiAbout this SDK is not used.
- Simeji (Japanese input keyboard) (@ Simeji_pr)2015, November 9
· Additional notes November 13, 2015 18: 42
Baidu Japanese corporation denied the use of "MoPlus" which became a problem in "Simeji" provided by Baidu Japanese corporation, but according to the blog "Windows 2000 Blog" posting technical information, "Simeji privacy Lock "and other Shimeji applications, it turned out that" MoPlus "charged with back door was used.
[Sad news] Discovery that cooperation processing with MoPlus is found in Baidu Simeji application which advertisement became a problem in August - Windows 2000 Blog
http://blog.livedoor.jp/blackwingcat/archives/1916023.html
In response to this, Baidu Japan Corporation immediately takes action to delete the corresponding application from Google Play.
@ BlackWingCat@ Mitsuaki_iIt is Baidu Japan. Thank you very much for your report. The app pointed out was deleted from Google Play at 12:50. The circumstances and details are currently under investigation. We will report it as soon as I know the details.
- Baidu_Japan (@ baidu_ japan)2015, November 13Related Posts: