It has been revealed that some VSCode extensions have a malicious function that encrypts files and demands ransom

The code editor
VSCode extensions found downloading early-stage ransomware
https://www.bleepingcomputer.com/news/security/vscode-extensions-found-downloading-early-stage-ransomware/
The two ransomware extensions registered in the Visual Studio Code Marketplace are 'ahban.cychelloworld' and 'ahban.shiba'. According to overseas media Bleeping Computer, 'ahban.cychelloworld' was uploaded to the Visual Studio Code Marketplace on October 27, 2024, and 'ahban.shiba' was uploaded to the Visual Studio Code Marketplace on February 17, 2025.
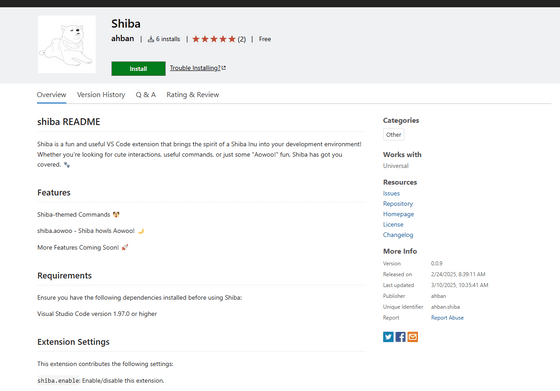
These extensions include the ability to use PowerShell scripts to download and execute other scripts from a remote server hosted on Amazon AWS. If the scripts are executed, they will encrypt files and display a demand that 'Your files have been encrypted. To recover them, pay 1
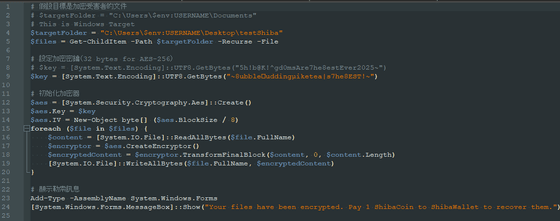
In addition, since this ransomware only encrypts files in the 'C:\users\%username%\Desktop\testShiba' folder, Bleeping Computer points out that 'it is clearly a ransomware under development or testing.'
The extensions were discovered by security firm ReversingLabs , who reported them to Microsoft, who then removed them.
We have reached out to the #VSCode marketplace team, & they have removed these extensions.
— ReversingLabs (@ReversingLabs) March 19, 2025
On the other hand, Italy Kruk, a security researcher at ExtensionTotal, criticized the attack, saying, 'When ahban.cychelloworld was first uploaded, it did not contain ransomware, but the ransomware code was added in version 0.0.2, released on November 24, 2023. We reported ahban.cychelloworld to Microsoft on November 25, 2024, but received no response.'
According to Bleeping Computer, 'ahban.cychelloworld' and 'ahban.shiba' had been downloaded 8 and 7 times, respectively, before being removed. Kruk pointed out that 'the number of downloads of these problematic extensions was low, so it's possible that Microsoft did not prioritize our reports.' In addition, Bleeping Computer said, 'The fact that the malicious extensions were left unattended for about four months indicates that there are serious shortcomings in Microsoft's review process.'
Related Posts:






