China-developed AI cyber attack tool discovered, collects detailed location and IP addresses of IoT devices to find vulnerable devices
Security researcher NetAskari reported that he had 'discovered a prototype of a Chinese cyber attack tool.' The tool was designed to target IoT devices overseas, particularly Taiwan's communications infrastructure, and was even equipped with the ability to identify the location of the devices and vulnerable protocols.
The Prototype: AI driven cyber offense - NetAskari
NetAskari discovered a 2.3TB data dump extracted from Amazon CloudFront in the U.S. via the security search engine Censys. After tracing the source of the data dump, NetAskari discovered a Vue.js -based dashboard running on an NGINX server.
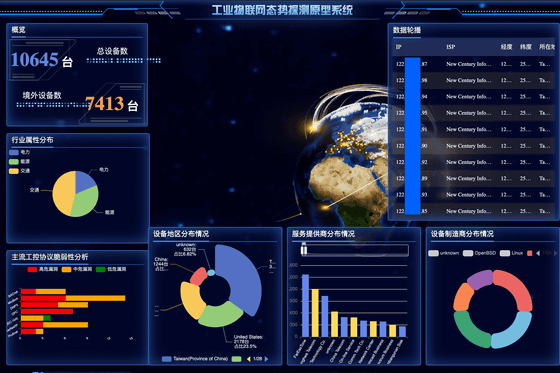
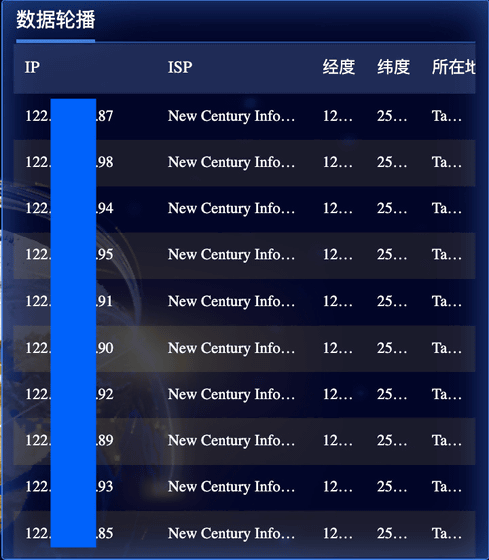
The dashboard was written in Chinese and displayed detailed information about the IoT devices in near real time, including their Internet service providers, IP addresses, latitude and longitude, etc. According to NetAskari, the majority of the devices displayed were IoT devices located outside of China, particularly in Taiwan.
It also included built-in indicators that could identify devices using common industrial communication protocols such as
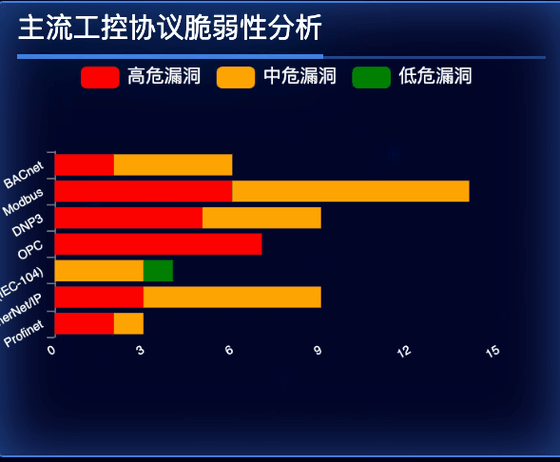
However, after NetAskari's investigation, he found that the dashboard retrieved static data via API once at launch and then repeatedly displayed it. In other words, although it appeared to be displaying real-time data, the dashboard was only displaying the contents of a pre-prepared data set. However, he also found that some of the IP addresses displayed were from real IoT devices in operation, so the data was not completely fake.
Further analyzing, NetAskari was able to access hidden menus and detailed design information of the dashboard from the behavior of the dashboard's user interface.
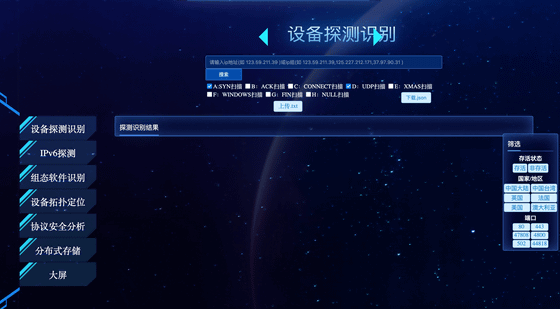
The hidden menu reportedly revealed a slide that described a workflow for acquiring and processing data from IoT devices. The workflow mentioned machine learning and demonstrated how AI can be used to identify targets and collect information.
Another slide explained how the system updates the target list after successfully infiltrating a device and how it uses landmark devices to pinpoint the physical location of IoT devices. This makes it clear that the tool is not just intended for external scanning, but also plans to infiltrate the target's network infrastructure and dig deeper to identify more vulnerable devices as it moves along.
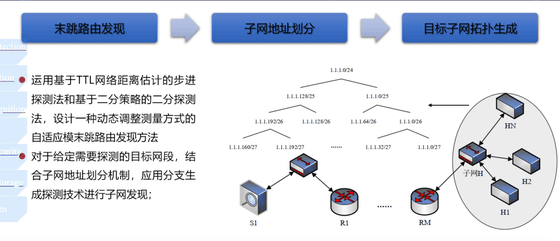
What at first glance appeared to be just a demo dashboard actually had a full-fledged design and information processing structure, leading NetAskari to conclude that the dashboard was not just a showpiece but a prototype for a real, operational tool.
NetAskari also concluded that the dashboard is likely not merely the result of a hobby or personal experiment, but a prototype for a full-scale attack tool developed as part of an advanced university research project or state-sponsored cyber operation. He also noted that China's offensive cyber capabilities are rapidly evolving, and warned that AI and machine learning will play an important role in future cyber warfare and intelligence gathering activities.
Related Posts:
in Security, Posted by log1i_yk