Hacker's matching site "Hacker's List" that I want work with someone who wants to hack
Even if there is an "opportunity" that you want to ask a hacker who can control your computer as you want, the means to actually contact a hacker is not so easy to roll. Site started in 2014Hacker's List"Has become a matching site that connects hackers with such hackers.
Hacker's List | Find a professional hacker | Home
https://hackerslist.com/
When you visit the site, there are straight items such as "Find Hackers" (search for hackers) and "Bid Projects (bid on the project)" at the top.
When you click "Bid Projects", a list of items you want to hack is displayed. Try clicking on a project written as "University" ......
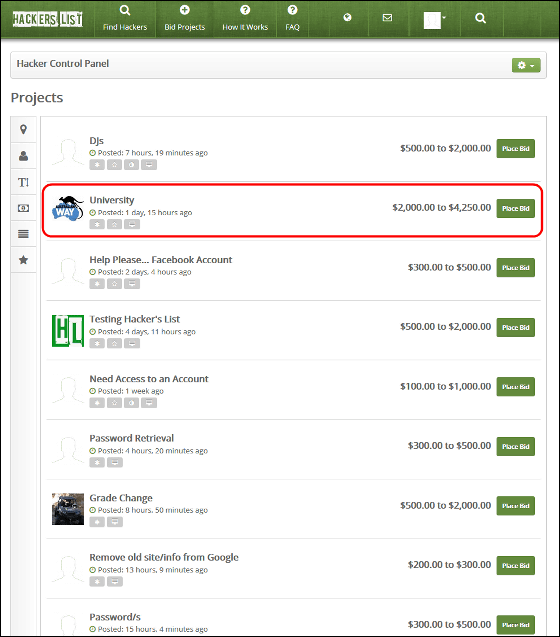
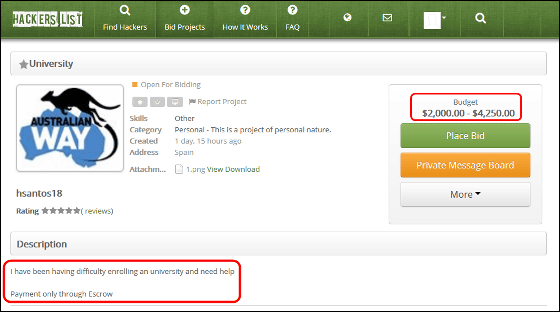
The details of the opportunity was displayed.

The content of the request is stated at the top of the screen. In the "Description" column, "I can not enter the university for a long time, so I need help, the urgent need of payment through escrow service". In the upper right "Budget", it is displayed as 2000 dollars to 4,250 dollars (about 240,000 yen to 500,000 yen), so you can see the payment fee paid when the case is successful.
Under "Bid (bid)" below that, the bid from the hacker is displayed. In the comment, I will ... (I will do it) and "time depends on your requirements / problems. (Required time depends on request / problem)" "If you want to hear more details, A comment such as "Ne" is given.

Also, the bid amount that each hacker decided by himself is displayed. People who put the lowest price like auction format do not get work, but eventually it may be the point that they become the client's choice.

As mentioned above, in the Hacker's List, payment of remunerationEscrowYou can use the service. Hacker's List seems to be guaranteed a certain degree of credibility because there is a provision that becomes a violation of the law when operating the service unauthorized if high credibility is required to provide escrow service in the United States .
Looking at the contents of other requests, "I want to access a Facebook account without resetting the password, I understand the account's email address and URL" ... ...

"GPAWe want the grades of the university to change grades so as to improve the score of the grading system (grading system widely introduced in Europe and the United States) ". In the comment column of the bid, "You can rewrite grades by accessing the database, with Skype in details", you can also see the interaction that you might think "Out!" Without thinking.

I also thought that "I want you to find out where the images come from and permanently delete the data from multiple sites", a request to make you feel urgently felt even written.

There are some ways to catch the word "hacking", and it is somewhat easier to say that it is somewhat premature to make it "hacker = criminal". The original "hacker" was a word that praised excellent computer engineers, but as time went on, there was a history that the image of "a person who criminalizes a computer by criminalizing a computer" has spread. Even now, the event "DEFCON", an interactive hacker as the original computer engineer, is held every year, and it is an event that gathers more than 10,000 visitors.
Documentary image of world's largest hacking event "DEFCON" is now on YouTube - GIGAZINE

In the column of the profile posted to the site posted on the site, it was stated that "moral professional hacker" and "I registered for the sake of money and in case of appropriate" It was.

This Hacker's List was launched around October 2014, and about 500 requests have been received at the time of article creation. It seems that the exciting service content "hire a hacker" seems to be talking about in the United States, and it is also taken up in the media such as the New York Times.
Need Some Espionage Done? Hackers Are for Hire Online - NYTimes.com

It is still unknown how it will be deployed in the future, including legal issues, because it is a service just started. In the first place, the question arises as to whether hackers with high computer skills will do the job of finding jobs looking for on such an open site, but it is not easy to find a service that seems to be interested in how to change and develop It was becoming.
Furthermore, acts such as unauthorized access to a computer without access authority, rewriting data, etc.Unauthorized Computer Access Prohibition ActYaComputer fraudThere are times when you may touch laws such as, so it is better to keep it in mind, just in case.
Police Agency cyber crime measures: laws and ordinances

Related Posts:
in Web Service, Posted by darkhorse_log