Iesys.exe Reward of 3 million yen to the information about the perpetrator of the remote control incident by the National Police Agency

Remotely operated virusThe crime preliminary announcement by the police exposed policeman's proprietary writing under the white day, "the IP address is the same as the fingerprint, so even if it knows this, the criminal can be caught" the low level of recognition that the police were false charges About the information that leads to the arrest of the author of iesys.exe who revealed the fundamental thing, the National Police Agency finally decided to issue a 3 million yen reward, and announced it on the official website.
The information which was found by the investigation so far is also not helpful at all, but it is summarized, and police say "software that enables anonymization of Internet communication"TorBy using such as "You can identify the criminal like a fingerprint if even an IP address is known" As a result of being overturned, you can see how severe the police are being driven into.
"Advertisement on investigation special incentive (December 12, 2012) | National Police Agency
http://www.npa.go.jp/reward/contents37.html
The period of entry is from December 12, 2012 to December 11, 2013, and the following seems to be the characteristics of the criminal.
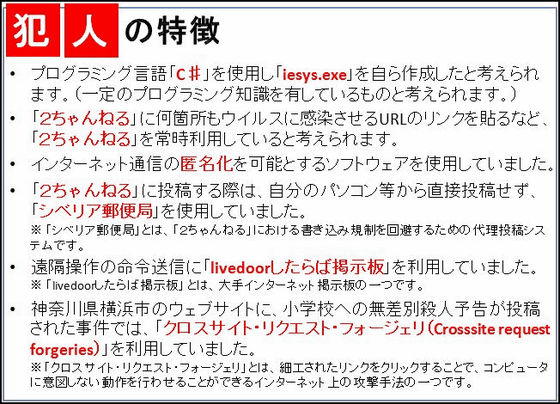
It is thought that you created "iesys.exe" by using the programming language "C #". (It is considered to have certain programming knowledge.)
· It seems that you are constantly using "2channel", such as attaching a URL link that infects viruses several times in "2channel".
· We used software that enables anonymization of Internet communication.
· When submitting to "2channel", I did not post directly from my personal computer etc, and I used "Siberian post office".
※ "Siberian post office" is a surrogate posting system to avoid write regulation in "2channel".
· We used "bulletin board if we livedoor" for remote control command transmission.
※ "If you livedoor bulletin board" is one of the major internet bulletin boards.
· On the website of Yokohama City, Kanagawa Prefecture, in the case where an indiscriminate murder notice to elementary school was posted, we used "Crosssite request forgeries".
* "Cross-site request forgery" is one of attacking methods on the Internet that allows you to perform unintended actions by clicking on a specially crafted link.
In addition, already the police have continued the investigation with its prestige, and in October it is said that the criminal statement e-mail is passing through the server of the United States and EuropeDispatch investigators to each country, In NovemberAsk FBI to analyze communication record, A suicide preliminary notice mail like the following is sent to every place concerned from the author iesys.exe as if to laugh at those behaviors.
【Remotely operated virus】 From the real criminal This time suicide notice mail - free book of satoru.net
Dear Ochiai
Hello DIG,
Hello TBS ****
Hello Asahi Newspaper ****
Hello Yano Sato
Hello ITmedia ****
Hello Fuji TV
long time no see. It is the real culprit.
I made a mistake. The game seems to be my defeat.
Since I do not want to be caught I commit suicide hanging from now.
It was a fun game.
goodbye. In the next generation -
Of course, the police also investigated these matters, but naturally it still arrived at the reward of 3 million yen this time in the situation that the iesys.exe author is still unknown. Perhaps, I think that it is truly stucky as soon as I do it already.
Also, if iesys.exe author is caught caught, but if we do visualization of the inquiries about the other side of this false case, that is "I was forced to confess what I was not doing" , Although it improves from the situation that anyone may be caught in a false accident much more than now it is why why he has not done anything at all, and those who forged counterfeit confessions eventually end up in a damn spot Whether it is pear, it is important to the movement of the police in the future.
Related Posts:
in Note, Posted by darkhorse