How to extract Gmail and Facebook passwords from Google Chrome's incognito mode

Google ChromeIncognito mode, The user name and password when logging in to Google or Facebook are not stored on the hard disk but are saved in memory. However, the function to extract data on this memory with one shot is password analysis software "Passware Kit"Was released in version 12.3 of the 12.3.
Passware Kit 12.3 Extracts Facebook, Google Passwords from Computer Memory; Improves ATI Acceleration and Distributed Password Recovery
http://blog.lostpassword.com/2013/02/passware-kit-12-3/
The screen below actually extracted the password from Chrome's secret mode. Gmail and Facebook passwords are easy to see, and the analysis time is only 3 minutes 6 seconds. In short, analysis is possible in a few minutes.
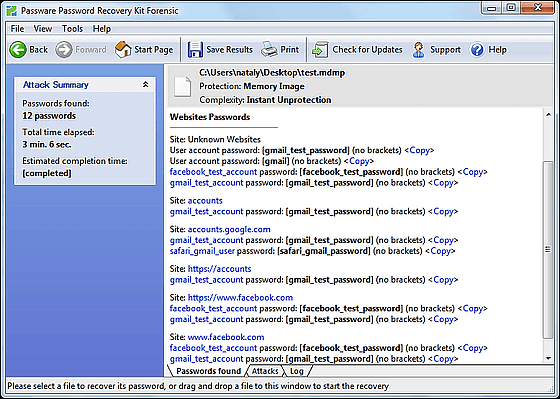
An explanation on what kind of mechanism has enabled such a thing to be done on official blog.
Extracting Facebook passwords from memory image or hibernation file
http://blog.lostpassword.com/2013/02/facebook-password-recovery/
First of all, it can be executed with Google Chrome's incognito mode, Ctrl + Shift + N key, and in incognito mode an icon like a spy is displayed at the upper left, no data is recorded on the hard disk of the computer. Many people use it when logging in using a personal computer, for example.
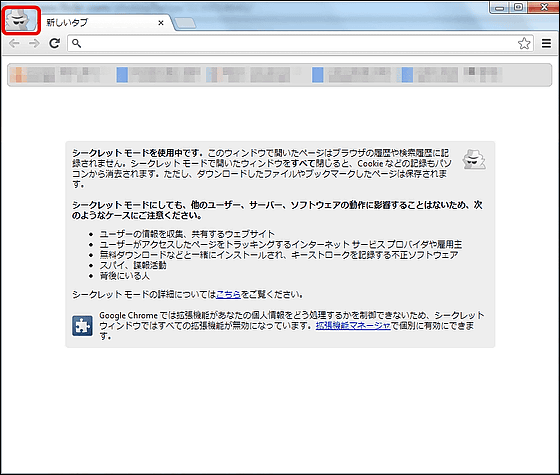
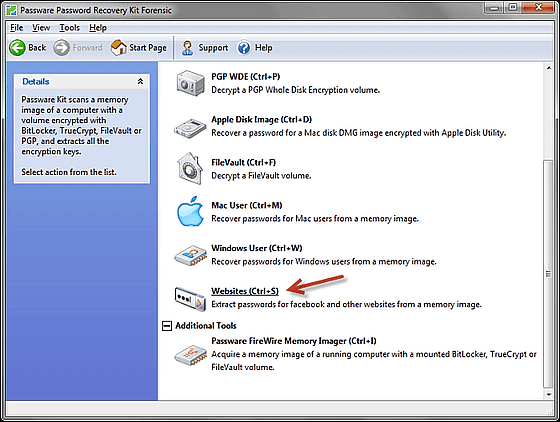
If you close Google Chrome from this state and put the computer in hibernation (hibernate), the data that was on the physical memory is saved as "hiberfil.sys" in the C drive. This file is locked by Windows, but since it can be opened with "Passware Kit", select "Websites" as it is.
Then the extraction of the password starts from the memory contained in the file ......
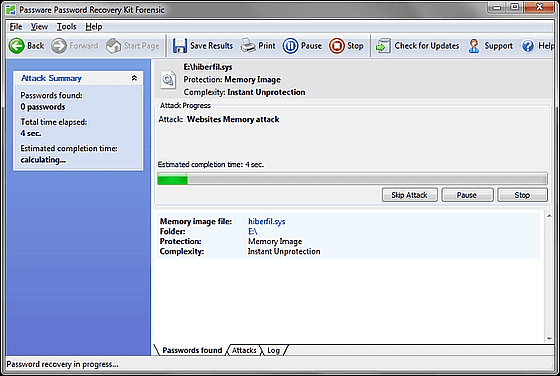
The password of each site such as Gmail and Facebook will be displayed in just a few minutes.

It is not so "as it is safe because it does not use hibernation", it is a higher version of "Passware Kit"Enterprise version(795 dollars, about 74,000 yen), you can imagine the memory of the computer you are booting from, you can extract it from the same procedure from there, so there is no blind spot.
Incidentally,Similar procedureIt is said that the password of the Windows user who is logged in with can be extracted from hibernation file and memory image of hibernation.
Related Posts:
in Software, Posted by darkhorse