What is the actual situation of the market price at the "underground market" where the leaked personal information is traded?

ByOriol Domingo
It is no exaggeration to say that the Internet can no longer be separated from information leakage due to hacking damage, money and property damage, even large companies like Sony PicturesA situation where an employee's family is threatened by cyber attacksI have encountered. Data leaked by hacking is sold under water and passed from the hands of those seeking information to hands,DellPublishes data summarizing the quotations of information flowing in "underground market" by such hackers.
The Underground Hacking Economy is Alive and Well | Dell SecureWorks Security and Compliance Blog
http://www.secureworks.com/resources/blog/the-underground-hacking-economy-is-alive-and-well/
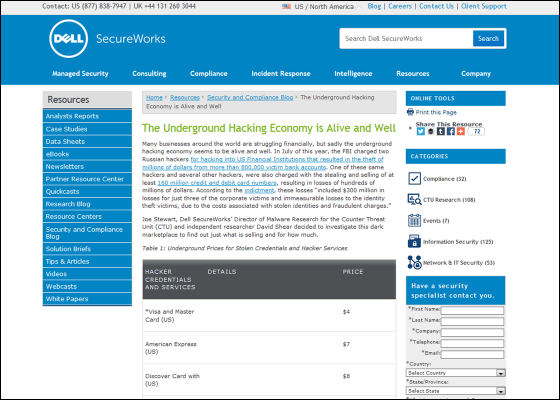
◆ Price information of hacked information · Card information etc.
Credit card information is the most frequently abused case among personal information. It seems that the market is trading at a price of about 1,000 yen to 2,000 yen per case. (In the text: US = USA, CAN = Canada, UK = UK, AUS = Australia, EU = European countries)
· VISA / Master card (US):Four dollars (about 480 yen)
· VISA / Master card (UK / AUS / CAN):7 to 8 dollars (about 830 yen to 940 yen)
· VISA / Master card (EU / Asia):$ 15 (about 1770 yen)
· American Express Card (US):$ 7 (about 830 yen)
· American Express Card (UK / AUS / CAN):12 to 13 dollars (about 1240 yen to 1350 yen)
· Discover card (US):8 dollars (about 940 yen)
· Discover card (AUS / CAN):$ 12 (about 1420 yen)
· Discover / American Express Card (EU / Asia):$ 18 (about 2120 yen)

BySean MacEntee
There are also cases where you sell the data itself stored on the magnetic tape part of the card. The magnetic tape is divided into three invisible lines (tracks), and authentication information such as account number, expiration date, cardholder's name, etc. are stored on the first and second tracks.
· First and second track information (US):$ 12 (about 1420 yen)
· First / second track information (UK / AUS / CAN):19 to 20 dollars (about 2240 yen to 2360 yen)
· First and second track information (EU / Asia):$ 28 (about 3300 yen)
In addition, information such as name, address, telephone number, e-mail address and the like that can identify individuals and information such as passwords attached to them are summarizedFullzInformation that is called also is subject to dealings. If Fullz is exploited, it will lead to damage such as creating a fake account at a place he does not know about.
· Fullz information (US):$ 25 (about 2950 yen)
· Fullz information (UK / AUS / CAN / EU / Asia):30 to 40 dollars (about 3540 yen to 4720 yen)
It seems that even the number of the bank account containing VISA authentication information, birthday information, and many deposits to enhance the safety of online payment is subject to buying and selling.
· Visa authentication (US):$ 10 (about 1180 yen)
· VISA authentication (UK / AUS / CAN / EU / Asia):17 to 25 dollars (about 2010 to 2950 yen)
· Birthday information (US):$ 11 (about 1300 yen)
· Birthday information (UK / AUS / CAN / EU / Asia):15 to 25 dollars (about 1770 yen to 2950 yen)
· Bank account number with deposit of $ 70,000 to $ 150,000 (about 8.3 million to 18 million yen):Below $ 300 (less than about 32,400 yen)
◆ Price list of hacked information: Hacking tools · Hacking proxy fee etc.
Not only the information leaked by the hacking as mentioned above, but also the tools used for hacking, the malware itself, and the service that carries out hacking acts are also being traded with prices.
· Computer information infected with malware 1000 information:$ 20 (about 2360 yen)
· Computer information infected with malware 5000 cases:$ 90 (about 1620 yen)
· Computer information infected with malware 10,000 cases:160 dollars (about 18,880 yen)
· Computer information infected with malware 15,000 cases:$ 250 (about 29,500 yen)
ByR3gular
·Remote Access Trojan (RAT):50 to 250 dollars (about 5900 yen to 299500 yen)
· Other add-on services accompanying RAT:20 to 50 dollars (about 2360 yen to 5900 yen)
·Exploit kit"Sweet Orange" Lease fee:$ 450 per week (about 53,000 yen) or $ 1,800 per month (about 210,000 yen)
· Web site hacking · Data removal fee (price depends on hacker's reputation):100 to 300 dollars (about 12,000 to 36,000 yen)
· Implementation of DDoS attacks:3 to 5 dollars per hour (about 350 yen to 590 yen)
· Implementation of DDoS attacks:90 to 100 dollars per day (about 10,600 yen to 11,800 yen)
· Implementation of DDoS attacks:400 to 600 dollars per week (about 47,000 yen to 71,000 yen)
· Doxing (Acquiring personal information of attack target through net, malware, etc. and publishing):25 to 100 dollars (about 2950 yen to 11,800 yen)
◆ What is the measure to prevent damage?
We encourage Dell to implement the following countermeasures at the organizational level and at the level of individuals, in order to protect ourselves from such "anything" hacking world.

ByAlan Dreamworks
· Organization / corporate measures
· Be sure to have a firewall to stop the damage in advance
·Intrusion Prevention System (IPS) and Intrusion Detection System (ISD), We prepare a system that detects and blocks transmission and reception of illegal information
· Host IPS itself
· Prepare the latest malware protection solution
· Scan system vulnerability
· We will monitor the system logs on a 24-hour basis, and prepare similar systems for web applications and networks
· Align the latest security-conscious staff
· E-mail encryption
· Thorough security education for employees. It is important to spread thorough security awareness such as not clicking mail URL even if the sender is clear.
· Measures to take at the individual level
· Use a computer that performs bank transactions independently from other tasks, making it separate from acts such as sending and receiving mails and surfing the web.
· Do not open URLs included in e-mails sent from unknown parties. Even if the sender is clear, it is desirable to confirm the contents to the sender before opening it.
· Collect the bank account information and credit card usage frequently frequently so that it can be discovered at an early stage even when illegal transactions are done.
· Keeping antivirus software up-to-date at all times is an effective means for defense.
· Anti-virus software should introduce "regular version", not "trial version". Since the trial version is mostly the case that the virus definition file is not up-to-date, it can be said that it is insufficient as a protective measure.
· When installing free software such as "○○ Download · Accelerator" or "Spyware Removal Tool", you should pay close attention. Also, do not download software from pop-ups such as "System is in danger" which may be displayed on website. This is because there are many cases where malware is hidden in the installed software.
Related Posts:
in Note, Posted by darkhorse_log