Clearly the existence of a vulnerability "Certifi-gate" that can damage millions of Android terminals

"In the Las Vegas"Black Hat USA 2015"According to Check Point of security software company, vulnerability affecting Android terminal of several million units"Certifi-gate"Was reported. this is,"Stagefright" revealed at the end of JulyAnd another vulnerability, the range of influence is large, even if you can not relieve even the terminal you just bought, be careful.
Certifi-gate: Hundreds of Millions of Android Devices Could Be Pwned | Check Point Blog
http://blog.checkpoint.com/2015/08/06/certifigate/
Your Android Is Pwned and There's Nothing You Can Do About It | News & amp; Opinion | PCMag.com
http://www.pcmag.com/article2/0,2817,2489195,00.asp
"Stagefright" was a vulnerability related to the media player framework, but "Certifi-gate" reported by Check Point is a vulnerability related to mobile remote support tool (mRST) used by terminal manufacturers and network service providers.
MRST is a tool that allows you to grasp what the screen of the terminal is currently and to operate the target terminal remotely by combining it with a system level plug-in by a third party, It is intended to solve the problem by support personnel operating the terminal remotely when receiving it. However, since mRST has privileges such as character input and application installation, if it is exploited, it is possible that the user's personal information is stolen or an operation which originally can not be done by the user of the terminal may be performed.
It is only necessary to delete mRST and plug-ins, but third-party plug-ins are read from the beginning, they are built by network service providers and manufacturers from the beginning, and it is impossible to delete them It makes it difficult.
Check Point's demonstration is like this. The attacker 's terminal is that the screen in the browser written as "Certifi - gate Demo" on the left side is opened by the user' s terminal, and the right side is opened in the separate window.
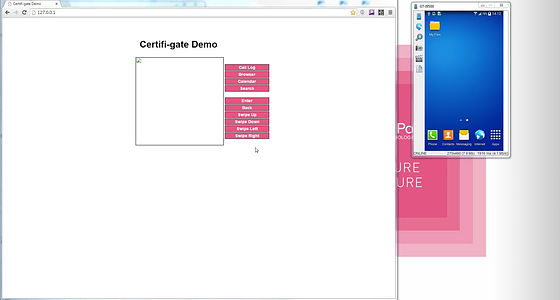
An attacker is installing some applications.
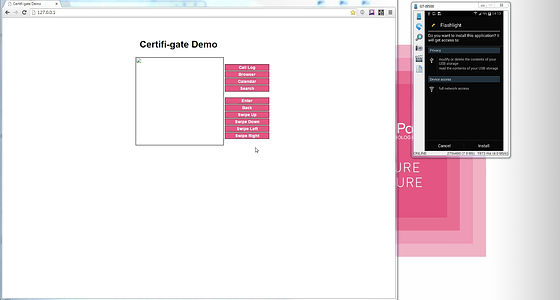
It seems that it was an application to turn on the light, and a button for lighting both the attacker side and the user side was displayed.
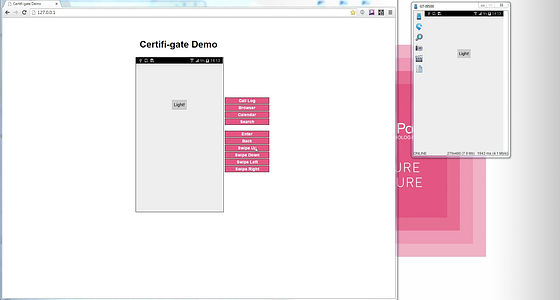
The home screen is mirrored like this.
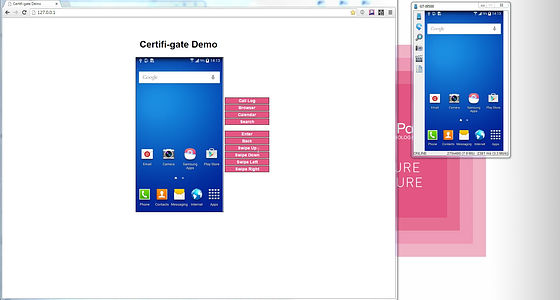
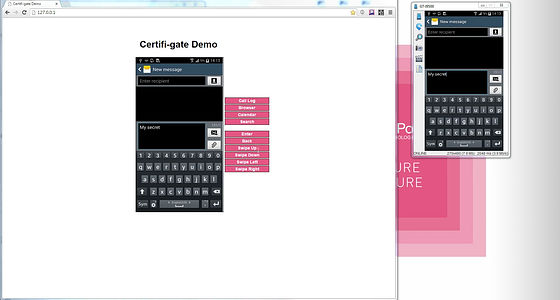
If you have created an email ......
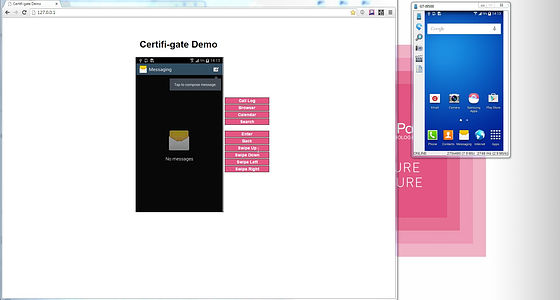
Even if the contents are confidential, it goes to the attacker.
Also, when the attacker displays the call history ......
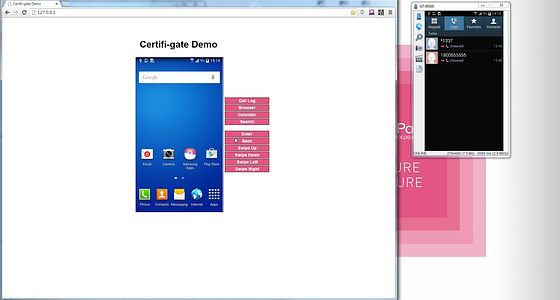
Similarly on the user's terminal to the call history screen. There is a story saying that the smartphone that was put in a pocket or a bag was unlocked by some kind of smile and was in a call state without permission, but that is not the case.
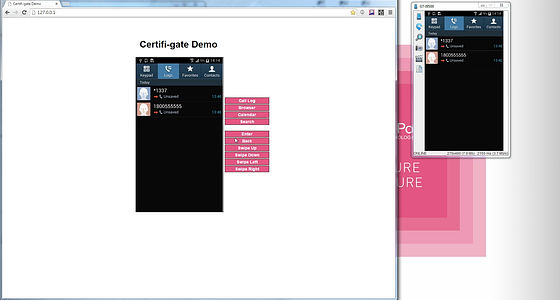
According to Check Point, the influence range will be several million units on the Android terminal. Since vulnerabilities exist regardless of the old and new terminal, Check Point has published Certifi-gate Scanner on Google Play for those who want to check if their terminal is safe.
Certifi-gate Scanner - Android application on Google Play
https://play.google.com/store/apps/details?id=com.checkpoint.capsulescanner
In addition, vendors of this affected terminal, Google etc. are informed as of April, and some companies are starting to distribute updates sequentially.
· 2015/08/26 12:22 Additional note
Anonymous data analysis for users who installed "Certifi-gate Scanner" revealed that the application using "Certifi-gate" was on Google Play.
Certifi-gate Found in the Wild on Google Play | Check Point Blog
http://blog.checkpoint.com/2015/08/25/certifigate-statistics-exploitation-mitigation/
I found that the application called "Recordable Activator" has been downloaded from 100,000 to 500,000 on Google Play. Since it was deleted from Google Play as of August 26th, there is no fear that it will be installed by mistake.
As a result of data analysis by the Check Point research team, Certifi-gate was not found on 42.06% of terminals, 42.09% is a vulnerable terminal, 15.84% is a terminal installed vulnerable plug-in He said that. Looking at each terminal manufacturer, Sony Mobile has a safe terminal as a whole 98.98%, Samsung has 66.68% vulnerable terminal, HTC 85.62% vulnerable terminal, LG is The vulnerable terminal was 19.03%, but 72.36% of vulnerable plugins were in the terminal.
Related Posts:
in Mobile, Posted by logc_nt