T-Mobile customers' call and text data is unencrypted and captured via home antennas

Security researchers at
(PDF file) Don't Look Up: There Are Sensitive Internal Links in the Clear
GEO Satellites
https://satcom.sysnet.ucsd.edu/docs/dontlookup_ccs25_fullpaper.pdf
SATCOM Security
https://satcom.sysnet.ucsd.edu/

In 2022, T-Mobile partnered with SpaceX's satellite internet service, Starlink, to announce T-Mobile Starlink , which will enable mobile phone service even in areas without internet access. Satellite communication users will not need any special equipment or devices; they will be able to communicate directly with the satellite using just a smartphone. Beta testing for T-Mobile Starlink began in February 2025.
SpaceX and T-Mobile announce plans to enable direct communication between mobile phones and Starlink satellites - GIGAZINE

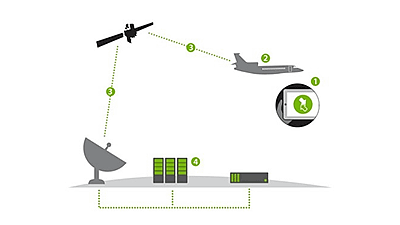
Satellite communication systems are considered to be at greater risk of being eavesdropped on than regular communications. Security researchers from the University of California, San Diego, and the University of Maryland, College Park, USA, jointly investigated the T-Mobile Starlink network. As a result, the researchers stated, 'T-Mobile's satellite communications were far more vulnerable than expected.'
The researchers first installed a satellite dish on the roof of a university building. This dish is almost identical to a commercially available home satellite dish, equipped with a motor that automatically changes its orientation to receive broadcasts and a TV tuner that captures television signals as data. Using this device, they scanned the 'transponders' of all visible satellites in the sky. The researchers report that they were able to create a program that 'analyzed the signal formats that differ from satellite to satellite and recovered the original internet communication data from the radio waves.'
The satellite data included voice calls and SMS from civilians, internet traffic from in-flight Wi-Fi and mobile networks, internal communications from businesses and government agencies, and data on critical infrastructure. Researchers also observed non-T-Mobile communications, including encrypted internal communications from ships, unencrypted portions of military systems including detailed tracking data for coastal vessel surveillance, and other law enforcement activity.

The paper cites two reasons why this large-scale data leak occurred. The first is cost. Enabling encryption incurs direct costs, such as additional license fees, and encryption also poses a risk of reducing the reliability of emergency services by making troubleshooting network problems more difficult. The second is the 'backhaul communication' format, which sends data from the edge of the communication network, such as base stations, to the core network. T-Mobile uses backhaul communication for communications in remote locations, and backhaul communication relays unencrypted satellite communications, meaning that information from users other than those intentionally using satellite communications could also be intercepted.
T-Mobile responded promptly to the research by encrypting communications. A T-Mobile spokesperson said, 'Last year, this investigation uncovered an encryption issue in a limited number of satellite backhaul communications from a very small number of base stations that was quickly fixed. While the issue was not network-wide, we are taking steps to ensure this does not happen again.' The researchers also stated that they have confirmed that several other carriers that received their reports have implemented countermeasures.
'We assumed that no one was going to go through all the satellites and scan them to see what was there, and that was their security approach,' said Aaron Shulman of the University of California, San Diego, who led the research team. 'We were shocked to find that the data being sent over the satellites was actually not encrypted at all.'
Related Posts:
in Web Service, Security, Posted by log1e_dh